this week in security — february 22 2026 edition
THIS WEEK, TL;DR
Hackers breached Ivanti in 2021 via bug in its own VPN, allowing access to dozens of other customers
Bloomberg ($): We start with brilliant reporting from Bloomberg, digging deep into Ivanti, a maker of VPN products used by the U.S. government, Fortune 500, and beyond. But, as often happens, private equity dealings, cost cutting, and layoffs put the security of its products at risk — and the companies that rely on them. Case in point: In February 2021, the company learned Chinese hackers had compromised its subsidiary's IT networks via its proprietary VPN product, Pulse Secure. The same flaws allowed access to over 100 other companies, including U.S. and European military contractors. Turns out this is just one of three major hacks affecting Ivanti in recent years. The reporting comes as Ivanti battles another hacking campaign targeting one of its other products, EPMM, which organizations use for managing fleets of employees' mobile devices. German authorities say the recently discovered zero-day under attack was first exploited back in 2025… so Ivanti has really taken its eye off the ball of late (*cough* years). Ivanti's slow suffocation by private equity follows similar blockbuster Bloomberg reporting last year into penny-pinching by Cloud Software Group, which owns Citrix (and whose boss was a senior DOGE staffer), and a company synonymous with security flaws.
More: BSI | Palo Alto Networks | @sambowne | @GossiTheDog

Microsoft says bug caused Copilot to summarize confidential emails
Bleeping Computer: Microsoft admitted a major AI whoopsie, where AI stands for Accidentally Ingesting confidential emails of paying Microsoft 365 customers. The tech giant said its Copilot Chat was summarizing sent and draft emails, bypassing any data protection policies that were in place, since at least January 21 (tracked as CW1226324 for admins.). Microsoft wouldn't say how many customers had data sucked into Copilot, but highlights the risks with having AI chatbots being able to see and access your data — even if it's said to be private. Meanwhile: Amaz-oh-no: Amazon Web Services had two major outages recently due to errors caused by AI tools.
More: TechCrunch ($) | Financial Times ($)
European Parliament blocks AI tools citing cybersecurity concerns
Politico: Speaking of AI risks… the European Parliament is trying to save lawmakers from themselves by blocking them from using the AI tools baked-in to their work-issued devices. The fears are that AI could upload confidential files and share it with others. This comes as the EU looks to move away from U.S. tech (and unpredictability and instability). Interestingly, Coinerella looks at a shopping wish-list for building a startup with EU-only tech and found it wasn't as easy as first thought.
More: The Register | Financial Times ($) | eWeek | Euractiv
Def Con bans three technologists named in Epstein files
TechCrunch ($): Three techies made it on the Def Con conference's forever sh*t-list for their ties to late sex offender Jeffrey Epstein. The con announced the bans in its transparency report, adding Pablos Holman, Vincenzo Iozzo, and former MIT Media Lab director Joichi Ito to a list made up of people mostly accused of sexual misconduct (or enabling it). This comes after the Justice Department released a new tranche of emails exposing people who maintained links with Epstein, even after pleading guilty to sex crimes in 2009 and high profile reporting exposing sex trafficking years later. Iozzo was also removed from the website of Black Hat's review board.
More: Nextgov | SC World
U.K. considers limiting access to VPNs to bolster age-checks
U.K. Government: As governments increasingly push age-checks and identity verification under the guise of protecting children, the U.K. — a frontrunner in age-gating the internet — is reportedly looking to expand its online ID checks by cracking down on VPNs "where it undermines safety protections and changing the age of digital consent." Pretty broad, but the U.K. is suggesting this because some have used VPNs to bypass online age-checks, which are meant to prevent kids from accessing social media sites. This follows an earlier proposal to potentially require ID checks before using a VPN — which seems like a really bad idea given that regular businesses could suffer as a result. Let's take you to a live shot of the U.K. right now as it looks to implement this policy…
More: @realhackhistory.org | @Em0nM4stodon | Alec Muffett
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
THE STUFF YOU MIGHT'VE MISSED
How Bluetooth is used to track you
DMCC: I'm a little late to this one, but this was a good read looking at how Bluetooth signals can be used to track our devices, and what kinds of metadata it can reveal about us. Since we're talking about threat modeling, Wired ($) has a great guide on how to organize in the age of growing surveillance.
ATM jackpotting attacks are netting hackers millions in cash
TechCrunch ($): The FBI is warning ATM owners to secure their cash dispensers as gangs are increasingly and successfully "jackpotting" ATMs with malware, forcing them to spit out reams of cash. Some gangs are making millions, per the feds. Many of these ATMs run Windows, which allows the malware to hack a range of different devices. (Disclosure: I wrote this story!) More from IC3 [PDF]. Time to break out this classic ATM jackpotting demo from Black Hat 2010.

China hackers are exploiting Dell RecoverPoint zero-day
Google Threat Intelligence: A group of Chinese hackers are targeting a hardcoded credential zero-day in Dell RecoverPoint (software used by enterprises to jump back to a virtual machine's snapshot in time). The bug has been exploited as far back as mid-2024(!) to plant a backdoor called Grimbolt. Google says this newly discovered hacker gang dubbed UNC6201 has "notable overlaps" with Silk Typhoon (aka Hafnium, which targets the IT supply chain) because it was seen previously using their Brickstorm malware. More via SecurityWeek.
Android malware found preinstalled on devices
Securelist: Kaspersky's latest research found malware baked-in to some Android devices and shipped with firmware, even before users complete setup. Device makers are likely unaware that the "Keenadu" malware is infiltrating devices and system apps as part of the software supply chain. One industry watcher said the malware gives attackers "effectively unlimited control and the ability to operate inside the context of every app on the device." More via CSO Online.
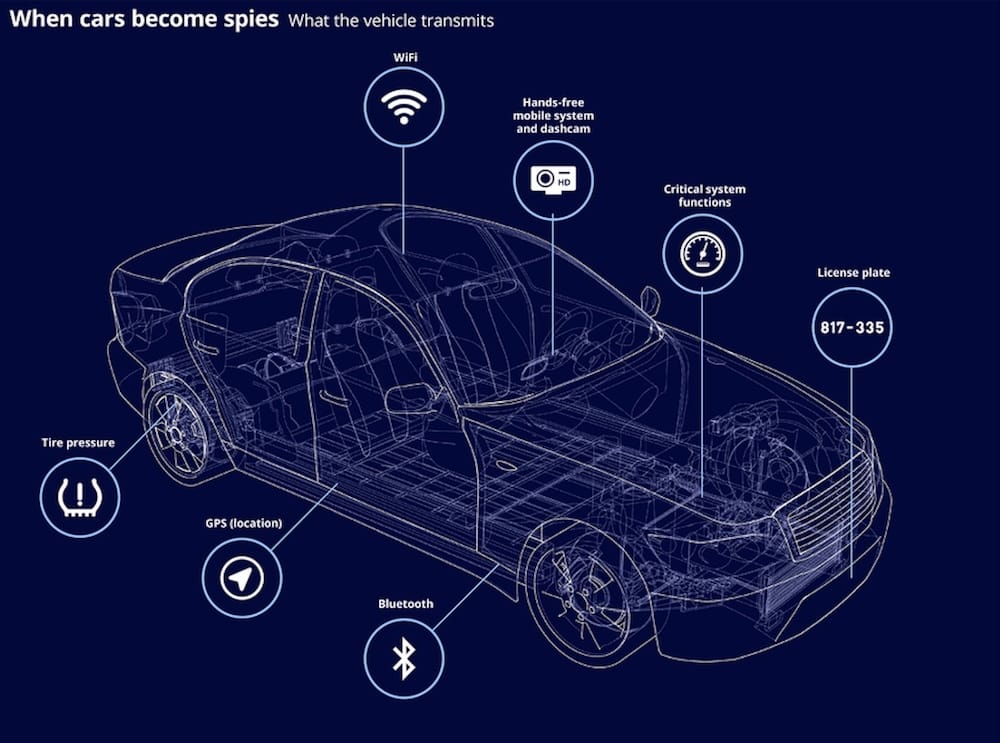
Surveillance firms are increasing tapping vehicles for tracking data
Haaretz ($): Brilliant reporting from Haaretz's @omerbenj who found Israeli companies are leading the surveillance race targeting cars and vehicles, known as CARINT (or car intelligence; after all, they're computers on wheels!). By tapping into the vehicle's cellular internet connection, some surveillance vendors are able to tap into real-time location data, the car's microphones, and its cameras.
ClickFix attacks are on the rise by both criminals and nation-states
Huntress: ClickFix attacks, which rely on people searching for quick fixes to tech issues but get tricked into pasting malicious commands into their computer that grant hackers access, have become the "most prevalent initial access method" for hackers and government spies alike over the past year, per Huntress. These hackers then hand off their access to your computer to ransomware groups (or others) in exchange for money. Relatedly, @patrickwardle has updated his BlockBlock tool to help prevent ClickFix attacks for macOS users. Also: I have much more for you on ClickFix attacks, what to look out for, and how you can protect yourself.
~ ~
OTHER NEWSY NUGGETS
CISA furloughs amid DHS shutdown: U.S. cybersecurity agency CISA has furloughed its staff and is running at about 38% capacity. This is because its parent agency Homeland Security was temporarily shut down amid a federal funding gap, as lawmakers balk at the idea of continuing to fund ICE and CBP's deportation operations across America. (via SecurityWeek, Nextgov)
Cellebrite balks on snoop probs: Citizen Lab found Kenyan authorities used Cellebrite's phone unlocking tech to snoop on the phone of a 2027 presidential candidate. This follows similar abuses by using Cellebrite equipment to target activists in Jordan. Cellebrite previously cut off Serbia from using its phone unlocking last year citing abuse of its tools, but refuses to say why it hasn't taken action of late. (via Citizen Lab, The Guardian ($), TechCrunch ($))
PayPal admits loan data leak: PayPal says around 100 people had information exposed by way of a bug in its PayPal Working Capital loan application over six months. The data spill included Social Security numbers. PayPal said it reversed the code change, but said it had detected some unauthorized transactions. (via Bleeping Computer, The Register)
Plus d'un million le hacked: Sacré merde… France reports a hacker obtained access to a national bank account database, exposing information about 1.2 million bank accounts. The hack was blamed on abuse of a stolen credential. (via ZDNet.fr, @gabrielthierry)
Hacker claims EURail breach: EU railway ticket operator EURail confirmed customers' personal and traveler data was stolen in a recent hack. The data was listed on a known cybercriminal forum, as seen by @DarkWebInformer, and claims to include passport details and other traveler data. The data is said to include millions of stolen records. (via TechRadar)
~ ~
THE HAPPY CORNER
Welcome to this week's happy corner, where there's space for peace, calm, and happy thoughts.
Getting ready for Monday morning… (via @starchy)
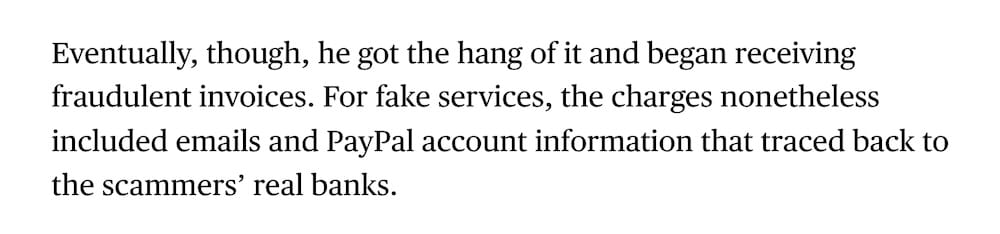
Props to this 16-year-old kid called Wyatt for helping networking gear maker Netgear to track down fraudsters who were trying to con its customers into buying nonexistent support packages. Wyatt essentially reverse social-engineered the scammers by pretending to be a victim of the fraud scheme. After a bit of refining, Wyatt helped Netgear chase the money backwards to the scammers' real bank accounts. Excellent work here, Wyatt. Sounds like you've got a promising career ahead of you! (Would've been nice had Netgear paid the kid more than minimum wage, mind you.)
Around the U.S., people are destroying and dismantling Flock cameras that are used for video surveillance and whose data is shared with ICE. It's lovely when people come together to support their communities! Some heartwarming tales of anti-surveillance via the excellent Blood In The Machine by @bcmerchant.
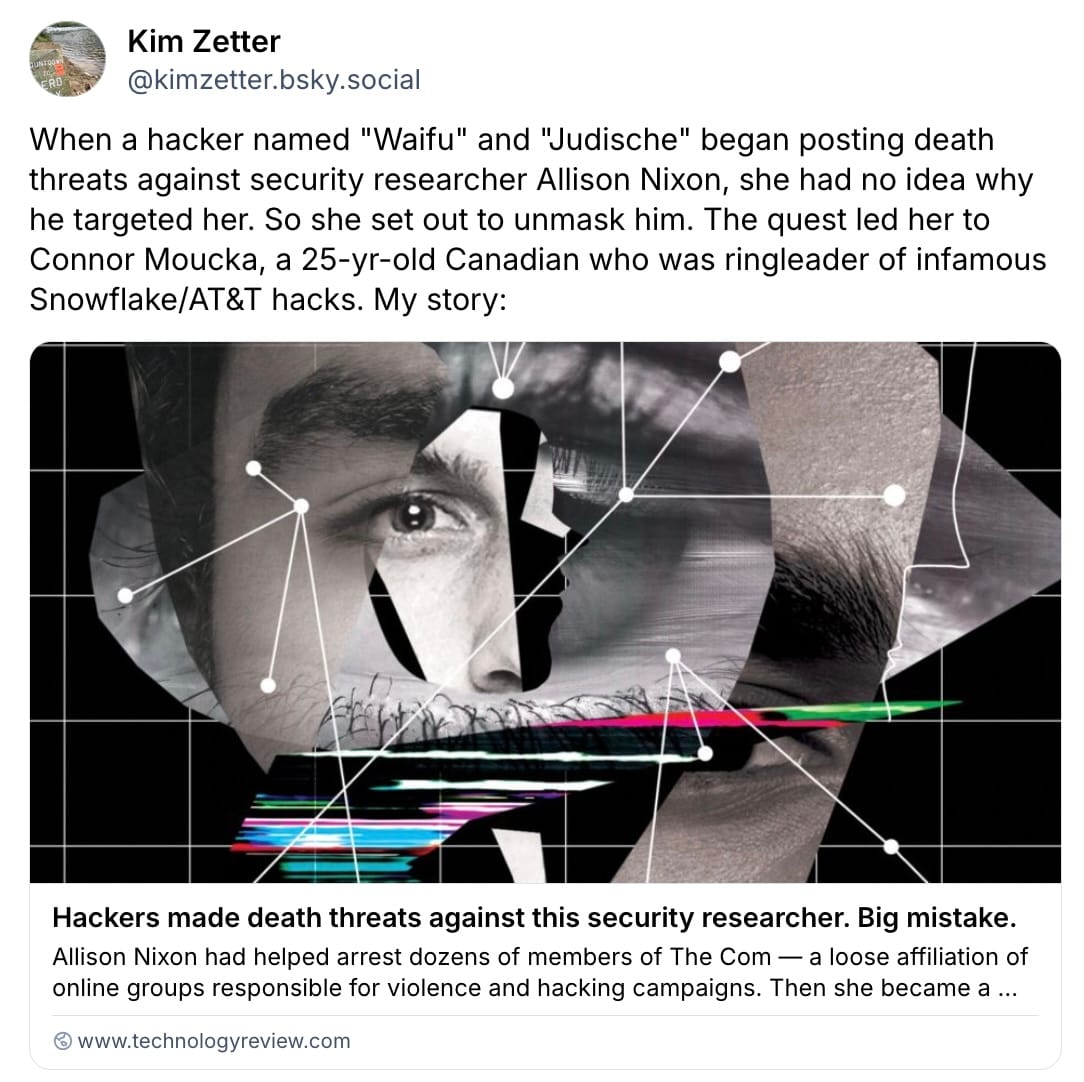
Meanwhile… when two hackers began posting death threats to security researcher Allison Nixon, she set out to unmask them — and succeeded. This is the inside story of how Nixon fought back against some of the world's most prolific cybercriminals. An absolute belter of a @kimzetter story.
And lastly. Don't forget the simple things in life. Love wins.
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cats are Arya and Batman, who can be seen here tucked in and snoozing after their busy cybersecurity adventures. It's a lot of work keeping folks safe and secure online! Thanks so much to Emily for sending in an update!

🐈⬛ Got cats? Send 'em in! 🐈⬛ This newsletter is fueled by your cyber-cat submissions! Send me an email with their photo and name and they will be featured in a later newsletter. If you've sent in before, updates are very welcome!
~ ~
SUGGESTION BOX
And that's it for this week! I started writing this newsletter edition seeing a few flakes of snow falling outside, amid days of warnings about a massive blizzard about to hit the U.S. east coast...

And, now, at the time of sending, it's now like this:

Stay safe and warm out there, cyber friends! If you want to get in touch with anything for this, or next week's newsletter, please do! Drop me a note by email any time. And if, like me, you're going to be stuck inside for a bit, take a moment to send in your top-quality, finest cyber-cats!
Catch you next,
@zackwhittaker