this week in security — january 18 2026 edition
THIS WEEK, TL;DR
FBI searches home and seizes devices of Washington Post reporter
Washington Post ($): The FBI raided and searched the home of a Washington Post journalist Hannah Natanson on Wednesday morning as part of an investigation into an alleged leak of classified information by a government contractor. Filed under "not good" on the ol' U.S. democracy downward slide. This is a major escalation from Trump's first term, when he used the Justice Department to secretly obtain the phone and email records of journalists at The Washington Post, The New York Times, and CNN, to advance government leak investigations. The public (and the Biden DOJ) only found out after Trump left office, prompting Biden's AG Merrick Garland to ban the practice. The PRESS Act would've codified that DOJ policy into law, with near-universal bipartisan support — but Sen. Tom Cotton blocked its passage and the bill failed. Trump's new AG Pam Bondi reversed Garland's policy early in Trump's second term, and here we are. Why target the press like this? Because it tries to prevent not just government leakers, but anyone, from trying to disclose wrongdoing and corruption — which these days, well, we all see it so brazenly in the open! Secure your comms. Don't let them chill you. Sunlight is the best disinfectant.
More: The New York Times ($) | CJR | NPR | CNN | @kyledcheney
Iran internet shutdown crosses one week, as protests continue
Scottish Herald: Iran's internet briefly spluttered back online in limited capacity on Saturday, more than a week after the Iranian regime shut off the country's internet amid nationwide anti-government protests. It's the longest ever shutdown in Iran, and one of the most prolonged outages in world history. The internet shutdown shut out the media, and tried to hide some of the horrendous brutality by pro-government forces. During the outage, Iranian disinformation networks masquerading as angry Scots on social media disappeared overnight. Starlink satellite connectivity is active in places, but Iran was said to be jamming satellite connectivity. It's not clear why the internet is recovering exactly, but hopefully we'll hear more from the ground this week.
More: Rest of World | TechCrunch | BBC News | AFP | @realhackhistory | @dougmadory
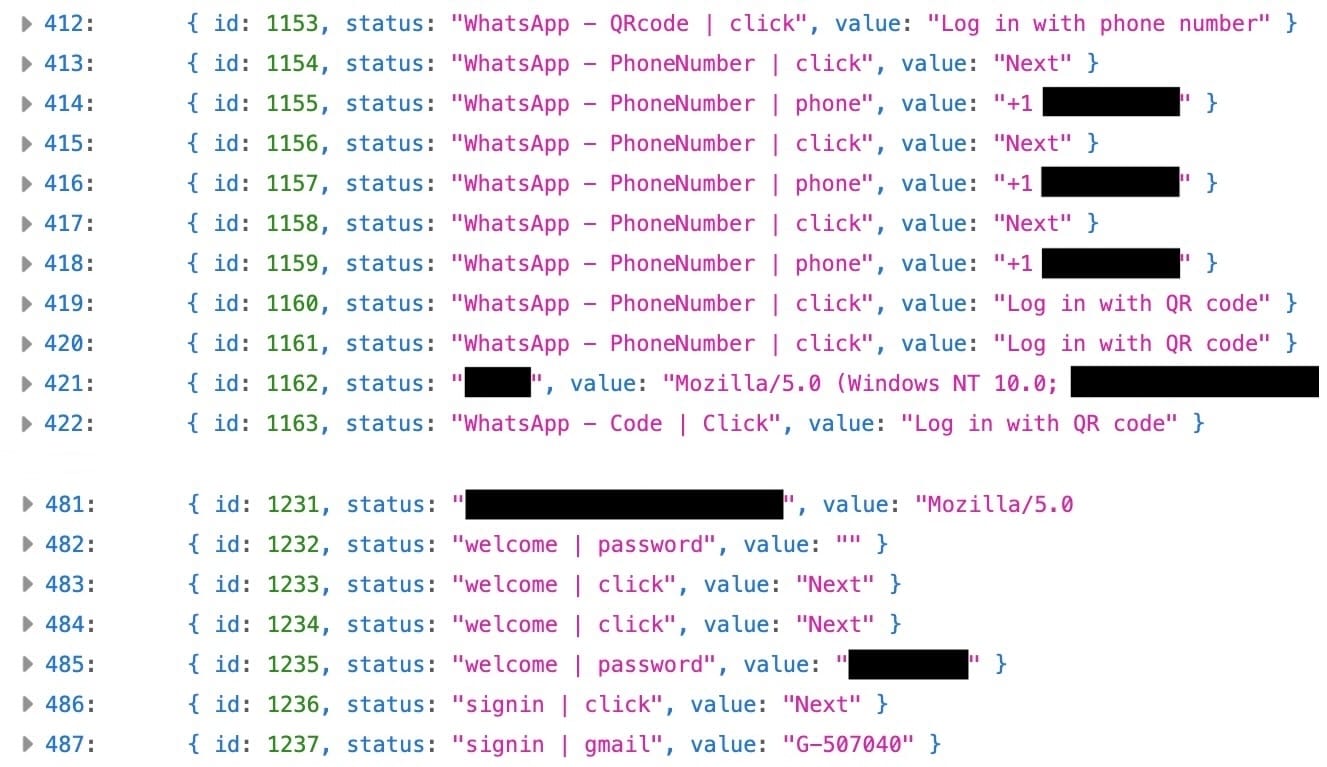
Inside a hacking campaign targeting high-profile Gmail and WhatsApp users across the Middle East
TechCrunch ($): Staying with Iran… somewhat adjacently… A phishing campaign going round this week targeted folks involved in Iran-related activities. U.K.-based Iranian activist @NarimanGharib received a phishing link by WhatsApp and shared details with TechCrunch. I grabbed a copy of the phishing page's source code. With the help of experts, I dissected this credential-stealing campaign and explored its surveillance capabilities, including the ability to steal a person's location data. A bug in the code allowed me to view some of the stolen data that the attackers had collected from its victims, including their email addresses and passwords. That data included the boss of an Israeli drone maker, a Lebanese cabinet minister, and a journalist, among others. It's not clear who's behind the campaign, whether Iranian state hackers, cybercrims, or both. (Disclosure: I wrote this story!)
More: GitHub | @NarimanGharib | @runasand
Police unmasked millions of surveillance targets because of a Flock redaction error
404 Media ($): Surveillance giant Flock is going after a website called HaveIBeenFlocked, in large part because Flock ultimately flucked up after police departments failed to redact license plates when releasing public records requests. As such, the site's database now lets anyone search 2.3 million license plates from unredacted Flock audit logs and millions more subjects of police searches. Flock reacted terribly to this scandal of its own making by complaining to the site's web host. Flock also reacted by starting to limit the data it produces when police search its systems. It's Flock's latest security lapse, after leaving cameras exposed to the web and failing to secure leaked logins.
More: MPR News | Reuters ($) | WABI 5
Millions of headphones vulnerable to eavesdropping bugs
Wired ($): At least 17 headphone models — including devices made by Sony, Jabra, JBL, Nothing, OnePlus, Soundcore, and others — are vulnerable to a flaw found in Google's implementation of its Fast Pair one-click Bluetooth pairing protocol. Researchers found that exploiting the bug (tracked as CVE-2025-36911, aka WhisperPair) allowed them to hijack some of the affected headphone models in about 15 seconds while within Bluetooth range of a target. The attack allows the disruption of audio and phone calls, and the ability to live-listen from a victim device's microphone. Google's own Buds Pro 2 and some Sony models have their own distinct flaw that allows the grabbing of a person's location via their Google account. Wired ($) does a great job explaining this messy flaw; getting the issue patched across a broad range of devices has been a challenge from the sounds of it.
More: WhisperPair | Ars Technica | @agreenberg | @lhn
~ ~
THE STUFF YOU MIGHT'VE MISSED
Thousands of n8n instances online remain vulnerable to max-severity bug
Bleeping Computer: A 10/10 max severity flaw in open source workflow platform n8n, which allows users to connect various apps together, is exposing some 50,000 vulnerable instances as of the time of this newsletter send. n8n is a central automation hub, which often stores API keys, OAuth tokens, database credentials, and more, so it's an attractive target for hackers. There's no workaround, but a software update mitigates. More tracking data from the good folks at @shadowserver.
SmarterMail critical bug allows unauthenticated code execution
Singapore CSA: Buckle up for another spicy one, as a critical 10/10 flaw in popular email software SmarterMail permits unauthenticated file uploads (such as webshells or malware) to any location on a vulnerable web server. More than 6,400 vulnerable servers remain online, per @shadowserver. The bug write-up from watchTowr Labs is worth the read, along with added analysis from Cyberwarzone.
U.S. cargo tech giant exposed shipping systems and customer data to the web
TechCrunch ($): Bluspark Global isn't a household name, but it's a tech firm that handles global shipping for hundreds of large companies. Eaton Zveare found five (yes, five!) separate 10/10-rated flaws, including plaintext passwords and an unauthenticated API, allowing unrestricted access to its shipping platform and its customers' data going back decades. Despite weeks of trying to alert the company to the bugs, the company failed to respond to the researcher's efforts, and so he contacted me. I got a response, at last! …from the company's law firm. SIGH.
Cisco finally ships fix for bug under attack by China
The Register: Enterprise tech maker Cisco took a month to fix — you guessed it — a perfect 10/10 bug. The company said it now has fixes for its Email Gateway and Secure Email and Web Manager, which suspected Chinese spies have been hacking for at least a month. I'm surprised there's anyone left to fix the bugs after so many Cisco layoffs…
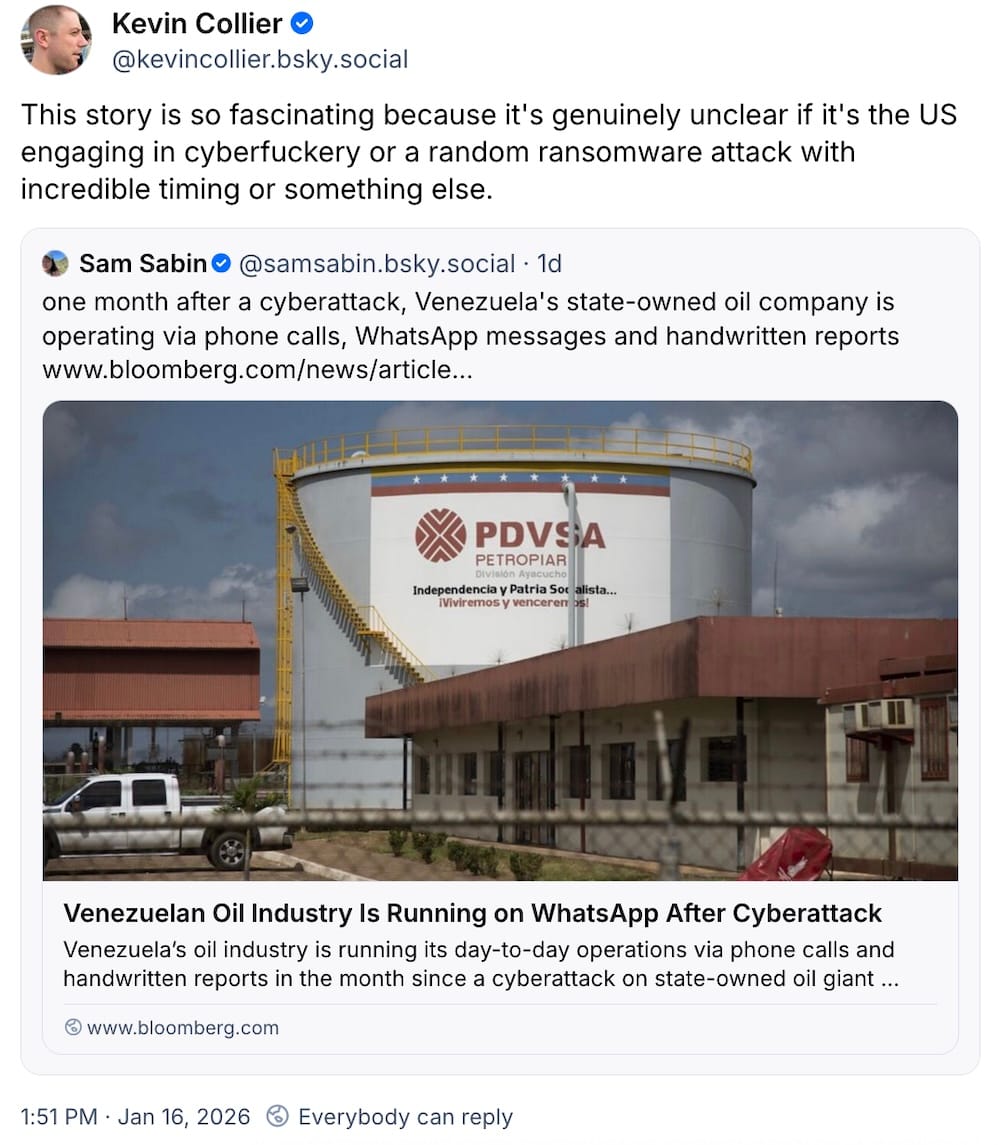
Nobody is sure if the U.S. switched off Venezuela's power during Maduro's capture
Ars Technica: Wild reporting by The New York Times ($)... if true… as U.S. sources tell the paper that the operation to capture Venezuelan president Nicolás Maduro earlier in January was aided by a cyberattack that switched off electricity for most residents in Caracas for several minutes. But the details are extremely thin, so much so that some are pushing back on the claims amid lacking evidence, compared to previous cyber-related power outages in Ukraine (twice), for example. Ars Technica's @dangoodin writes that there's a good reason for skepticism: Venezuela’s government said U.S. missiles were "at least partially to blame." Meanwhile: In confirmed cyber news, Venezuela’s oil industry is running its day-to-day operations via phone calls and handwritten reports following a December 15 hack on state-owned oil giant Petróleos, per Bloomberg ($).
Black Basta leader now one of EU's most wanted by German authorities
Hakan Tanriverdi: A year ago, reporters with Der Spiegel ($) and Der Standard ($) identified the admin of the prolific Black Basta ransomware group, a hacker called Oleg H. (aka Tramp). Oleg escaped a courtroom in Armenia in 2024, and remains on the run. Now, Oleg finds himself on the EU's most wanted list, thanks to a nudge by German authorities. (Internet Archive backup link in case the site is slow for you, too.)
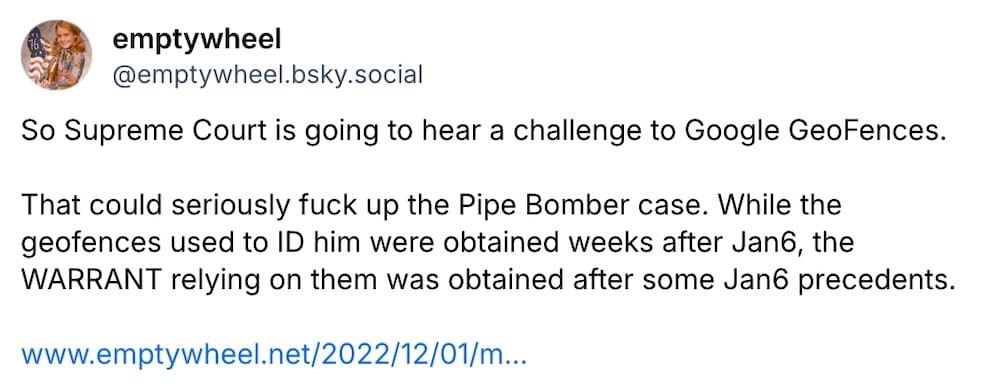
U.S. Supreme Court to hear legality of geofence warrants
SCOTUSblog: Interesting development, as the U.S. Supreme Court said it will hear a challenge [PDF] to the government's use of geofence warrants. These are essentially speculative search warrants that allow cops to dumpster-dive databases at Google (and other location-grabbing companies) to obtain the identities of people who were close to a crime scene at the time it was committed — often under the guise of trying to find the suspect. As you'd expect, these warrants ensnare entirely innocent people (more from me from 2024). Rendering geofence warrants illegal would be a good move for privacy, but could upend a ton of ongoing criminal cases — so all eyes on Chatrie v. U.S, which is expected to be heard before the court later this year.
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more, including:
TriZetto failed to stop hackers stealing Americans' health data for a year
ClickFix attacks are devious, dangerous, and can hack you in an instant
It's far too easy to find leaked passports and driver's licenses online
Thousands of North Koreans have secretly infiltrated US and European companies as remote IT workers
~ ~
OTHER NEWSY NUGGETS
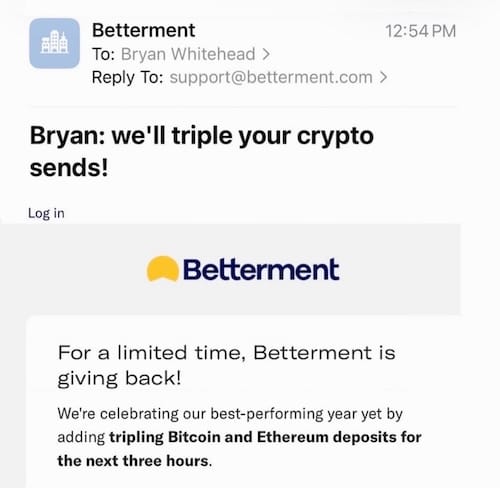
Betterment hacked, hid notice: Hackers broke into systems run by fintech firm Betterment to send fake correspondence to unsuspecting customers, claiming that the company will triple the value of whatever crypto they unwittingly send to a wallet controlled by the hackers. Betterment notified affected customers, but hid its breach notice with a "noindex" tag so nobody could find it. (via TechCrunch ($), @bryan)
Cyberattack fails to disrupt Poland's power: Poland's energy minister Milosz Motyka told reporters that a massive cyberattack in December aimed at disrupting the comms links between renewable installations and power distribution operators ultimately failed. Poland seemed to imply Russia may have been to blame. (via Reuters ($))
@ihackedthegovernment pleads guilty: A mystery guilty plea from a Tennessee man who admitted to hacking into the Supreme Court's electronic filing system also hacked several other U.S. government agencies and then posted about it on his Instagram page. The handle of that Instagram account? I kid you not: @ihackedthegovernment. Just absolutely stellar opsec, no notes. (via TechCrunch ($), @seamushughes)
New week, new university breaches: Bronx-based school Monroe University confirmed hackers stole sensitive personal and health data of 320,000 people during a 2024(!) cyberattack. Bleeping Computer adds Monroe to a growing list of schools that have been hacked of late. Also: The Victoria Dept. of Education was also breached, which allowed hackers to steal data of current and former students in the Aussie state. (via ABC AU)
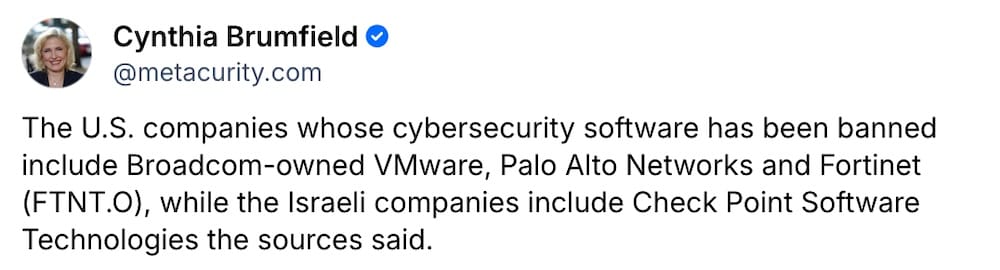
China dumps U.S., Israeli cyber software: Beijing has told Chinese firms to stop using U.S. and Israeli-made cybersecurity software, citing national security concerns. Security software often relies on being deeply hooked into the operating systems of the devices they protect, hence the concern. The U.S. banned Kaspersky in 2024 for similar-ish reasons. (via Reuters ($), @raphae.li)
FTC says no GPS for GM: The Federal Trade Commission banned carmaker GM and its OnStar subsidiary from selling drivers' location data for five years after collecting gobs of data without owners' explicit consent. GM sold the data to insurance firms, which used the information to hike the costs of people's premiums. (via FTC, Bleeping Computer)
Apple readies Background Security Improvements: Apple device software testers were shipped a new update this week introducing Background Security Improvements, which Apple says doesn't contain any actual fixes but could deliver patches in the future without having to restart a device. Not sure yet how different this is to Apple's Rapid Security Responses. (via 9to5Mac, @aaronp613)

Grubhub hacked: Food delivery giant Grubhub confirmed it was hacked, but details of the breach remain limited. The ShinyHunters hacking group is said to be extorting the company, but wouldn't comment. (via Bleeping Computer)
DOD to feed secrets to Musk's racist chatbot: Elon Musk's racist and antisemetic chatbot, under fresh fire for helping X users generate sexualized photos of women and children, will soon operate inside the Pentagon's classified network. Secretary of Defense Pete Hegseth said data will be fed from intelligence databases into Grok's AI systems. [internal screaming intensifies] (via AP News)
~ ~
THE HAPPY CORNER
And with the news done and dusted, let's find some peace… in the happy corner.
A little sprinkling of good news from the U.K., as the government has backed down from its plan to introduce mandatory digital ID cards across the country. Some close to 3 million people in the U.K. objected to the move, becoming one of the most submitted petitions to date.
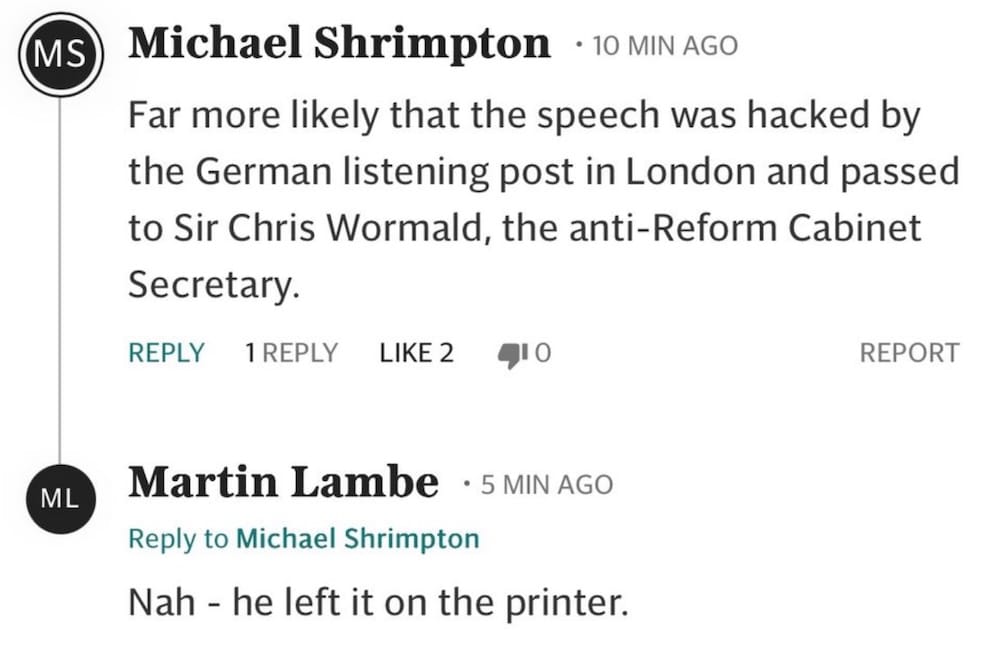
Thanks to @ciaranm for spotting this exchange between two political journalists, who inadvertently summed up pretty much the entirety of infosec throughout history.
And, it's not quite Doom, but running this tiny SimCity-style game on a Raspberry Pi is pretty impressive! Nice work, @chrisdiana.

Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat pupper is Eleanor, who can be seen here looking absolutely shattered after a busy day hacking her human's cybersecurity defenses with her pet crocodile. A formidable duo! A big thanks to Sam H. for sending in!

🐈⬛ Keep sending in your cyber cats! Thanks to everyone who submitted a cyber-cat last week. Keep 'em coming! Send me an email with a photo of your cat (or non-feline friend) and name, and they will be featured in a future newsletter!
~ ~
ONE LAST THING...
Are you a security researcher or journalist? Dissent Doe at DataBreaches.net and yours truly with this week in security want to hear from you! This is the last call to take our survey, which explores the state of legal and criminal threats faced by researchers and reporters. We plan to close the survey later today (January 18, 2026).
Please take our survey! We'll report the findings in the coming weeks.
~ ~
SUGGESTION BOX
Going once... going twice... thrice..? And we're done! I'm calling time on this week's seemingly never-ending stream of cyber news. Let's do it all again next Sunday!
Thanks so much for reading and subscribing. If you haven't made the leap to becoming a paying subscriber of this newsletter and blog, come and join in! And do get in touch if you want me to dive into a news story during the week, or an even deeper look into a security topic or two. I'm always keen to hear what you're interested in learning about!
Until next, take care and enjoy your week.
Catch you later,
@zackwhittaker