this week in security — january 4 2026 edition
~ ~
It was really nice to log back on after a much-needed two-week holiday break and new year with friends and family, feeling refreshed and ready to take on the world. Then, I woke up on Saturday to see a flood of news notifications about Venezuela, and my reaction — just like most of the world — was:

No major signs yet of cyber (as of the time of hitting send), but I'll keep an eye on whatever happens next both politically and internationally as things intersect with intelligence, and — yep — you guessed it, bad opsec. For now, let's move onwards to the rest of the news... *breathes aggressively into paper bag*
~ ~
THIS WEEK, TL;DR
'MongoBleed' bug allowing unauthenticated access to MongoDB databases under mass exploitation
Bleeping Computer: A not-so-happy Christmas for MongoDB customers who were left scrambling to patch a major bug in the database software. Details of the bug were revealed on Dec. 24, then days later, a security researcher published working exploit code, allowing anyone to leak sensitive memory data from web-facing servers running most versions of MongoDB for the past decade. The bug (officially CVE-2025-14847) is called MongoBleed for its similarity to CitrixBleed, in that it's easy to exploit over the internet. MongoDB's cloud-based Atlas customers are already patched, but that leaves around 80,000+ self-hosted, internet-facing MongoDB databases vulnerable to hacks. The U.S. and Australian governments are among those urging users to patch amid widescale global exploitation.
More: MongoDB | Cyberscoop | Ox Security | Censys | DoublePulsar ($) | Wiz
U.S. lifts sanctions for three executives linked to Predator spyware
U.S. Treasury: In a move that has alarmed privacy advocates and human rights defenders, the U.S. Treasury is removing sanctions for three executives involved with Intellexa, a consortium of spyware makers most well known for Predator — and the underlying mess it made by being used to hack into the phones of Greek politicians and journalists, as well as targeting members of the U.S. Congress. An unnamed Treasury official said the department had responded to a "petition request for reconsideration," and the trio had "demonstrated measures to separate themselves from the Intellexa Consortium," without saying exactly how. This comes as competing spyware maker NSO Group (behind the notorious Pegasus spyware) is now under U.S. ownership as it attempts to lift its de facto ban on operating in the U.S., which the Biden administration imposed. On the brighter side: TechCrunch's @lorenzofb has a guide on what to do (and who to ask for help) if you're targeted by government spyware.
More: The Record | Bloomberg ($) | Reuters ($) | Haaretz | TechCrunch
German hackers call for digital independence at annual Chaos Computer Congress
Euractiv: Hackers at the annual CCC hacker conference in Hamburg are starting to organize "digital independence days" in Europe to encourage and help users to move away from U.S. tech companies to regional alternatives. This comes as Silicon Valley increasingly and brazenly acts against people's best interests to defend their own profits. Belgium's spy chief warned (via the Financial Times ($)) that U.S. tech dominance has led to a major security threat, as it's "currently impossible” to store data fully in Europe. And yet the repercussions can be huge for those who fall on Trump's bad(der?) side, like, say, prosecutors of war crimes. It's genuinely chilling to hear that the U.S. can cut anyone off from the world's biggest tech providers and the international financial system, just because the U.S. houses so much of it. More from CCC online, and some favorites pulled out from users on Hacker News.
More: CCC 39C3 | Heise ($) | Irish Times ($)
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
THE STUFF YOU MIGHT'VE MISSED
Ubisoft shuts down Rainbow Six Siege X servers after hack
BBC News ($): Rainbow Six Siege X gamers can now play again after a hack prompted its maker, Ubisoft, to shut down its servers over the holiday break. Hackers gifted players millions of dollars in virtual currency, while also hurling insults at Ubisoft. Ubisoft has so far avoided calling this a security incident (though, by all accounts, it was). @GossiTheDog found one of Ubisoft's now-secured MongoDB databases on the internet, which may have been the culprit. More via The Gamer.
Leaked handbook details how cybercriminals operate romance scams
Reuters ($): Reporters at Reuters obtained a detailed guide by a Philippines-based cybercrime crew on how to carry out romance-related scams, commonly called pigbutchering, one of the most prevalent kinds of organized cybercrime today. The guide describes how the gang creates fake personas to lure in people, and how to handle targets who suspect a ruse. Knowing how these scams work allow researchers to reverse-engineer defenses and protections.
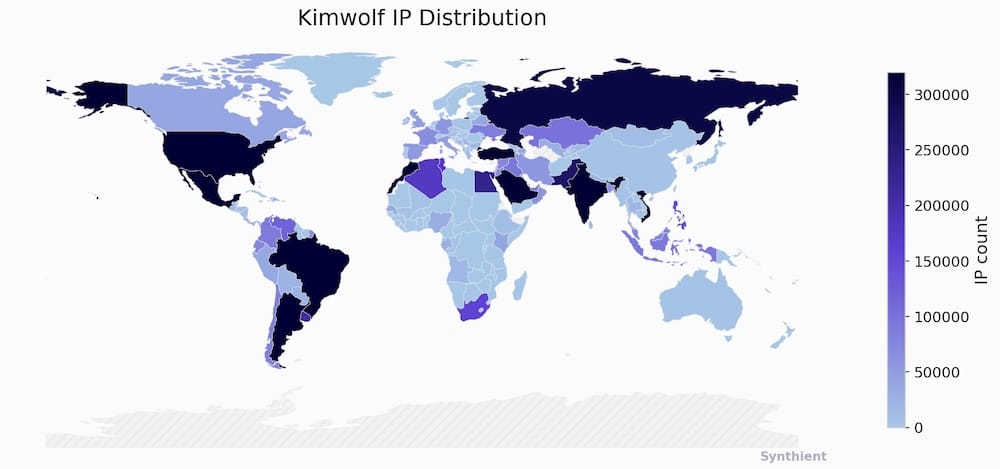
Kimwolf botnet has ensnared over 2 million hijacked W-Fi networks
KrebsOnSecurity: Independent security journo @briankrebs has a long read detailing the ongoing threat to home and residential networks from the growing Kimwolf botnet. The botnet works by compromising Android TV boxes, many of which ship with a default mode that allows remote access from over the internet. More than 2 million Android TV boxes have been compromised, lending some context to the scale of this botnet, allowing the malware to use its network's internet bandwidth to engage in ad fraud and crippling DDoS attacks. Synthient has a blog post about the campaign, and a checker to see if you're affected.
Fears mount that federal cybersecurity is stagnating, or backsliding
Wired ($): @lhn looks back at 2025 in federal cybersecurity under the Trump administration's first year of its second term. After months of layoffs and cuts, the situation looks dire. CISA rebuffed claims that cuts across the agency are affecting the U.S.'s cybersecurity posture (despite a raft of hacks last year affecting the U.S. government!), yet this seems to fly in the face of hard truths of actual reality.
Shai-Hulud supply chain hack led to $8.5m crypto wallet heist
SecurityWeek: More of the fallout from the earlier Shai-Hulud supply chain attack in November, which affected hundreds of developer projects, is coming to light. One popular crypto web extension, Trust Wallet, confirmed hackers used a private key stolen in November to subsequently publish a malicious update to Trust Wallet's web extension, allowing the hackers to steal secrets from ~2,500 users who logged in between Dec. 24 and Dec. 26. The hacks led to the theft of $8.5 million in user funds. Relatedly: Bloomberg ($) dug deep into "wrench attacks," aka real-world violence and physical robberies that seek passwords from crypto holders and high net worth individuals. “If we cannot hack them, we rob them," one of the robbers testified.
~ ~
OTHER NEWSY NUGGETS
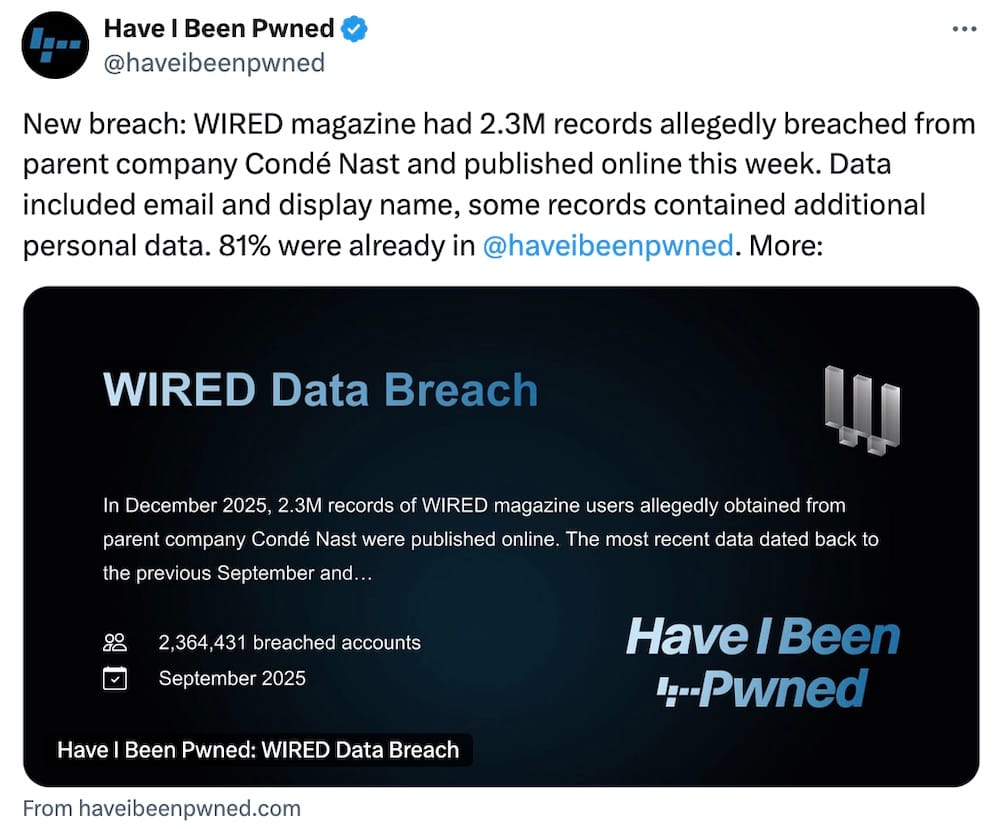
Condé mum on subscriber breach: The venerable Dissent Doe at DataBreaches.net disclosed a complicated breach involving 33 million user accounts associated with media giant Condé Nast. The hacker initially claimed to have only a few records but was unable to notify the magazine publisher, then later claimed to have stolen millions of records and were willing to leak the files. Condé still hasn't acknowledged the breach of email addresses, names, phone numbers, and more. Some 2.4 million records associated with Condé-owned magazine Wired were handed to data breach notification site Have I Been Pwned. (via DataBreaches.net, Bleeping Computer)
Researchers jailed for ransomware: Two security researchers who worked for companies that negotiate ransom payments for cyberattack victims have pleaded guilty to moonlighting for a notorious ransomware gang, ALPHV (also known as BlackCat). The pair face upwards of 20 years in prison for their involvement in targeting U.S. companies with the notorious ransomware group's malware. (via The Verge ($), Justice Department)
Coupang's $1.2B post-breach apology: Coupang, the "Amazon of Asia," will issue $1.2 billion in vouchers to apologize for its massive data breach affecting over 33 million customers. That's some $35 each for the hassle of having their personal information allegedly stolen by a former employee. (via Coupang [Korean], CNBC)
Aflac breach hits over 22 million: Insurance giant Aflac confirmed 22.6 million people had personal and health information stolen during a cyberattack disclosed in June. Several other insurance companies were hacked around the same time. Aflac said the stolen data includes Social Security numbers and government-issued ID documents. (via TechCrunch ($), Iowa Attorney General [PDF])
La space, le hacked: The European Space Agency confirmed a number of its external servers were compromised, which the agency says were used for "unclassified collaborative engineering activities." A hacker claims on a hacking forum to be selling some 200 gigabytes from the space agency's servers. (via @ESA, Space News)
~ ~
THE HAPPY CORNER
*keeps breathing into same paper bag* …Are we clear? OK. That's the news, and here is the mental palate cleanser you need — it's the happy corner.
Some excellent news for Californians, who can now enjoy some of the strongest data protection and privacy rights in the United States (not that there are many). The state's new one-stop-shop DROP tool allows state residents to block some 500 data brokers from selling their personal and identifiable information. More via ABC7 and The Washington Post ($) on how it works. (Thanks for the flag, @metacurity.com.)
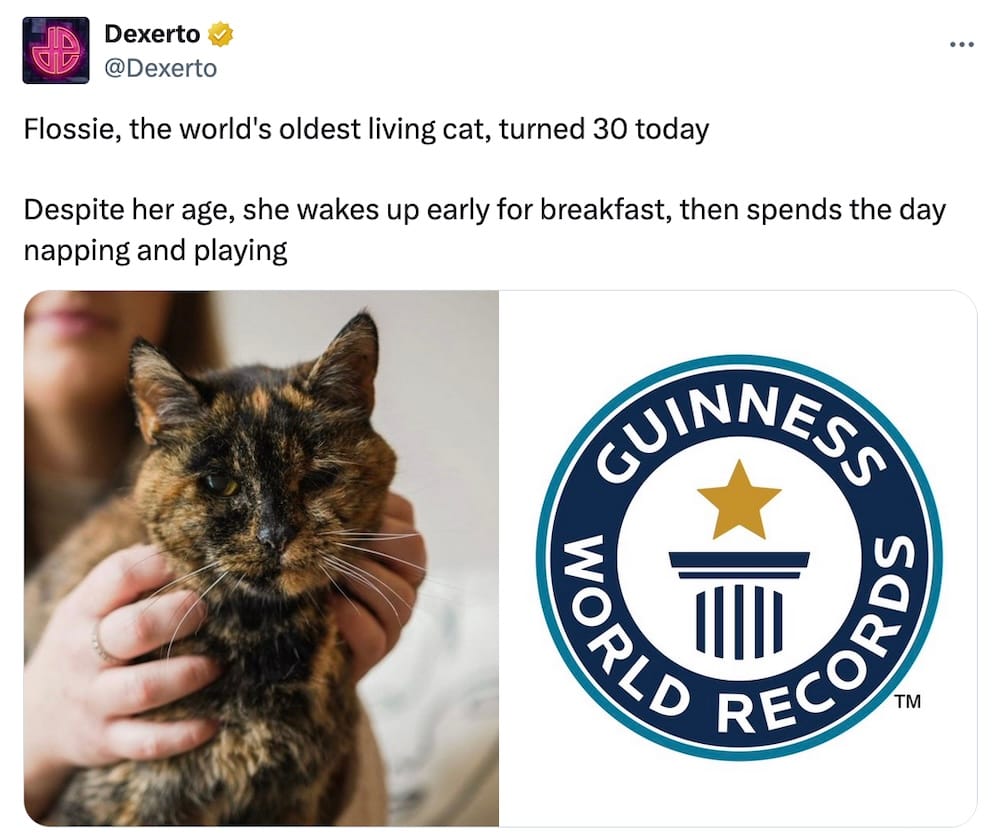
Bonus cybercat as the world's oldest cat, Flossie, turned 30 just before the new year. Happy birthday, Flossie! (via Dexerto)
@peturdainn welcomed 2026 in the nerdiest way possible (and there's code you can try!)
And, lastly… from me: Thanks so much to everyone who joined as a paying subscriber to ~this week in security~ during the last few weeks of 2025. As promised, I have donated 10% of all new annual Astonishing admin subscriptions during the month of December, plus a personal match from me, to a total of $240. This donation went to The Diana Initiative, a non-profit that is committed to helping all underrepresented people in infosec, and continues to do a ton of events and workshops to support its mission. I will reach out to the cybercat mug winners this week — look out for an email from me!
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat (and world traveler extraordinaire) is Findus, whose human tells me that he was found as a kitten in Florida, bottle-fed and nursed to health... then moved to New York with his new family, and now Bavaria, where he lives today with his adoptive brother Fuzzer. This is one incredible view, made only better by Findus himself. Thanks so much to Nick S. for sending in!

🐈 Please send in your cyber cats! 🐈⬛ Have a cat or a non-feline friend? Send in an email with their photo and name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
Thanks so much for joining me again. It has been... a week, for sure. I'll be back next week with your usual update from the last seven days in cybersecurity and more — with at least a couple of stories from me.
Please do reach out if you have something for next week's (or an otherwise upcoming) newsletter, like news, research, or other fun stuff that's caught your eye. It's always lovely to hear from you!
See you next,
@zackwhittaker