this week in security — february 15 2026 edition
THIS WEEK, TL;DR
Ivanti zero-days under attack blamed for hacks on European governments
Cybersecurity Dive: We start with Ivanti, as its latest round of zero-days allowed hackers to take over (what feels like) half of Europe. The Dutch government last week said its judiciary and data protection agency were hacked, blaming a recently disclosed zero-day in Ivanti's EPMM software. The EU Commission also said it had staff data compromised in a breach, and Finland's government IT unit said thousands of its employees had contact information swiped in its hack, though neither named the vendor. Researchers think the hacks may be carried out by initial access brokers, who break into systems then hand off their access to hacker groups (for a price). GreyNoise said its data shows most of the exploitation is tracked to a single IP on a bulletproof host (read: a web host that authorities can find difficult to take down), which hasn't been widely publicized, meaning if you're relying on public IOCs for blocking activity, you need to go back and look again.
More: Cyberscoop | Defused | Valtori.fi | European Commission
South Korea blames Coupang's massive data breach on management
Reuters ($): Veering all the way over now to South Korea, which is still mopping up after its largest retail giant, Coupang, was hacked last year to the tune of 34 million people's private data, or about half of the country's population. Aside from investors suing the company, dubbed the "Amazon of South Korea," the government in Seoul is now squarely and publicly blaming the company's management for its months-long breach and not a "sophisticated" attack as the company claimed… because, by all accounts, it wasn't! A former employee had knowledge of flaws in Coupang's system and later stole reams of data, without the company noticing. The country's investigation continues.
More: TechCrunch ($) | The Straits Times | UPI | DataBreaches.net | @metacurity
Prosecutors say Trenchant boss sold exploits to a Russian broker that could hack 'millions' of computers
TechCrunch ($): U.S. prosecutors are requesting nine years in prison for Peter Williams, aka "Doogie," the former head of L3Harris' hacking tools maker Trenchant, for stealing at least eight exploits from the company's systems and selling them to a Russian broker, which counts the Russian government among its clients. Prosecutors said for the first time that the exploits would have allowed the broker and its customers access to "millions of computers and devices around the world," including in the United States, to conduct ransomware attacks and indiscriminate surveillance. In response, Williams, who pleaded guilty, apologized and said he regrets his actions. He's expected to be sentenced in the next week or two. If you missed the whole back story of how he stole these exploits under the nose of his employer, @lorenzofb broke the news last year.
More: SC World | Wired ($) | @lorenzofb | @vaspanagiotopoulos
Ring and Nest face backlash over video surveillance fears
The Verge ($): Ring, the Amazon-owned maker of surveillance doorbells, sparked widespread furore and general ick after a Super Bowl ad went viral for grossing out the entire United States. While Ring thought it was cute to air an ad that claimed it could "find your lost dog" quickly turned into, "what if ICE starts using this surveillance gear to round up people?" Even the internet's favorite dog account, @WeRateDogs, was super grossed out, showing how far this controversial ad spilled out of the walls of the internet. The backlash prompted Ring's mercenary PR flacks to claim its doorbell cameras are "not tools for mass surveillance." (*coughs loudly* Bullsh*t!) Ring later tried to quell the furore by cancelling its deal with Flock over its ties to ICE, but that isn't even the worst of Ring's partnerships! Meanwhile: All eyes on Google's Nest cameras, which reportedly uploaded camera footage from the home of a missing woman whose camera didn't even have an active subscription. The FBI said they fished out footage from Google's cloud. If you feel the need to use surveillance, at least consider a camera that's end-to-end encrypted…
More: NBC News | 404 Media ($) | The Verge ($) | The Interface | AP | @weratedogs
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more, including:
How tech giants track you across the web, even if you don't use their apps
Apple's Lockdown Mode: Once an 'extreme' security protection, now a necessity for Americans
TriZetto failed to stop hackers stealing Americans' health data for a year
~ ~
THE STUFF YOU MIGHT'VE MISSED
Cities report billing outages after BridgePay ransomware attack
DysruptionHub: Cities across the U.S., including in Florida and Texas, are reporting billing system outages after payments processor BridgePay was hit by a ransomware attack, per its status page. The Record reports widespread downstream outages for government customers, and other businesses that rely on BridgePay. For its part, the company says this was not a breach of payment cards.

Thousands of OpenClaw instances publicly exposed, risking user hasks
The Register: Thousands of instances of the self-hosted open-source AI agent OpenClaw are putting their owners at risk of hacks, as the software contains high-risk vulnerabilities, such as listening of all network interfaces. Speaking of: BBC's @joetidy reveals the risks of running poorly secured AI platforms, such as Orchids, by showing how easy it is for a hacker to break into his computer running the software.
Discord to roll out age-checks globally, despite data breach
The Verge ($): Discord announced it will roll out mandatory age-checks across the globe, and will automatically set accounts as "teen-appropriate" unless they verify with a face scan or an upload of their government ID. Discord's move to roll out age-checks comes despite a data breach last year that let hackers steal government IDs of Discord users who sought to verify their age. More thoughts via @jmiers230 and @dangoodin. Of course, the kids are already bypassing these face checks with easy hacks. For those wanting to move away from Discord, @mttaggart has some Discord alternatives you might want to check out.
Senegal reveals ransomware attack hit national ID agency
The Record: A ransomware gang reportedly took credit for hacking Senegal's Directorate of File Automation, which runs the country's national ID card system. The office stopped functioning last week. Several stolen files, including leaked emails, appear to confirm the breach. Argentina and Estonia had similar breaches of their national ID card system in the past. This comes as India aims to expand its national ID system, Aadhaar, which covers over a billion people but has also seen its own raft of data leaks in recent years.
Windows users need new Secure Boot certificates soon
Microsoft: Secure Boot, a security feature introduced in Windows 8 that ensures unverified software can't load with Windows as it boots up, will need new certificates come June and October, or PCs without them could face future issues on startup. Make sure you get those necessary patches before then! More words from Ars Technica.
Trio of zero-days hit Windows users
Cyberscoop: Speaking of security updates… Windows users got plenty of fixes in this month's Patch Tuesday drop. The updates fix several bugs under attack, including three zero-days, one of which affects all versions of Windows, and can be exploited in a one-click attack. Microsoft said hackers were actively abusing the bugs to target people, and details of the bugs are public, meaning hacks are more likely. More via Krebs On Security.
~ ~
OTHER NEWSY NUGGETS
Dogfood dogsh*t security: Productivity suite SmarterTools said a ransomware gang broke into its network and a datacenter by way of exploiting an unpatched vulnerability in one of its own products. A company executive blamed an employee for setting up a SmarterTools server that the company wasn't aware of. Counterpoint: it's the company's fault for not detecting the rogue server sooner! (via Bleeping Computer, SmarterTools)
Spy for me, and for thee? A surveillance law that allows the NSA and FBI to spy on people's communications — FISA's Section 702 — is expiring in April and the Trump administration still hasn't given lawmakers any decent indication whether it wants to renew the powers or not. Bipartisan lawmakers were critical of the administration as officials were unable to answer basic questions. (via CNN, Nextgov, Brookings)
Why did the U.S. drop spyware sanctions? Meanwhile, Democratic lawmakers want to know why the Treasury recently dropped sanctions against several executives of Intellexa, the maker of the Predator spyware, which was implicated in multiple scandals across Greece and wider Europe. The lawmakers said this comes not long after Google said Predator continued to spy on people while evading sanctions. (via Bloomberg ($))
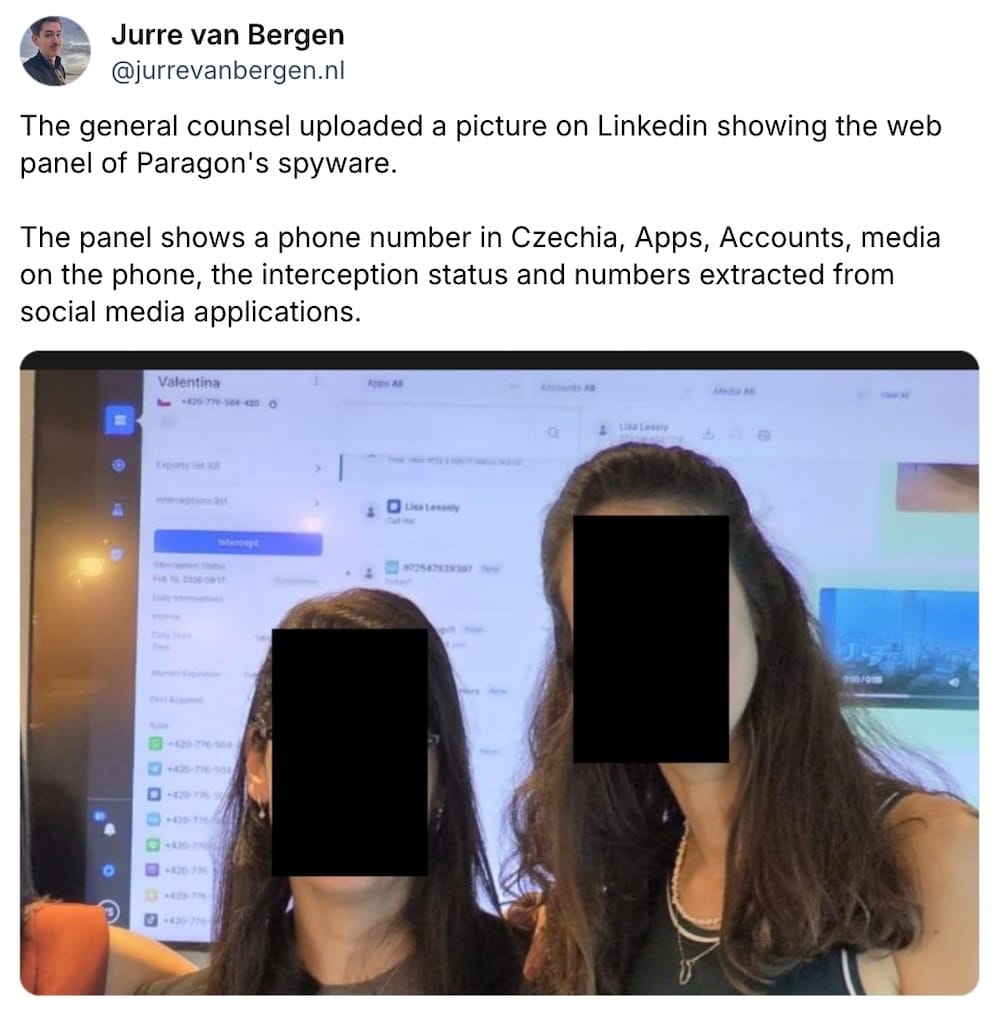
Spyware slip up: Filed under whoooops: The general counsel of spyware maker Paragon posted a photo allegedly revealing a partial screenshot of the spyware's backend dashboard. This allowed eagle-eyed watchers like @jsrailton to identify what kinds of data this spyware can steal from people's phones. (via @jurrevanbergen)
So, about that whistleblower complaint: It turns out last year the NSA overheard a call from foreign intelligence about Trump's son-in-law Jared Kushner, which prompted the U.S. government's top spy Tulsi Gabbard to flag the call to the White House's chief of staff and not the FBI as what probably should've happened. The contents of the call aren't public (yet, lol) as the claims are capable of "severely" damaging national security (👀). The White House was keen to stress the allegations about Kushner, which — again, not public! — were demonstrably false. So, uhhh… (via WSJ ($), The New York Times ($))
Singapore says telcos tapped: Singapore's government linked a China-backed espionage group (aka UNC3886) that hacked four of its top telcos for months as part of a suspected espionage operation. Previously, the government had only said that its critical infrastructure was under attack. (via Reuters ($), SecurityWeek)
~ ~
THE HAPPY CORNER
And enough with that busy week! Behold, it's the happy corner.
Happy (belated) Valentine's Day to anyone over the age of 35 who gets this reference:
And shoutout to @cR0w for this year's alternative Valentine's Day message. Very apt, very true.
Are you using Lockdown Mode yet? Because while it used to be billed as an "extreme" protection for people facing cyberattacks, it's passed yet another real-world test by blocking feds from snooping on a journalist's phone. I wrote about why it may be a good idea for Americans to consider switching on the security feature.
And, pour one out for Palmerston, one of the U.K. government's official cats and former chief mouser to the Foreign Office, who this week passed over the rainbow bridge in Bermuda, where he lived out his final days (via @jamesrball). Palmerston may well be best known for sparring with his fellow civil service cat, Larry, who just marked 15 years at Downing Street.

Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat puppers are Baxter (top) and Scarlet (bottom), who can be seen here ready for cuddles and snuggles, but wouldn't hesitate for a second to "borrow" your credit card to buy themselves toys and treats. Thanks so much to Ryan for sending in!

Ding dong! It's the cyber-cat gong! Every newsletter features a cyber-cat (or non-feline friend!) submitted from readers like you. Want to join in? Send me an email with a photo and their name, and they will be featured in a later newsletter!
~ ~
SUGGESTION BOX
And that's it for this edition! Thanks so much for tuning in, subscribing, and generally just being you. It really means a lot that you read, and I'm fortunate that I get to send this newsletter every week. I'm thankful for your support.
As always, if you ever want to get in touch with suggestions, feedback, questions, or anything for the newsletter, please get in touch!
Take care, and catch you next Sunday. Have a great rest of your week.
Ta ta, for now,
@zackwhittaker