this week in security — december 7 2025 edition
THIS WEEK, TL;DR
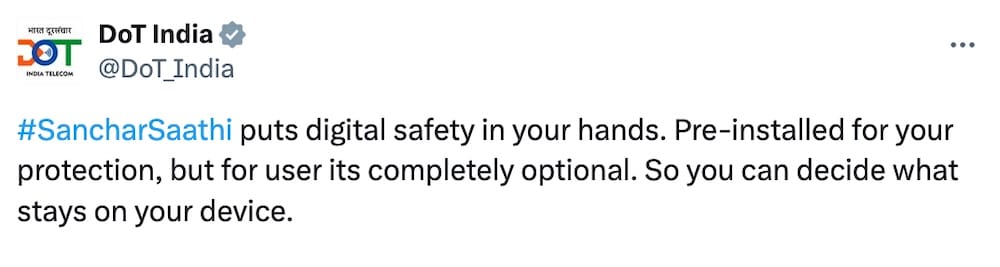
India backtracks after requiring citizens to install mandatory phone app
BBC News ($): We start this week in India following a week of controversy after the Modi government withdrew a mandate requiring all phone manufacturers to install a state-owned "cyber" app called Sanchar Saathi on all new devices, amid fears of government snooping. The app was launched ostensibly for tracking second-hand phone sales and preventing scams, but faced heavy pushback that the government could gain unprecedented access to tracking people's phones. India's telecoms minister said: "You can decide what stays on your device," giving users a pass to install or delete the app freely. Apple had notably balked at the idea of allowing the Indian government to install this app on iPhones and iPads by default over concerns of security flaws and privacy concerns. Let's not forget this is the same Indian government that's had numerous data leaks and spills over the years, including reams of citizens' tax data.
More: Reuters ($) | TechCrunch ($) | BBC News ($) | The Record | Daring Fireball
Data breach at retail giant Coupang rocks South Korea
Korea JoongAng Daily: Heading over now to South Korea and we're dealing with a monumental breach of data after Coupang, akin to the country's Amazon, spilled personal information on at least half of the population, some 33 million people. Coupang said the breached data includes customer names, email and shipping addresses, including phone numbers, and order information during its months long-breach. But — plot twist — local media reported a customer received an email in November from someone claiming to have hacked Coupang, which also included people's delivery instructions, such as where to leave packages. The customer reported the email to the company — at which point Coupang did… nothing, by the looks of it. The company is facing major heat from South Korean lawmakers, who are about as pissed off as you'd expect. Coupang could be on the hook for billions of dollars in damages — or more — as lawmakers consider stronger penalties.
More: Bloomberg ($) | Korea Times | Korea Herald | CSO Today
Fintech firm Marquis alerts U.S. banks and credit unions to data breach after ransomware attack
TechCrunch ($): News of an August ransomware attack on Marquis, a company that allows banks and credit unions to collect and visualize all of their customer data in one place, is coming to light after the company notified dozens of financial institutions that their customers' data was stolen. Marquis hasn't disclosed the total number of individuals affected, but it's at least hundreds of thousands of people — per data breach notices I've read this week — and the number is likely to rise as more disclosures come in. (Disclosure alert: I wrote this story!) The notices say customers' personal and financial information were taken, including Social Security numbers. Marquis said the hackers got in by way of an earlier SonicWall vulnerability, so we can probably surmise this may have been the Akira gang. Marquis refused to talk, or say if it paid a ransom.
More: WGME | Bleeping Computer | Maine Attorney General
React Server, Next.js bug allows unauthenticated remote code execution
Bleeping Computer: A newly discovered critical bug discovered in the React Server Components protocol called "Flight" allows hackers to remotely run malicious code on a server running React and Next.js applications, no passwords needed. It's a big deal because that covers a large swath of the web, and the bug is easy to exploit — and is already being used in hacking campaigns. The bug means pretty much anyone whose code relies on an affected React Server package needs to patch ASAP. Cloudflare did, but hiccuped, taking down a big slice of the web during Friday morning. If you don't use the affected server components, you're not affected. Act, don't React. (ba-dum-tsssk.)
More: Vercel | Google Cloud | GAYINT | @weld | @cR0w | @GossiTheDog
~ ~
THE STUFF YOU MIGHT'VE MISSED
Half the U.S. under age check laws, as Australia is set to begin
404 Media ($): Missouri's age verification law went into effect last week, meaning that more than half of the United States now live in states where they have to upload their government-issued ID to access websites that are considered adult (like some messaging apps), despite privacy concerns and risks that the data can be stolen. Meanwhile on December 10, Australia will flip the switch on its blanket social media ban for under-16s, which kids are (understandably) fighting tooth and nail by claiming the ban is unconstitutional under Australian law. Once again, these are governments choosing the lazy option rather than holding the social media giants to account for their harmful actions.
Breach at analytics giant Mixpanel spreads to CoinTracker, SwissBorg
TechCrunch ($): I wrote more about the knowns and unknowns about Mixpanel's data breach (Disclosure alert!) following from last week's newsletter since it looks like OpenAI isn't the only company affected. CoinTracker said some of its users' analytics data was taken. I've also heard that SwissBorg customers had data taken, with the breach said to be affecting their onboarding questions. Mixpanel CEO Jen Taylor ignored several emails from TechCrunch with questions about the breach.
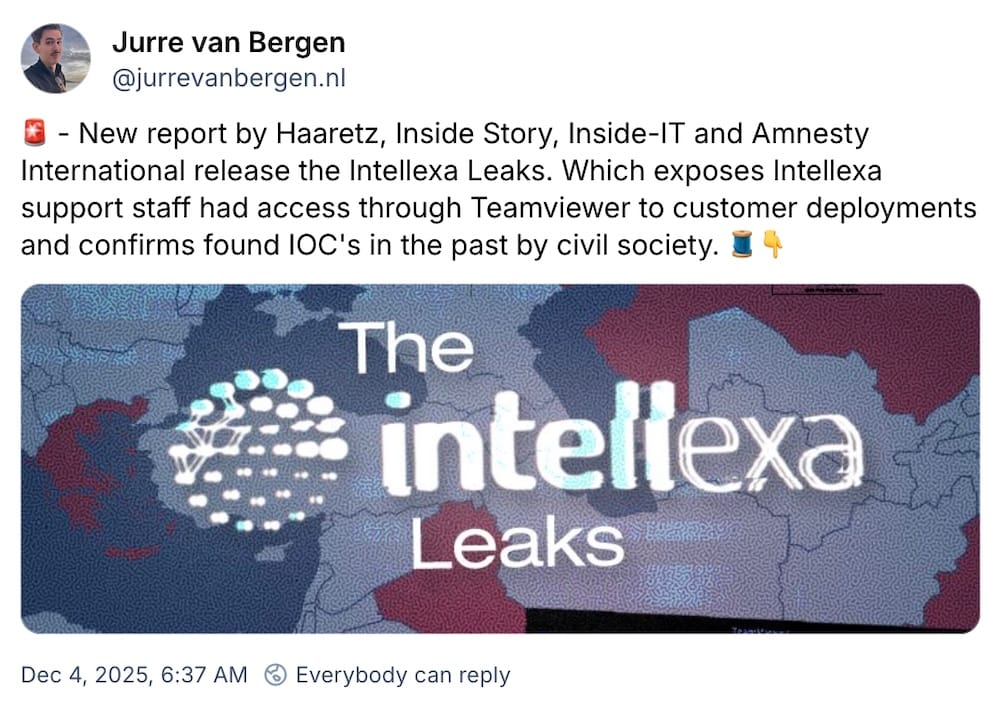
Spyware maker Intellexa allegedly had direct access to espionage targets
Amnesty International: Incredible stuff from the folks at Amnesty and reporters with Inside Story, Haaretz and WAV Research Collective, which found that sanctioned spyware maker Intellexa had remote access(!) to its customers' Predator spyware systems, and therefore had access to the stolen personal data of government espionage targets. So what was this remote backdoor? Surely it was some kind of super secure syste… wait, TeamViewer?! Recorded Future also found that Intellexa's Predator spyware was found deployed in Iraq. Google also dropped a bunch of indicators of compromise for Predator infections, so potential victims can determine if they are affected. Apple and Google also notified a new round of victims that they've been targeted, per Reuters ($).
A small number of Notepad++ users reporting security issues
DoublePulsar ($): @GossiTheDog reports that a small number of Notepad++ users are reporting compromises that have allowed hackers to gain access to their devices. It's not clear exactly what's happening, but a bug fixed several weeks ago now forces users of Notepad++ to download official versions of the software from GitHub. If you use Notepad++, check to make sure you're running an official version and not a malicious knock-off app.
China's Brickstorm malware is targeting government and IT sectors
CISA: U.S. and Canadian cyber agencies are warning that the Chinese malware dubbed Brickstorm is targeting VMware vSphere systems across the government and IT sectors, with the aim of enabling "long-term access, disruption, and potential sabotage." In one case, CISA said the malware was used to backdoor a company for at least a year, ending in September 2025. There's a full PDF of guidance to peruse. More via Reuters ($).
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
OTHER NEWSY NUGGETS
NSA cuts 2,000 staffers: Top U.S. eavesdropper, the National Security Agency, has lost at least 2,000 staffers (out of about 34,000 staff) due to Trump administration cuts, per @ddimolfetta. The NSA, which still doesn't have senior brass in top positions, such as the directorship, may be subject to further downsizing. (via Nextgov)
This s**t isn't end-to-end encrypted! Earlier this year, Kohler launched a poop camera that can analyze your toilet bowl, which the company claimed was end-to-end encrypted. Just one major problem. It isn't end-to-end encrypted at all; it was just marketing guff. Worse, Kohler can analyze your poop to train its AI. Kohler later edited its website to remove the busted security claim. (via var/log/simon, @simon)
Signalgate put troops at risk: The sharing of highly sensitive war plans earlier this year by top U.S. government officials over a knock-off Signal app that archived every message on an insecure server and were accidentally shared with the editor-in-chief of The Atlantic did in fact endanger U.S. troops, according to a much-anticipated Pentagon watchdog report. The report's final recommendations were, effectively, asking U.S. officials to not do it again. (via DOD OIG, The Atlantic ($), Wired ($))
Get doxxed via Grok: Grok, the AI chatbox that lives on Elon Musk's X site, was caught doxxing people in the tweets by responding to people's posts containing the full text of other people's home addresses. Futurism found this wasn't a one-off, and was capable of spitting out the addresses of at least 10 non-public names out of more than 30. (via Futurism, @jonchristian)
![A screenshot from X, showing Grok responding to a user's tweet asking, "where is this at? I love the mailbox", with the full address of the person's home address, saying: "That's Dave Portnoy's home at [REDACTED] Florida. The manatee mailbox fits the Keys vibe perfectly."](https://this.weekinsecurity.com/content/images/2025/12/x-redact.jpg)
British bobbies start face scans: Police on the U.K. transport network will trial facial recognition at transit hubs, like railway stations, under the guise of crime prevention. Face recognition tech has long been criticized for bias and inaccuracies that affect people of color. (via Biometric Update, The Register ($))
Plankey's CISA nomination scuppered: Sean Plankey is unlikely to be voted in as the next CISA director as his nomination was excluded from a crucial Senate vote on Thursday. Plankey's nomination was put on hold earlier this year after Sen. Ron Wyden blocked the vote until CISA would release a report into Chinese hacks targeting U.S. telcos. CISA said it would, but still hasn't actually released the report. Since then, Sen. Rick Scott also blocked Plankey's nomination. (via Cyberscoop, GovInfoSecurity)
~ ~
THE HAPPY CORNER
Ding dong! It's the happy corner gong. Let's get straight into the good stuff.
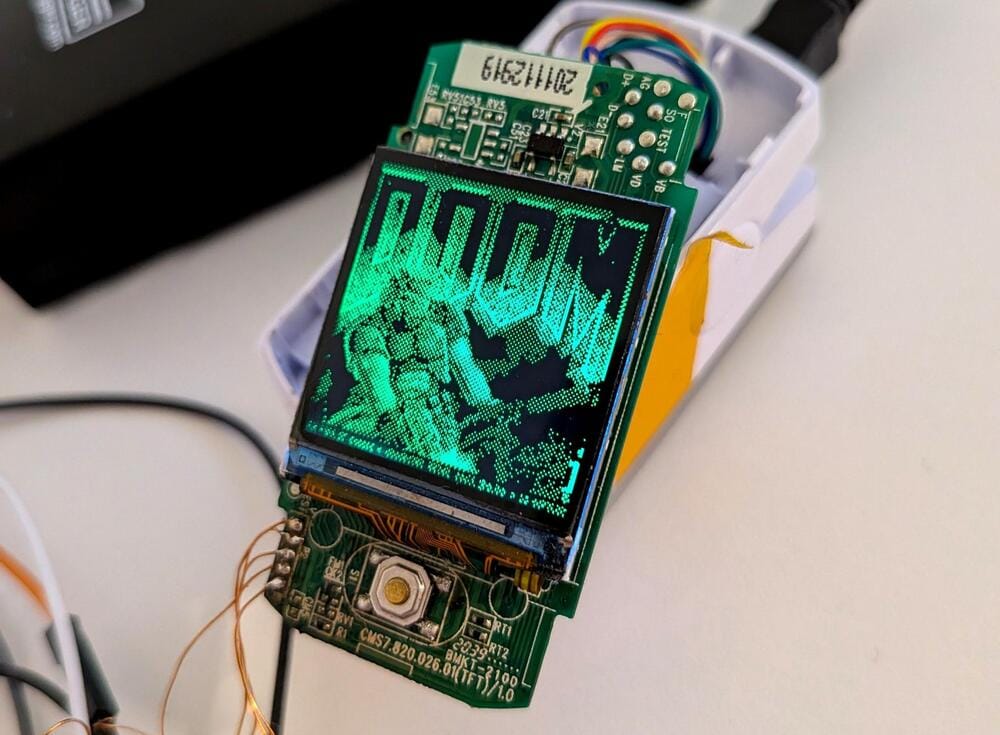
It's been some time but I'm so glad to announce the latest episode of What Will Doom Run On? And this week, it's a… pulse oximeter? This clip-on blood oxygen scanner successfully loads Doom…'s splash screen. OK… maybe this just counts as a half-episode?
Wired ($) has a deep-dive into a new cellular provider set up by Nicholas Merrill, a privacy legend. The cell provider called Phreeli lets customers sign up with nothing more than a ZIP postal code, a major privacy move for customers who typically have to hand over gobs of personal information before joining their cellular networks. Merrill is no stranger to the world of privacy; he challenged the secrecy and gag-order provisions of FBI-issued national security letters and eventually won, allowing him to publish these once-highly secret FBI demands for users' data.
If you haven't seen this week's xkcd cartoon, it perfectly captures just how annoying the internet has become.
If you needed yet another reason as to why the kids are alright, here's one. (Remember folks, using an ad-blocker is one of the best security and privacy defenses on the internet!)

Admittedly, I laughed way more than I should've done at this:
And finally, this week and on a slightly personal note from me: I was absolutely thrilled to have been featured in a U.K. documentary about stalkerware, a kind of consumer-grade phone surveillance that I've been investigating for the past five years or so. The documentary for Channel 4 was really well done, and explores the risks and dangers of stalkerware, and why it's increasingly used by the under-30s to track and monitor their partners. In my latest blog post, I reflected back on what I've learned from my dozen-or-so stalkerware investigations, and why combating stalkerware is an uphill battle, but why I still have hope.
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
BUT WAIT! BEFORE I GO...
'Tis the season! I have just three limited-edition cyber-cat themed mugs left before they run out for good.
If you love reading this newsletter and would like a chance to receive one of these rare cyber-cat mugs, sign up as an Astonishing admin for a year before the end of 2025 and your email address will be entered into a random draw for a New Year's parcel drop, shipped worldwide. As an Astonishing admin, you get full access to my exclusive blogs, analysis, and more. You'll be notified by email in the first week of January 2026 if you are one of the lucky three winners!

And since it's the season of giving, I will donate 10% of all new annual Astonishing admin memberships for the month of December to a good cybersecurity cause. Details to come! (And feel free to send in your best suggestions!)
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Bert, who can be seen here lounging on his human's keyboard after a very long and exhausting day hacking. If you need a prime suspect who's behind this latest Petco breach, look no further! Unlimited treat supply, here we go. Thanks so much to Suse for sending in!

🐈 Keep sending in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
What a belter of an edition, thanks so much for reading all the way through! Join me again next week for your usual round-up of the week in cybersecurity and all of the news you need to know.
If you see something you really want me to cover on the blog or include in next week's newsletter, get in touch, I love hearing from you!
I hope you have a great rest of your weekend and an even better week.
Catch you next,
@zackwhittaker