this week in security — november 16 2025 edition
THIS WEEK, TL;DR
Spyware maker NSO gets new U.S. owners to curry favor with Trump
Wall Street Journal ($): Israel-based spyware maker NSO Group is now under American ownership. Its new leadership, which includes Hollywood producer Robert Simonds (for some reason), hopes to restore the company's "battered reputation" following years of spyware abuses. NSO's new executive chairman David Friedman (pictured), who was the former U.S. ambassador to Israel and Trump's own bankruptcy lawyer, said he hopes the Trump administration is "receptive to considering any opportunity" that might keep Americans safe, a veiled push at getting its Pegasus spyware into the hands of the U.S. government. NSO's spyware has been used against ordinary people for years, so much so that the once-small pool of victims isn't so small anymore. Apple and WhatsApp said in response to the new NSO owners that they'll continue to defend their users, who are often targets of spyware attacks. I'm not sure you can repair a spyware maker's reputation; you only lean into its horribleness, like the government has done with ICE. All I can see are a bunch of gross, creepy, weirdo dudes who want to rifle through people's personal lives for profit. Sorry, but any claims of "fighting crime" don't fly anymore and haven't for a while.
More: The Guardian ($) | TechCrunch ($) | Jerusalem Post | @skirchy

EU considering weakening GDPR to placate AI firms
Politico: The European Union, in its infinite wisdom (sarcasm), thinks gutting the bloc's privacy and data protection rules — some of the strongest in the world — is its answer to not falling behind the global AI boom. EU officials want to sacrifice some of its GDPR rules so that certain categories of protected data, such as religious beliefs or health data, can be legally allowed to train and operate AI tech. The idea is that pseudonymized data (where data is obscured, not anonymised) can also be used to train AI. But we've already seen huge datasets like location data where that information can be identifiable. A lot of Europeans are already making their voices heard. Europeans worked really hard to get and keep GDPR, and while it's not perfect, it certainly shouldn't be whittled away. All eyes should be on the EU's anticipated November 19 announcement…
More: The Record | Tech Policy Press | AFP | The Register | Computerworld
U.K. suspends intel sharing with U.S. after Caribbean bombings
CNN: Let's take a slight detour from Europe to the Caribbean, where the U.S. has been illegally bombing alleged drug trafficking vessels in the region. Alleged, because we've seen no evidence of it yet, since the U.S. is literally blowing it up. But the U.K. entered the fray this week after it cut off the U.S. from its Caribbean intelligence sharing pact, amid concerns that its information has been used to bomb people without due process rather than — novel concept here — boarding their vessels and stopping them? This is the latest incident to strain the U.S. government's intelligence partnerships with its ever-dwindling global friendship group, aka the Five Eyes, and beyond. Relatedly, this week, The New York Times ($) reported that the FBI director Kash Patel made a promise to his U.K. counterpart, the director of MI5, about saving an FBI liaison's job — and flat-out broke it. Patel might as well crawl into a cave for the rest of time because that relationship is donezo.
More: Defense Post | Reuters ($)
Lawmakers say Democratic states are sharing driver's data with ICE
Reuters ($): Dozens of Democratic reps and senators have sent letters to governors of U.S. blue states warning them that their state governments are sharing driver's data with federal immigration authorities like ICE. This is in spite of some states offering sanctuary by not assisting federal authorities with enforcing immigration. A little-known loophole allows ICE to get near-realtime access through a third-party service called Nlets, which is run by police departments. ICE and two other DHS immigration enforcing agencies accounted for close to million queries of the database during the year prior to October 1. Only a few states have blocked access, like New York and Illinois. The lawmakers said that only the governors can stop the data sharing, and can do this at any time.
More: Ron Wyden | DocumentCloud | Nlets | TechCrunch | Fox 8 Baltimore
Researchers question Anthropic's latest research that an AI-assisted attack was autonomous
Ars Technica: Anthropic said it's seen the "first reported AI-orchestrated cyber espionage campaign" after detecting China-backed hackers using its Claude AI tools to target dozens of companies. But outside researchers had a more measured response to the findings, noting the limitations of the attack, notably that some of it was hallucinated or overstated, effectively preventing fully autonomous attacks. Cyberscoop's story is also a good balancer, and Volexity's own research this week looks at how LLMs are used in crafting phishing emails and malware development. AI has some uses — including malicious — but it's a long way from fully autonomous AI attacks.
More: WSJ ($) | BBC News | Cyberscoop | @sexabolition | @gregotto
~ ~
THE STUFF YOU MIGHT'VE MISSED
Interview with prolific Ukrainian hacker held in U.S. prison
BBC News: The BBC's @joetidy got some rare facetime with notorious Ukrainian hacker Vyacheslav Penchukov, aka Tank, who was on the FBI's most wanted list for a decade and is now serving a lengthy prison sentence in the U.S. after getting arrested in Switzerland back in 2022. Tank offers some rare insights into the cybercrime world, albeit from behind bars.
Scammers abuse ClickFix to gain access to a victim's device
Ars Technica: Hackers are ramping up their attacks that rely on tricking users into infecting their own Windows or Mac computer with malware, usually by way of a malicious web popup that hijacks the screen to look like a software update. The victim must complete a CAPTCHA, copying a line of code to the clipboard, which the victim must paste into their computer's terminal. Malware is then instantly downloaded onto the victim's computer capable of stealing their passwords and more. Microsoft has a good overview from August, and @GossiTheDog, too.
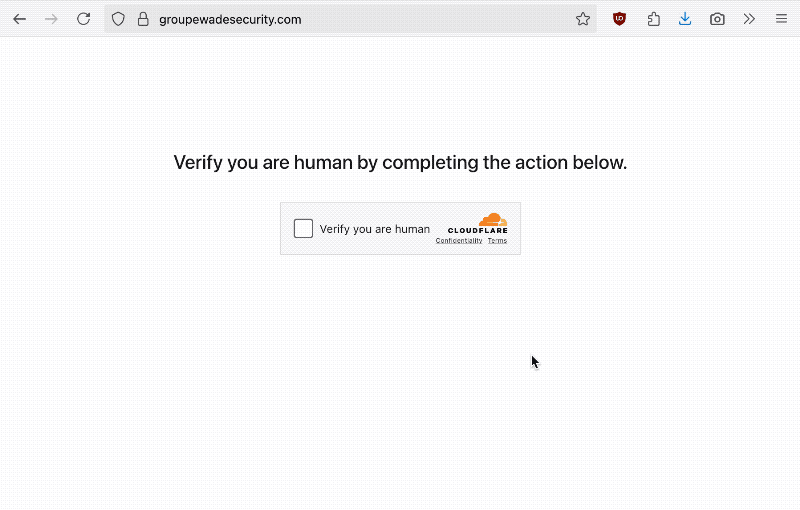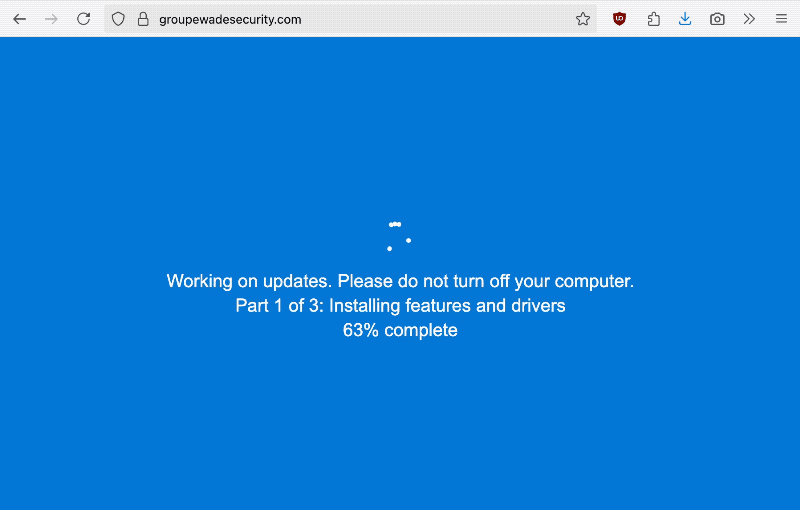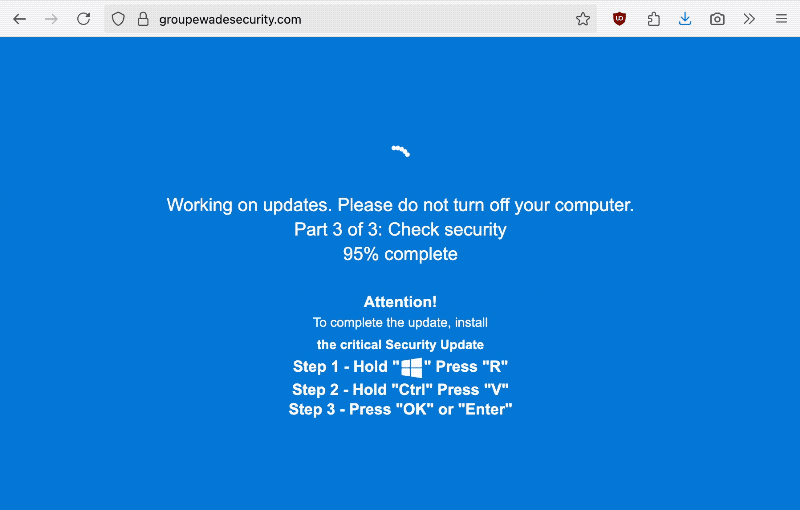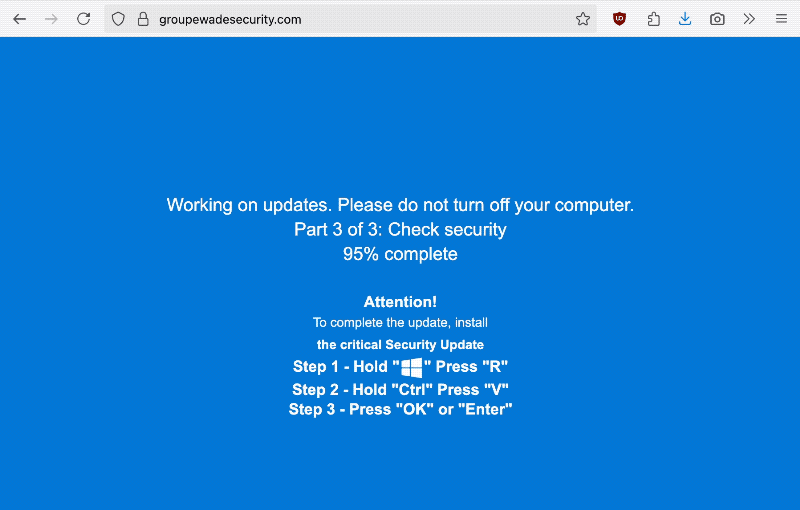
CISA says federal agencies hacked via Cisco ASA flaws
TechCrunch ($): CISA warned that federal agencies are not patching their networks sufficiently against exploits targeting Cisco ASA firewalls. CISA says the firewalls have been under attack since September, prompting the agency to order federal agencies to patch their systems. But some federal networks were "still vulnerable," as CISA said it was tracking "active exploitation” across the federal government. (Disclosure: I wrote this story!)
Open-source intel: Putin's many, many hideaway offices
John Scott-Railton / X ($): Using open-source intelligence, researchers believe that Russia's Vladimir Putin has multiple hideout offices around Russia that are meant to look identical. But little mistakes give the game away. Russia has one of the world's most persistent intelligence apparatus and yet can't seem to figure out interior design. Opsec is hard! (via @alburov, Svobodo Radio)

European police take down three cybercrime operations
Europol: Law enforcement in Europe is back with its third round of disruptions under Operation Endgame, which saw officers nuke a popular infostealer called Rhadamanthys (which exploded in usage after an operation hobbled close rival Lumma earlier this year), a botnet called Elysium, and a remote access trojan called VenomRAT. The "main suspect" was arrested, so that's promising, but as noted by TechCrunch, this is the latest whack-a-mole effort by cops to take down the sprawling and ever growing cybercriminal ecosystem. Have I Been Pwned loaded the dataset so you can check if you are affected.
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing-up for a paying subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
OTHER NEWSY NUGGETS
Synnovis notifies NHS of published data: Synnovis, a major pathology lab for the NHS across the U.K., is finally notifying affected NHS trusts that their patients' data was stolen during a 2024 ransomware attack. It took the lab over a year to pore over its stolen data, effectively paving the way for the NHS to alert affected individuals whose health data and lab results were stolen in the breach. (via DataBreaches.net, Digital Health)
Checkout rebukes hacker's ransom: Checkout.com said it was targeted by the ShinyHunters hacking group, which gained access to a third-party system containing customer data from 2020 and prior. It's unclear why the data was still stored there years later, but props to Checkout.com for publicly declining to pay the hackers' ransom and instead donating some of the ransom to cybercrime research. (via SecurityWeek)
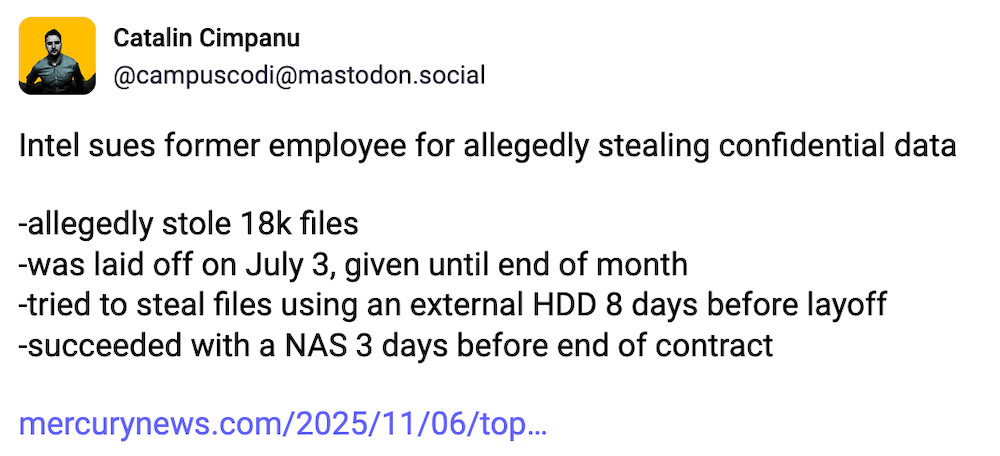
Intel insider data theft: Chipmaker giant Intel is suing a former employee who, just before getting laid off, allegedly took off with 18,000 internal company files, including some labeled "Intel Top Secret." The employee apparently used a network storage device. An interesting insight here for insider threats' watch. 👀
China's Typhoons down under: Australia's spy chief says China-backed Salt Typhoon is "probing" the country's telecom networks. He also said they've seen Volt Typhoon, the Chinese hacking group known for planting malware in critical infrastructure, and warned of the risk of potential future sabotage. (via Reuters ($), Bloomberg ($))
Princeton donor data popped: Princeton is the latest university to confirm a hack in recent months. This latest hack involved data on alumni, donors, and students, which contained personal information including names, contact details, and “fundraising activities and donations” to the school. Columbia and UPenn were also hacked earlier this year, though it's unclear if any or all are connected. (via Princeton, Bloomberg ($))
JLR breach hit U.K. economy: The cyberattack that took out Jaguar Land Rover's car production lines for several weeks earlier this year cost the company at least $220 million. The outage was cited as a reason for the slight slowdown in the U.K.'s economy over the past few months. (via Bleeping Computer, BBC News)
~ ~
THE HAPPY CORNER
Welcome back to the happy corner, where we have just one little item from the world.
A judge in Washington state has ruled (via 404 Media ($)) that police images taken by Flock surveillance cameras are subject to public records laws, despite efforts by cities and police departments to keep data associated with their surveillance tech private. Oh, the irony. Time to fire up the FOIA cannon!
Good news to share? Drop me a line! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cybercat special features Corina and Federico, who can be seen here carefully monitoring their domain from a highly privileged position (on the fridge!). No birds can penetrate this perimeter. Thanks to Jane C. for sending in!

🐈 Send in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a later newsletter!
~ ~
SUGGESTION BOX
And that's it for this week's newsletter. Thank you so much for reading. I hope you enjoyed this dispatch. I'll be back next week as usual with your roundup from the week.
If you have anything you want to share with me for the newsletter, please get in touch — it's a real joy to hear from you. And I'd never say no to you sending in a cyber-cat (or friend!).
In the meantime, feel free to get stuck into some of my articles. There's something for everyone. And if there's something you'd want more of, or for me to write about, please reach out. I'd love to hear what you're curious about and interested in across the world of cybersecurity.
Yeeting myself offline,
@zackwhittaker