this week in security — february 8 2026 edition
THIS WEEK, TL;DR
Moltbook, the 'Reddit for AI bots', launches with major security lapse that exposed access to AI agents
Wiz: Let's start this week with Moltbook, the AI sensation that went viral overnight — as did the security flaws it launched with. Moltbook is billed as the "Reddit for AI agents" by allowing users' autonomous AI agents to talk to each other in public. But Moltbook's inadvertently public database exposed over a million API keys and other tokens representing about 18,000 humans. This was a major problem because these agents can be granted access to their users' private data, including bank logins and user passwords, and more. (These agents can also be tricked into processing malicious instructions, opening these agents — and their users' data — to a raft of abuse.) Security giant Wiz found the Moltbook exposure and immediately disclosed them to its maker. It's no surprise there was a major security flaw, given the entire platform was "vibe-coded" with AI to create this anti-security slop. This is just the latest in a string of many AI projects to go public (with people's data, literally). (*Corrected due to inaccuracy.)
More: MIT Technology Review | Reuters ($) | 404 Media ($) | The Register
Notepad++ says Chinese-backed hackers hijacked updates for months
Ars Technica: The developer of Notepad++, one of the longest running open source projects, confirmed that the text editor's update mechanism had been hijacked by suspected Chinese government-backed hackers for months. Rapid7 dove into the analysis, attributing the hack to China's Lotus Blossom, which has targeted companies and government sectors across Southeast Asia and Central America in the past. Per Notepad++'s developer Don Ho, the hackers broke into his shared online hosting and abused the access to manipulate the server endpoint that Notepad++ checks for software updates. This allowed the hackers to redirect some users to a malicious update on their servers. Props to @GossiTheDog for spotting this months ago while the attack was going down.
More: Notepad++ | Censys | SecureList | @GossiTheDog
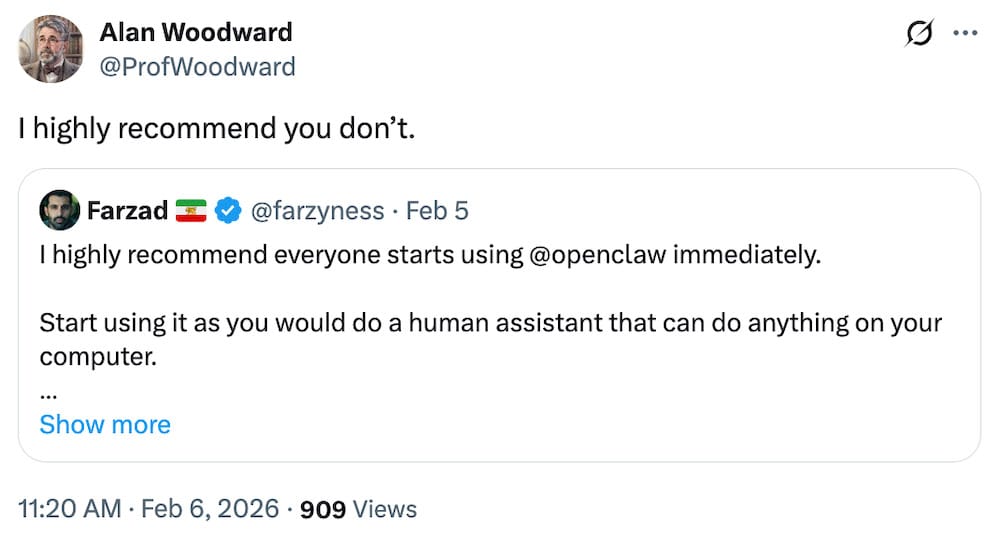
Homeland Security is trying to force tech firms to turn over data about Trump critics
TechCrunch ($): The U.S. government is really, really stretching the limits of the Fourth Amendment these days. Stories by Bloomberg ($) (which I mentioned last week) and the Washington Post ($) reveal how the Trump administration is explicitly targeting critics of the government's policies by demanding personal data about them from tech companies (including Google and Meta) using "administrative subpoenas," which aren't even signed by a judge(!). Using these subpoenas, Homeland Security is trying to unmask anonymous Instagram accounts and demanding information about people's Gmail accounts, and using the data to send federal agents to their doors — in one case, an American retiree. In my article (disclosure alert!), I wrap up the two stories with comments from the tech firms and Homeland Security's top spokesperson, which claims the agency has broad authority to demand data from tech companies. Remember, this affects everyone who uses a U.S. tech service, even overseas, because the Fourth protects your data from U.S. demands, too! This is incredibly chilling stuff, but sunlight is the best disinfectant.
More: Techdirt | The Verge | ACLU | @willoremus
Substack, Flickr, Betterment hacks; Conduent breach balloons
Data Breach Roundup: It was a busy few days in data breach land, so let's rattle through a few of them…. *breathes in*… Newsletter platform Substack had a data breach, spilling the email addresses and phone numbers of some 700,000 or so subscribers… A breach at fintech giant Betterment affects over 1.4 million people, according to Have I Been Pwned. Meanwhile: Data stolen from Harvard and UPenn last year is now public after the ShinyHunters claimed responsibility for the hack this week, affecting at least a million people. Onwards: Flickr was hacked, too, affecting users' email addresses, IP addresses, and their approximate geolocation data. Coinbase confirmed an insider attack that affected the personal data of about 30 people (still not great after last year's unrelated breach)... and… not to be outdone, the ransomware attack on govtech giant Conduent is ballooning in size, and now affects millions more Americans than first reported.
More: Bleeping Computer | TechCrunch ($) | DataBreaches.net | @newsguyusa
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
THE STUFF YOU MIGHT'VE MISSED
Survey shows researchers and journalists mostly rebuff legal and criminal threats
this week in security: And the results are in! DataBreaches.net and I ran a survey several weeks ago to gauge the state of legal and criminal threats against security researchers and journalists. We found that in the face of threats, most researchers and journalists stood their ground and did not alter or retract their findings. We have a ton more findings for you to read through (PDF).
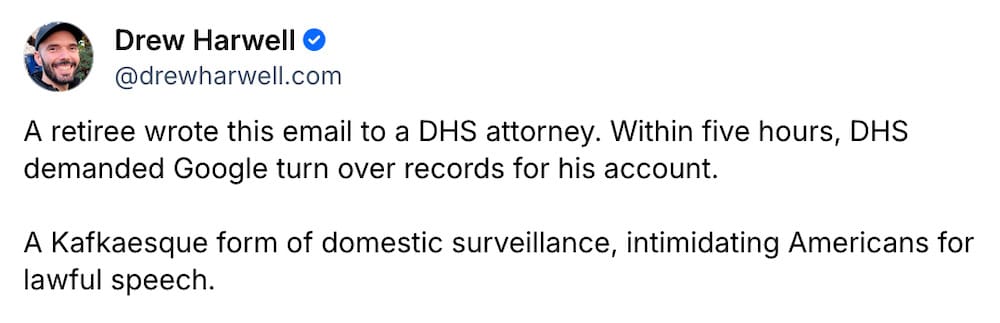
NSA detected foreign intelligence call about a person close to Trump
The Guardian ($): The NSA allegedly intercepted at least one call last year by people linked to a foreign government (friendly or not, we don't know), which discussed a person close to President Trump. Details of the call weren't clear, nor the person involved, or even the foreign government, let alone if there's any wrongdoing by the person involved. But what we do know… and the Wall Street Journal ($) confirmed as well… that the U.S. top spy Tulsi Gabbard withheld the information for eight months(!) from federal investigators like the FBI (tasked with weeding out potential foreign interference) and members of Congress (who ultimately oversee the intelligence community) and instead took it directly to Trump's chief of staff Susie Wiles. All of that makes you (and lawmakers) wonder: why?
Senator says he has 'deep concerns' over CIA activities
Techdirt: Potentially not even the worst news for the CIA this week, as Sen. Ron Wyden went public with a rare two-line letter, noting that he has "deep concerns" about some of the CIA's activities. He can't say what exactly, as the matter is classified, but clearly it's something enough that he could hint about it in public. This isn't the first time he's sounded the so-called "Wyden siren," but whenever he does (think NSA phone records surveillance and the FBI spying on push notifications) he's always been vindicated.

Russian space vehicles may be intercepting satellite comms
Financial Times ($): European officials fear that at least two Russian space vehicles may be tapping satellite communications (many of which are unencrypted!) over the continent or worse, manipulate their trajectories to crash them. The vehicles, Luch1 and Luch2, were seen performing suspicious maneuvers in orbit, at a time when Russia is stepping up its hybrid war (land! sea! cyber! space!) on the West. (More via Space News.)
Anthropic says its Claude AI model found hundreds of security flaws
Axios ($): Anthropic's newest AI model, Claude Opus 4.6, found over 500 security flaws (validated by a security researcher) in open-source software. Little word on whether the bugs had any practical exploitability, but it's good to see at least some use for the water-guzzling tech, even if — like all AI models prone to errors (and flat-out making stuff up) – it means having to double-check the work. Some more thoughts via @briankrebs. (I still hate AI, in case you wondered.)
~ ~
OTHER NEWSY NUGGETS
Crypto stolen after execs hacked: Step Finance said hackers stole $40 million in crypto after compromising the computers of its top executives. Details of the hack weren't disclosed, but were allegedly caused by "a well-known attack vector." I would lay money that it has something to do with infostealing malware… let's wait and see! (via Bleeping Computer, @StepFinance_)
U.S. cyber weapons hit Iran: U.S. officials allegedly "digitally disrupted" Iranian air missile defense systems last year as part of the U.S. aerial raid on Iran's nuclear facilities. The cyberattacks are said to have blocked Iran from launching ground-to-air missiles in defense by targeting something like an edge device on the target's network (like a router or firewall), rather than a critical computer system inside the network. (via The Record)
Gov't to secure the edge: Speaking of… CISA has ordered federal civilian agencies to patch or replace outdated or no-longer-supported edge devices, citing ongoing exploitation by hackers associated with unfriendly countries and overseas adversaries. (via Nextgov)
Salt Typhoon hits Norway: Salt Typhoon, the Chinese-backed hackers who target phone companies and internet providers to spy on senior government officials and diplomats, is now targeting companies in Norway, per the country's latest threat assessment [PDF]. Meanwhile: AT&T and Verizon, two U.S. phone giants that were hacked by Salt Typhoon, are blocking the release of a report that might've explained how the hackers got into their systems to begin with. (via Reuters ($), Regjeringen.no, Cyberscoop)
Cops nix Flock over fears of fed abuse: A bunch more U.S. cities and regions have switched off their Flock surveillance cameras, citing fears that ICE and other immigration federal authorities can snoop on their license plate readers and track where people go. (via The Record, State of Surveillance)
Dutch data agency breached: The Dutch data protection agency and the country's judiciary were hacked, per a report in Dutch from local lawmakers, who blame a bug in Ivanti's Endpoint Mobile Manager (EPMM). Ivanti has already confirmed exploitation of a "limited number" of its customers, which could still feasibly be dozens or hundreds of organizations. (via @campuscodi, Cybersecurity Dive)
~ ~
THE HAPPY CORNER
Ding-DONG! It's time to smash that happy corner gong, and with gusto.
A good place to start is a bonus cyber-cat… if you can see them.

For the folks at the Washington Post who were laid off this week, the very excellent @runasand, whose consultancy firm Grannitt helps at-risk folks (like journalists!), is offering them pro-bono work for the rest of February to answer questions about digital security.
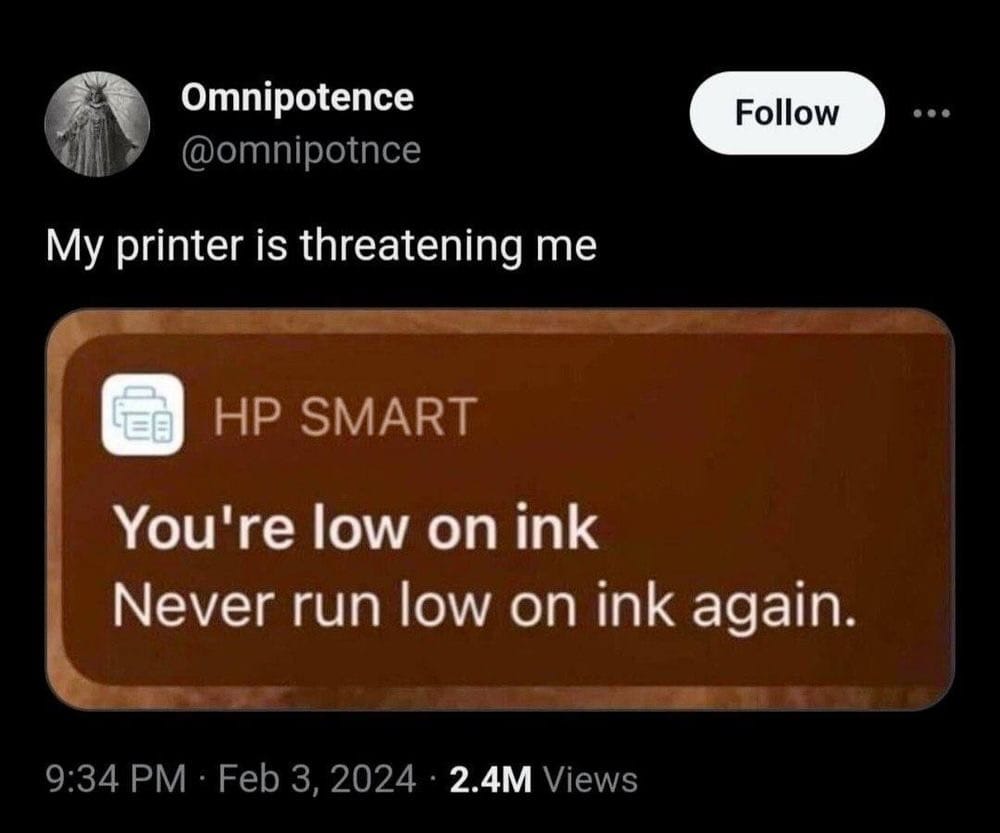
Moving on… let's hope printers never gain sentience, because:
And lastly, this week. The world is a hot mess right at the moment, but something quite nice recently happened at my home. A few months ago, a pigeon laid two eggs on our balcony, prompting my partner and I to document the whole process from hatching to their first flight, and what we learned in the process. Yes, this is now a cybersecurity, cat, and pigeon-friendly newsletter.

Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Bandito, who can be seen here sitting on the keyboard of his human while they were trying to get some work done on their day off. Look, sometimes a cat-in-the-middle attack is necessary! Thank you so much to Raïs for sending in!

🐈 Send in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And I'm outta here — and for the second week in a row, absolutely frozen. For those who are braving the sub-zero weather on the east coast and beyond, stay warm. I don't think I've ever been this cold whilst living in America...
Thank you for reading! I hope you have a great rest of your week. Please do get in touch (cybercats! fun stuff! news! what you're interested in!) — it's really great to hear from you. Drop me a line any time.
Dreaming of a warm sandy beach,
@zackwhittaker