this week in security — january 25 2026 edition
THIS WEEK, TL;DR
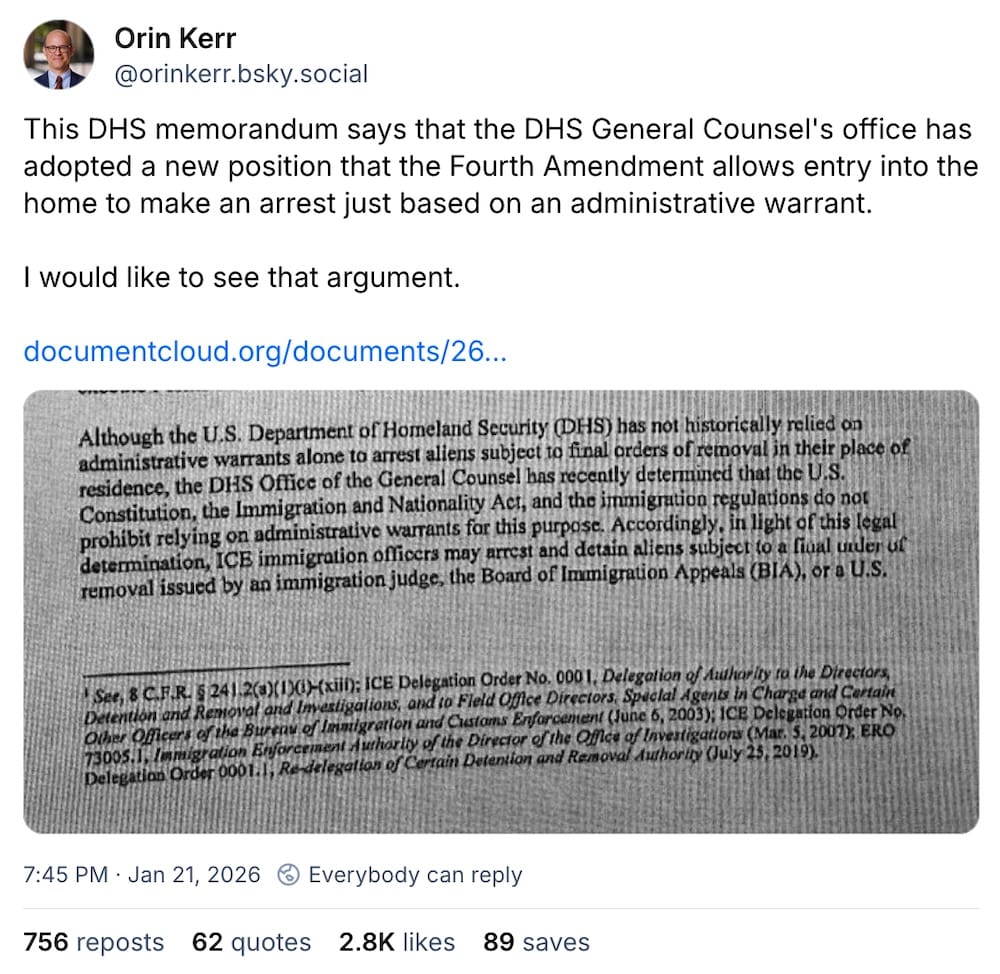
DHS says ICE agents can enter homes to make arrests without a judge's warrant
Associated Press: We start this week with an obscure but important one… the Fourth Amendment. It's the core pillar of the U.S. Constitution that prevents the police and feds from randomly searching your home and seizing your stuff, both in the real world and the digital realm. Well, Homeland Security has torn off a huge corner of U.S. constitutional law with its top lawyer relying on a secret interpretation of the law since mid-last year(!!), claiming that ICE doesn't need a judge-approved warrant to boot down someone's front door and arrest someone. Yeah, let that dumbassery sink in for a hot second. The Trump administration's approach to the rule of law (all the while pulling FBI agents from investigating actual crimes) is troubling as it ignores hundreds of years of past precedents. Where does this leave say, the future of device and data security? Just because DHS says it can do something doesn't make it legal, though it won't stop the agency from trying. A U.S. judge already contradicted (albeit indirectly) the ICE memo, per Wired ($), saying ICE violated the constitution by entering someone's home to arrest them without a court's approval. To assume this isn't a wider effort to undermine longstanding American norms would be as delusional as thinking that they could ever actually succeed — it just requires enough people to resist the obvious lawlessness.
More: Lawdork ($) | Lawfare | USA Today | @brendannyhan
Trump admin. says DOGE may've misused Social Security data
The New York Times ($): The thing that we said would happen only went and happened. Thanks to the wanton abuse of power by the world's richest idiot Elon Musk and his band of incels, there's a greater than zero chance that some or all of the U.S.' Social Security data is now in the hands of a group whose efforts include trying to "overturn election results in certain States." A government court filing [PDF] this week admitted that two DOGE staffers may have accessed sensitive Social Security data, which was ruled by a court to be off-limits at the time, and shared with the group, though the government can't be sure. The two unnamed staffers are facing Hatch Act referrals, which prohibits certain political activities of federal employees.
More: TechCrunch ($) | Politico ($) | Nextgov | NPR | CNN
Failed cyberattack on Poland's power grid used Russian wiper malware
Zero Day: So, about that failed cyberattack in Poland that I mentioned last week. It turns out it was actually a much bigger deal. European cybersecurity firm ESET obtained a copy of the "wiper" malware used in the attack, which ultimately failed, and attributed its use to Sandworm, a notorious hacking group with Russian intelligence. ESET said Sandworm tried to use the data-wiping malware to destroy computers critical to Poland's power grid, some 10 years almost-exactly after Sandworm's first major cyberattack took out Ukraine's power in late 2015. Poland said the cyberattack, if succeeded, could've cut the power and heat to 500,000 homes across the country during the dead of winter.
More: Poland government | Reuters ($) | ESET | TechCrunch ($) | @kimzetter
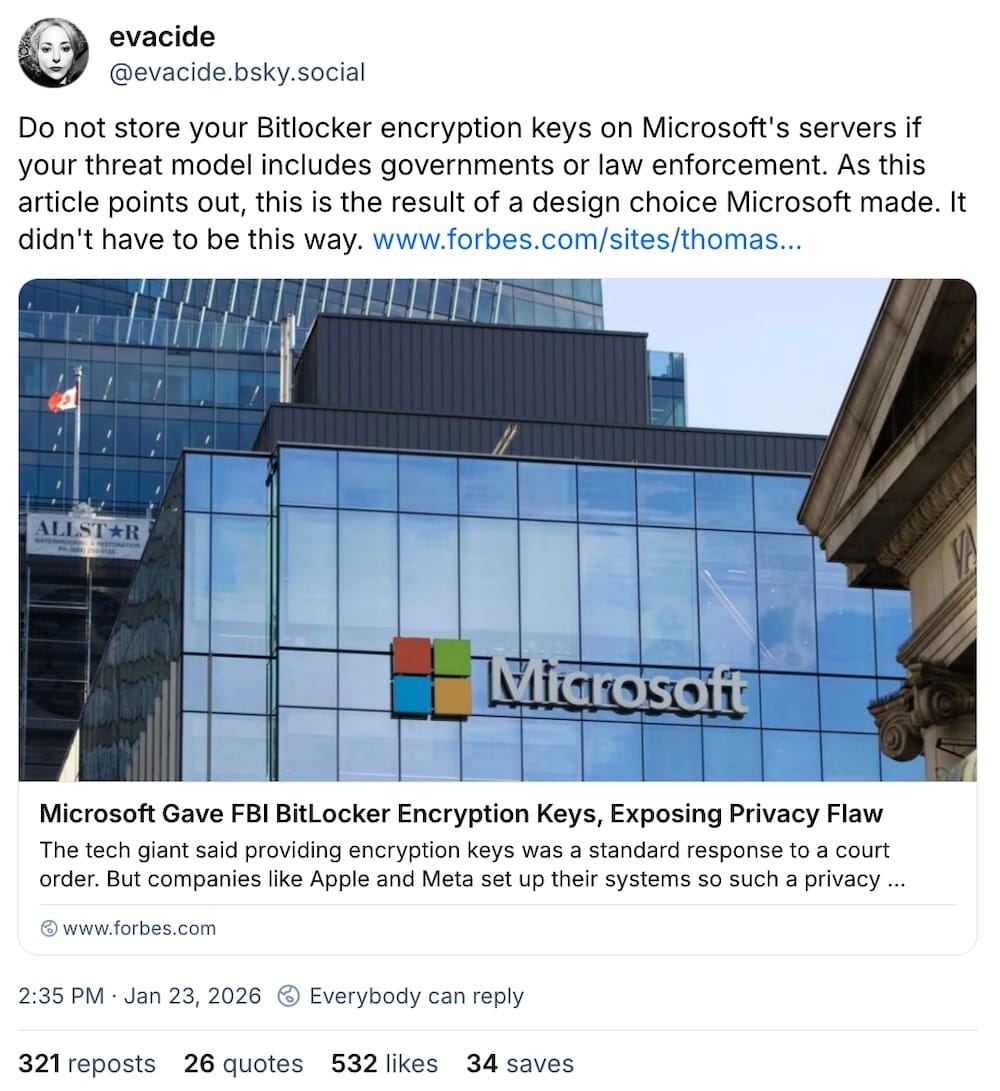
Microsoft gave FBI a set of encryption keys for suspects' laptops
Forbes ($): In response to a demand by feds last year, Microsoft handed over the encryption keys to unscramble the data on several laptops belonging to suspects in a fraud investigation. The demand was successful because Microsoft, by default, allows Windows users to upload their BitLocker encryption key to their online account in case they ever get locked out. But since this encryption key is in Microsoft's control, the feds can also swipe a copy for themselves. Microsoft now said it receives around 20 requests each year to unlock people's hard drives. Sen. Ron Wyden, a rare tech and privacy hawk, called Microsoft's ability to turn over its customers' encryption keys to the feds "simply irresponsible," especially when the company has the ability (like other tech giants) to lock themselves out of their customers' own data. Adjust your threat models accordingly!
More: Kandit News | Shotack & Associates | @matthewdgreen
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
THE STUFF YOU MIGHT'VE MISSED
Signal president says AI agents pose a risk for encrypted apps
Bloomberg ($): AI agents, which are software bots that act somewhat autonomously on a user's behalf (what could does go wrong?) are posing a major risk to encrypted apps, such as Signal, according to the nonprofit's president, Meredith Whittaker. The argument is that if you give an autonomous agent root access to your computer, which they require in order to do their job, this access "can be hijacked," said Whittaker.
Printer memory caught contractor who allegedly leaked classified data to reporter
The Intercept ($): The government contractor who allegedly leaked classified information to a Washington Post reporter was caught because he printed papers from the classified network. It wasn't hidden printer dots this time… but simply the printer storing a copy of every printed file ever printed. The charges are likely to stick, given the evidence, but this shows the feds likely had no reason to search the home or devices of the reporter who allegedly received the files (which, thanks to the First Amendment, isn't a crime).
SmarterMail bug under attack (again) two days after bug fix
watchTowr Labs: Security researchers suspect malicious hackers reverse-engineered a bug fix that aimed to resolve a remote code execution bug in the popular email software SmarterMail. Within two days of the fix landing for CVE-2026-23760, it was under attack — again — allowing the force-resetting password of admin accounts and granting access to the user's mailboxes.
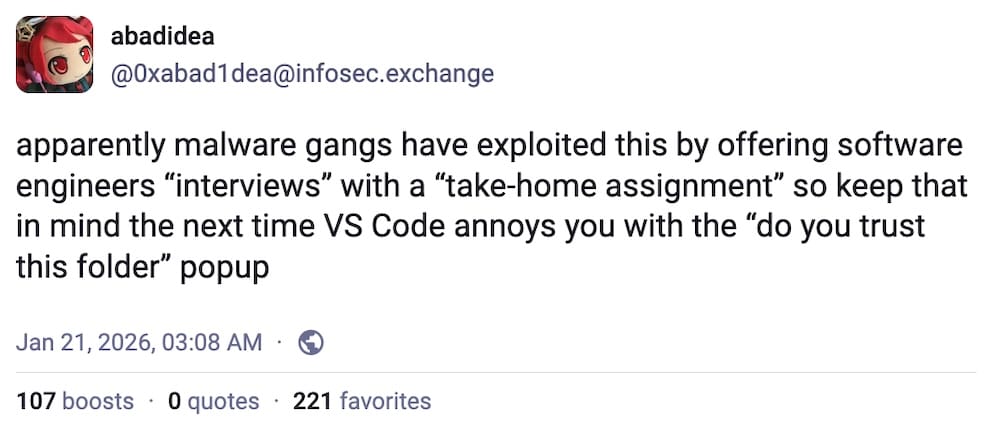
Hackers abusing Visual Studio Code to remotely run code on dev's computer
runjak.codes: Devs (and job hunters), beware. Attackers are trying to infect developers using Visual Studio Code by tricking them into allowing malware to run on their machine, sometimes under the guise of a job interview. Thankfully, @mushu caught this one, reported it, got the repos taken down, and blogged about it. This is a common technique used by North Korea, per Jamf. (If you're interested in reading more about the North Korean threat, I have just the deep-dive for you.)
ShinyHunters use voice phishing to target major SSO providers
Bleeping Computer: The ShinyHunters hackers are back with a new leak site, this time targeting a wave of companies with their voice phishing skills. By impersonating IT helpdesks, the hackers try to trick employees into entering their credentials and two-factor codes into fake-looking single sign-on (SSO) portals, such as those provided by Google, Microsoft, and Okta. From there, the hackers have direct access to company systems and databases for theft and eventual extortion. As part of this campaign, the hackers say they hit SoundCloud, Crunchbase, and Betterment.
~ ~
OTHER NEWSY NUGGETS
Brits cozy up to China on cyber: After more than a decade of having a digital and diplomatic frenemy relationship, the U.K. and China have reportedly started a new "cyber dialogue" that aims to lower tensions between the two countries. It's the first time that the two countries have set up a dedicated channel for senior government staff on both sides to discuss cyberattacks. (via Bloomberg ($))
Ireland mulling cops using spyware: Ireland's justice minister said the country will move to amend its 1993-dated eavesdropping laws so cops can use spyware, bringing a whole new range of devices into the government's surveillance scope. Since many apps are end-to-end encrypted and prevent law enforcement from snooping, often the only way for cops is to directly tap into the suspect's phone. (via Irish government, The Register)
Under Armour breach involves 'sensitive' data: Clothing and fitness data giant Under Armour confirmed to me that it was breached, but that the company was still investigating, after a hacker posted 72 million records online that were later given to Have I Been Pwned — which is a good thing, since Under Armour hasn't notified its customers about the incident. After I obtained some of the stolen data, Under Armour told me (disclosure alert!) that at least some of the stolen data was "sensitive," but wouldn't say what data, or how many people this affected. (via TechCrunch ($), Associated Press)
U.K. Lords nuke VPNs for kids: The U.K.'s House of Lords passed a provision that would "prohibit the provision of VPN services to children in the United Kingdom." This is to stop kids from skirting mandatory age-checks, which were set up as the government's lazy way of trying to prevent harm from social media giants (rather than taking on the giants themselves). It's unclear if the lower House of Commons will approve the measure. (via Tom's Guide, U.K. Parliament, @alecmuffett)
Dream wish list for cybercrims: Another massive database of stolen credentials has been found online. This so-called "dream wish list" for criminals contains close to 150 million usernames and passwords, likely collected via infostealer malware. This includes millions of accounts for Facebook, Gmail, and cryptocurrency platforms. (via Wired ($))
Google sends spam sky-high: If you, like me, were wondering why Gmail's spam filters suddenly crapped out on Saturday, you aren't alone. Google confirmed the issue is now fixed. (via The Verge ($), Google Status)
~ ~
THE HAPPY CORNER
And here's your much-needed moment of calm for this week. Welcome back to the happy corner.

Heading first over to Amsterdam to see what the Dutch are up to...
Speaking of Europe… now might be a good time (especially for those stuck inside due to the U.S. snow storm) to slowly wean your way off some of your favorite U.S.-based tech services. Thankfully there are plenty of global and European-based offerings that deserve your dollars euros, and European Alternatives is a great place to start.
In a new 2026 edition of What Can Doom Run On?, it turns out a pair of Pinebuds Pro earbuds can run the 1993 classic. Why? Why not! Stellar work here by @arin-s.
And lastly, this week. Pour one out for Gladys West, an absolute mathematical badass, whose work paved the way for the modern-day GPS satellite system. West passed away last weekend at 95. NPR dug in, looking at West's incredible work, much of it involved charting orbital trajectories and figuring out mathematical models of the Earth's shape that would go on to figure out where satellites had to be positioned in orbit. West apparently wasn't much of a fan of it herself. "I prefer maps," she said. Rest in power.
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Catherine the Great, who can be seen snooping on her human during a recent webinar... it's impossible to work under these watchful conditions! Many thanks to Izebel for sending in!

Pssp pssp pssp. Got two minutes? Send in your cyber-cats! Drop me a quick email with a photo of your cat (or non-feline friend) and name, and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's it for this edition of this week in security! As always, feel free to drop me a line if there's anything you see for next week's newsletter, or if you just want to get in touch to say hello.
Without any further ado, I'm off to spend the rest of the day indoors (and out of this epic snow situation) with my fellow human, huddle the cats, eat some snacks, binge watch some telly, and wait for all of this crazy weather to blow over.
Peace and love, my cyber friends.
@zackwhittaker