this week in security — january 11 2026 edition
THIS WEEK, TL;DR
Founder of pcTattletale pleads guilty to hacking and selling spyware
TechCrunch ($): For subscribers who read my dispatch in December, here's why the tide is turning in the fight against consumer-grade spyware, aka stalkerware. In a rare bit of good news to start this week's newsletter, a U.S. stalkerware maker pleaded guilty on Tuesday to hacking and the sale and advertising of surveillance products for illegal uses. Feds were investigating Michigan-based pcTattletale founder and chief executive Bryan Fleming as far back as 2021, and eventually brought charges against him after an undercover operation found he helped people hack into people's phones to plant spyware. This is the first successful criminal prosecution of a stalkerware maker in more than a decade, which could open the floodgates for more prosecutions and criminal action against others. (Disclosure: I wrote this story!) Fleming shut down pcTattletale after a hack and data breach in 2024, and is expected to be sentenced later this year.
More: DocumentCloud | The Record | Ars Technica | The Register
Hackers threaten to post thousands of New Zealanders' health data
The New Zealand Herald ($): A data breach at Manage My Health, a website that hosts a third of New Zealanders' health data, was breached on December 29. Hackers reportedly demanded a ransom of $60,000 to prevent the release of 430,000 patient documents affecting 127,000 people, or some 6-7% of the site's 1.8 million users. Manage My Health said it fixed a bug that allowed the data theft. The New Zealand government sought an injunction to prevent "anyone from accessing, storing, broadcasting or publishing" the stolen data, not that ever stopped cybercrime… but does make it trickier to notify people. That's the second-known breach injunction in recent days, after Neighborly said a large database of members, including precise location data, was posted on a criminal forum.
More: Manage My Health | Reuters ($) | Bloomberg ($) | RNZ | DataBreaches.net
Inside ICE's tool to monitor phones in entire neighborhoods
404 Media ($): The good folks at 404 Media obtained materials about how ICE uses a social media and location-based surveillance system called Tangles (made by a company called Penlink), which ICE paid $2 million in September for access, per Forbes ($). In a nutshell, Tangles is "designed to monitor a city neighborhood or block for mobile phones, track the movements of those devices and their owners over time, and follow them from their places of work to home or other locations." This surveillance tool relies on location data obtained from the apps that people install on their phones (which sells your data to brokers), as well as the ads that they see. (Using an ad-blocker can help!) As it involves buying the data, ICE and other authorities can use this tool without a warrant and without judicial oversight. As folks across the U.S. took to the streets again this week to protest ICE, Wired ($) has its non-paywalled guide on how to protest safely while protecting your privacy and safety.
More: Wired ($) | EFF | @evacide | @jasonkoebler
Iran cuts off internet amid nationwide protests
Associated Press: On Thursday, the internet across Iran collapsed, according to several internet monitoring firms Kentik and Cloudflare, and others. By the end of the week, it was clearer why. The Iranian government, which maintains a tight grip on the country's web access, said it enacted a mass internet outage amid demonstrations across the country in major cities and beyond, as crowds took to the streets to protest the country's economy, human rights abuses, and more. With the country largely in digital darkness right now, it's not exactly clear what's happening on the ground — except that these protests are huge, on a scale not seen before. Iran has major cyber capabilities in its arsenal, and the U.S. has vowed to strike if Iran keeps killing protesters (which is rich coming from the Trump administration these days). It's worth keeping an eye on Iran.
More: BBC News | TechCrunch ($) | NBC News | DW ($)
~ ~
THE STUFF YOU MIGHT'VE MISSED
ClickFix attacks are devious, dangerous, and can hack you in an instant
this week in security ($): In my latest blog, I dive into how ClickFix attacks can trick unsuspecting victims into effectively hacking themselves by pasting malicious commands into their terminal. These attacks are increasingly effective and dangerous, as they can hack you and steal your sensitive data, like your passwords, in an instant. With hands-on examples of real-world ClickFix attacks, I show you exactly what to look for. Like this:
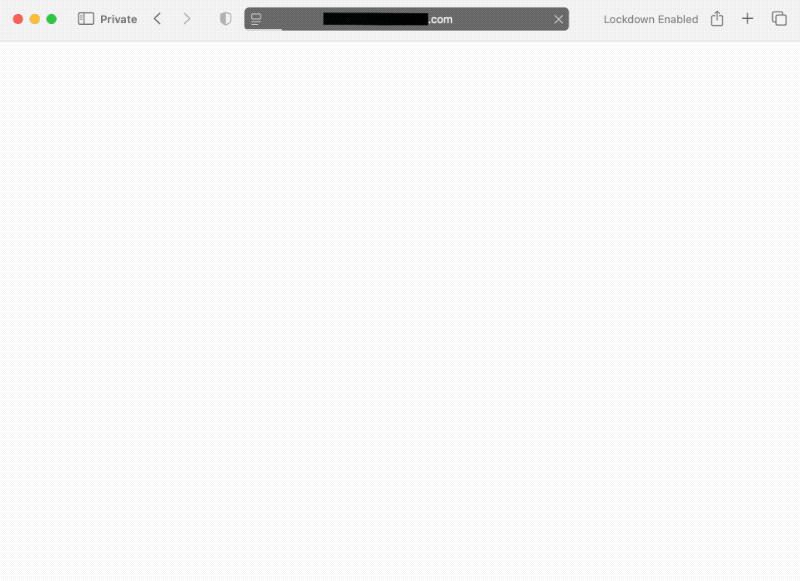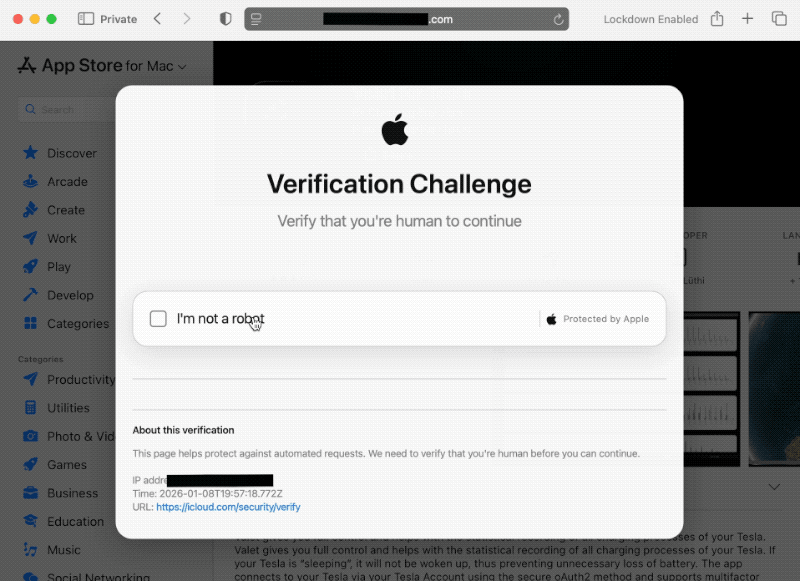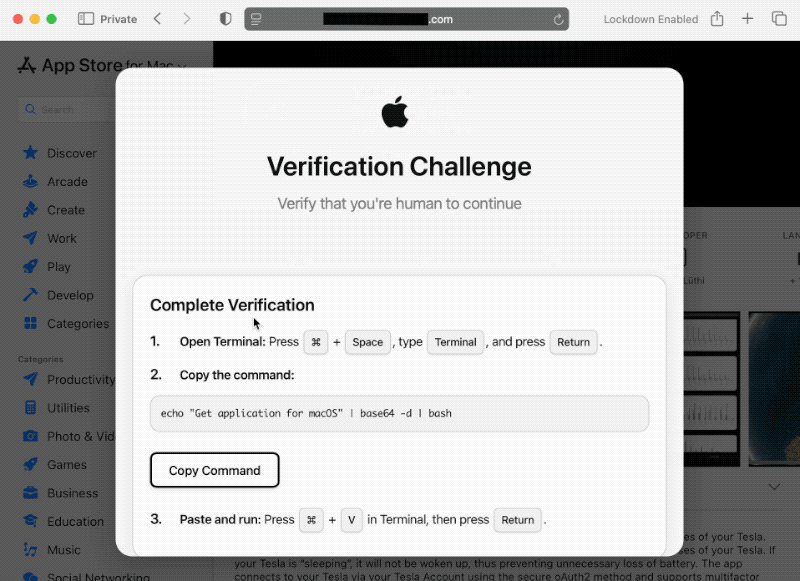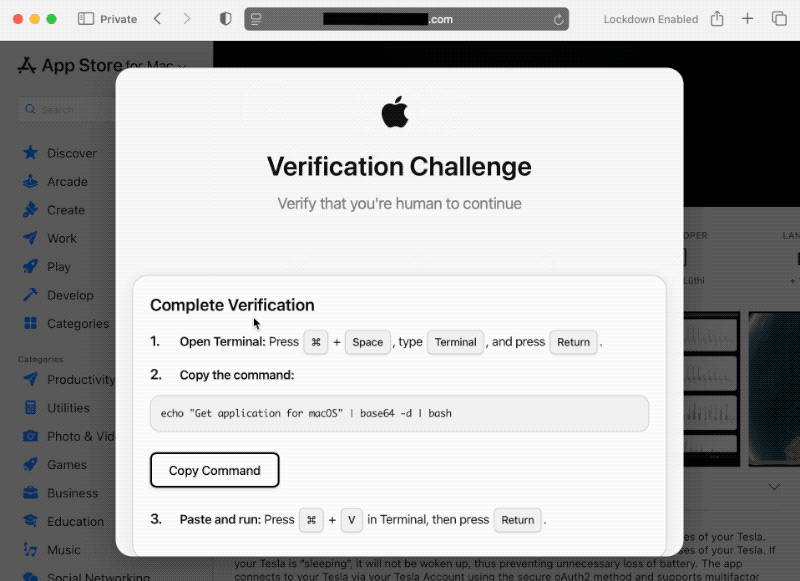
Instagram leak exposes some profile data amid uptick in password reset requests
The Verge: Users are reporting an uptick in password reset emails from Instagram, but Instagram said to basically ignore them. In related news: @haveibeenpwned obtained a cache of largely public data allegedly stemming from an Instagram API leak. About 6.2 million records had an associated email address or phone number.
ShinyHunters get played by security firm, leaks hackers' details
Resecurity: The prolific hacking group known as Scattered Lapsus$ Hunters, a coalition of groups made up of mostly teens and young adults, claimed it hacked cyber firm Resecurity. Just one problem with that… they hadn't; the hackers broke into a honeypot storing fake data (whoops), prompting Resecurity to fire back by dropping 105 pages of intelligence on one of the group's top known hackers, John Erin Binns (aka IntelSecrets). Resecurity went public with its dossier on Binns because he was indicted but remains at large in Turkey, likely due to his citizenship. More analysis from DataBreaches.net.
Hackers are using 'ragebait' in phishing lures
Simo Kohonen / LinkedIn: The next time you get a suspicious-looking email that sends you off in a rage, think again! Simo Kohonen found "ragebait" used in a phishing lure that aims to trick a victim into clicking a link to a phishing page in order to take action against something obviously repugnant. Per Silent Push last year, this looks like a PoisonSeed campaign, which relies on hacking compromised accounts of email sending giants (think SendGrid) to send phishing emails. @neurovagrant has more and historical passive DNS data to check out for network defenders!
SpyX stalkerware operation traced to Chinese tech firm
maia arson crimew: Not to be outdone by the pcTattletale news, @crimew.gay has a new blog post digging into SpyX, a phone spying stalkerware operation with over 1.5 million registered users, linked to a Chinese tech firm called Gbyte and its founder.
Security pros: 'Sophisticated' breaches often stem from boring problems
/r/cybersecurity: In this Reddit thread, security professionals discuss some of the boring ways that "sophisticated attacks" actually happen — all too often, it's something incredibly basic that was missed long ago. It's worth remembering that the basics in cybersecurity matter, and to not believe everything a data breach notice tells you (or misses altogether).
Flock exposed a private key dozens of times that spilled internal data
Nexanet: Security researchers found 53 instances of Flock exposing a hardcoded private key that allowed access to internal data, such as information from police departments, 911 incidents, and surveillance camera locations of 12,000 law enforcement deployments. Flock, if you recall, has a nationwide system of license plate scanning cameras, but can't seem to stop leaking access to its own systems.
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis and more, including:
ClickFix attacks are devious, dangerous, and can hack you in an instant
Thousands of North Koreans have secretly infiltrated US and European companies as remote IT workers
Banning TP-Link won't save America from its own terrible cybersecurity
~ ~
OTHER NEWSY NUGGETS
Brightspeed breached? Fiber broadband provider Brightspeed is investigating a claim of a breach by hacking group, Crimson Collective. The hackers (known for previously hacking Red Hat) claimed to have exfiltrated one million records from Brightspeed, including customers' personal information. (via Bleeping Computer, SecurityWeek)
Critics pan Pegasus paper: NSO Group's not-so-transparent transparency report [PDF] is out, but seems to have fewer details about human rights abuses carried out using its surveillance tools. Critics slammed the report as mere window dressing at a time when the Pegasus spyware maker is now under U.S. ownership, with an eye towards seeking permission to operate within the U.S. borders… which means potentially spying on Americans. (via TechCrunch ($))
New spyware, who dis? A new South African spyware maker has been revealed. Intelligence Online ($) reports the firm sells to a slew of governments, including Mexico, Venezuela(!), and the Myanmar regime. (via @vaspanagiotopoulos)
Illinois admits years-long lapse: Illinois' health department confirmed a years-long data exposure affecting over 600,000 people. The state said it's unclear if anyone accessed their personal and health data (presumably because it didn't keep logs). (via NPR Illinois)
Sedgwick govtech unit hacked: Sedgwick Government Solutions, which provides claims solutions and technology to many U.S. government agencies, said it's investigating a breach. A ransomware gang claimed to steal 3.4 gigs of data. (via Bleeping Computer)
TriZetto breach blows up: At least dozens of healthcare providers who rely on TriZetto, a Cognizant-owned company that helps doctors offices and hospitals bill patients for services, have so far notified their patients of an upstream data breach. TriZetto processes close to 3 billion healthcare transactions annually, and as such handles huge amounts of health data and patient Social Security numbers. Cognizant is facing multiple lawsuits following the disclosure of its 2024(!) incident, in which details remain murky. (via Bloomberg Law ($), Planned Parenthood)
Salt Typhoon hacked Congress: The Financial Times ($) reports China's Salt Typhoon hacked the email accounts of at least four congressional committees, including those overseeing armed services, intelligence, and foreign affairs. The Trump administration has taken largely a fingers-in-ears approach to the China-backed hacks, amid firing gobs of cyber staff across the federal government, and beyond. (via Reuters ($), Techdirt)
~ ~
THE HAPPY CORNER
*breathe in*... and out. This is the happy corner, and everyone is welcome in this little oasis of calm and joy.
The venerable @hacks4pancakes, a top-notch digital forensics expert in the ICS and operational technology (OT) networks space, has an excellent blog post with top tips and recommendations for OT cybersecurity students who want to break into the field. Lesley is the best of the best, so soak up these wise words.
TIL: Germany's BND intelligence service were snooping on the calls of then-U.S. President Barack Obama aboard Air Force One, apparently without permission from then-German Chancellor Angela Merkel, per a new book by Die Zeit ($) deputy editor. Apparently, the satellite links between the plane and space weren't encrypted properly. This was around the time that the NSA/Edward Snowden surveillance scandal was kicking off in 2013.
Is 2026 the year that Linux desktop goes mainstream? The Verge ($) thinks it might be, and is checking it out. (Plus: bonus cybercat in this post!) I remember when I was younger and Linux was… well, not the easiest to get around. But luckily, these days, the onramp to the wonderful world of open-source operating systems is far easier than you might expect — and certainly better for you in the long run than the AI-generating slop of Windows 11. More words from Notebookcheck.
And lastly, this week, a brief moment of bliss.
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Boo, who can be seen here reminding you — with all the love in the world — to do the security basics: use a password manager, two-factor all the things, and keep your devices up-to-date, and give me chin scritches... Wait... nice try! Thanks so much to Cathy M. for sending in!

⚠️🐈⬛ Please send in your cyber cats! 🐈⬛⚠️ The bank of cyber-cats is low and I fear an imminent drought. If you have a snap to send in of your cat (or non-feline friend), please do! Send in an email with their photo and name and they'll be featured in a later newsletter!
~ ~
SUGGESTION BOX
And that's it for this week — phew! Enough of that craziness. Onto next week's whatever-it'll-be. I'll be back next Sunday with everything you need to know from the week in cyber, plus more.
Thank you so much for reading this edition (and for subscribing!). If you want to get in touch with anything for next Sunday's newsletter, please drop me a line. It's always really nice to hear from you, and helps me find things I might not ordinarily see!
Enjoy your week, I'll catch you later.
@zackwhittaker