this week in security — november 2 2025 edition
THIS WEEK, TL;DR
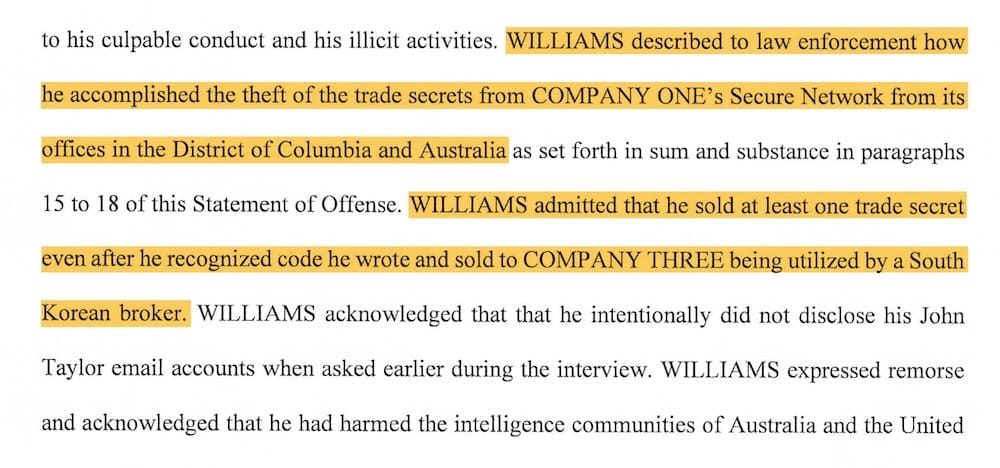
Ex-Trenchant boss guilty of selling eight exploits to Russian buyer
TechCrunch ($): And there it is, confirmation at last that Peter Williams, the former boss of Trenchant, the L3Harris unit that makes exploits and hacking tools for Western governments, was behind the theft of eight exploits to a Russian zero-day broker. On Wednesday, Williams pleaded guilty in federal court after @lorenzofb broke the news last week that prosecutors had accused Williams of the theft of unspecified "trade secrets." With Williams pleading guilty, we have some new details via @kimzetter, including that an exploit he sold to the Russian broker was being "utilized" by a downstream South Korean broker, but Williams still sold new exploits anyway despite the risks of getting caught. Williams allegedly made $1.3 million in proceeds from his crimes, which he converted into crypto and luxury items, like watches. This is an example of an insider threat that will no doubt be studied for years. Williams was trusted with the keys to Trenchant's kingdom, and subsequently stole a motherlode of hacking tools for Russia. The former Trenchant developer who was initially blamed for the leaks might want to hire himself a lawyer…
More: Wired ($) | CourtListener | Cyberscoop | Bloomberg ($) | Zero Day | Risky.biz | Lawfare | @lorenzofb
Telecom giants LG Uplus and Ribbon confirm cyberattacks
Korea Herald, Reuters ($): Two major telecommunication giants reported hacks this week, including LG Uplus in Korea, the country's second-largest phone provider and now the third Korean telco to have been hacked in recent months. LG notified the government of a breach months after the country's state cyber regulator tipped off that the company had been hacked. Meanwhile: U.S. telco giant Ribbon, which provides networking and phone services to enterprise giants and critical infrastructure, said in a 10-Q filing that hackers were in its systems for almost a year before getting caught. This comes in the same week that FCC chair and Trump sycophant Brendan Carr wants to scrap cyber requirements for telcos… because that's precisely what you do after your telcos were mass-hacked by the Chinese just a year earlier.
More: TechCrunch ($) | Mobile World Live | Reuters ($) | FCC.gov | Cybersecurity Dive
U.S. proposes banning TP-Link Wi-Fi routers, citing threat from China
Washington Post ($): Well, it looks like we're back on banning consumer tech again. This time, it is network equipment maker TP-Link that has drawn ire from the federal government over its alleged links to China, which the feds believe poses an automatic national security risk. TP-Link, for its part, says there isn't any risk as it spun off from its Chinese parent company several years ago. The ban, if it goes ahead, would be huge, given that TP-Link supplies some of the most popular wireless routers sold in the United States. This isn't the first time a major tech giant has been banned, or faced a ban. Cast your mind back to the U.S. government's ban of Kaspersky products over its links to Russia. TikTok has so far avoided a ban in the U.S. after its China-headquartered parent company sold off TikTok to a U.S. entity owned in large part by Oracle boss and major Trump donor Larry Ellison. All to say, there is precedent, but this time it's murkier since we still haven't seen any actual evidence of a national security risk.
More: Washington Post ($) | New York Times ($) | @joemenn
Canada says hacktivists are targeting internet-connected industrial control systems
Government of Canada: The Canadian government warned in a new advisory that hacktivists are targeting internet-connected industrial control systems, which are used in water, energy and critical infrastructure systems. The hackers are mostly doing it for the lulz, per the advisory, but the Canadian government warns that the attacks could have dire consequences. In two cases, Canada said hackers tampered with a water facility's pressure controls and created "potentially unsafe conditions" in a grain-drying silo. Many of these ICS systems are run by the private sector, so all the government can do is urge companies to take action before it's too late. Meanwhile: Sweden's power grid operator Svenska kraftnät confirmed a data breach, but said its power grid was unaffected. The provider didn't say what kind of data was stolen, or if the data belonged to customers. The Record has a little more. Fun fact: the power grid operator's Wikipedia page has just one section, titled "Criticism," and followed by a lot of footnotes. Beloved, it is not.
More: Svenska kraftnät | The Register | Bleeping Computer
~ ~
THE STUFF YOU MIGHT'VE MISSED
Azure is the latest cloud giant hit by a day-long outage
Wired ($): Not wanting to be outdone by last week's day-long AWS outage, Azure took its turn to take a big, happy, unscheduled sleep in the middle of the working day, forcing anyone who relies on Microsoft's cloud (actually a lot of people) to log off citing a digital snow day. Microsoft faced criticism for taking more than half an hour to disclose the outage.
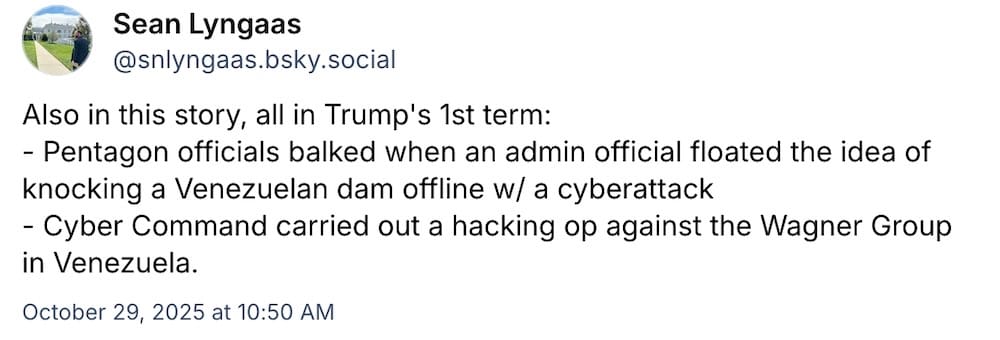
CIA hacked Venezuelan intelligence during Trump's first term
CNN: New reporting found that in 2019 during the last year of Trump's first term, the White House ordered the CIA to target and disable the computer systems used by Venezuelan intelligence. The cyberattack was part of covert action taken in an effort to oust Venezuelan strongman Nicolás Maduro from power. The news comes against the backdrop of blatantly illegal strikes in the Caribbean and Pacific against alleged drug traffickers, for which we've still seen no evidence. Some extra commentary via @neurovagrant and @snlyngaas.
Police charge group behind blackmail of top Italian politicians and business leaders
Politico ($): Reporters obtained police wiretap transcripts revealing that a corporate intelligence firm was engaged in a criminal plot to blackmail some of Italy's top political elite using a database full of kompromat. The database, dubbed Beyond, pulled together "hundreds of thousands of records from state databases," including suspicious financial transactions and criminal investigations, per the publication.
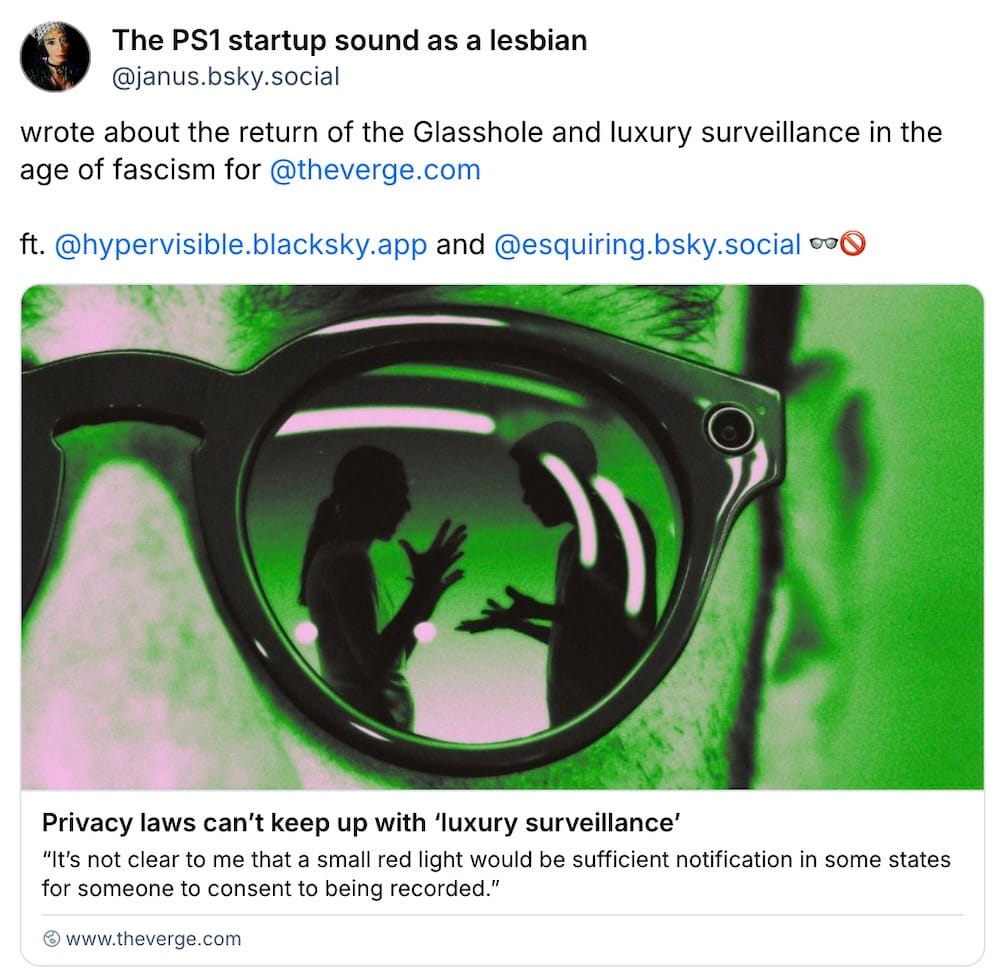
Privacy laws can't keep up with wearable surveillance tech
The Verge ($): Wearable snoop-tech is increasingly becoming a thing with Meta's camera-enabled glasses and other AI-enabled listening pendants, aka "luxury surveillance" devices, allowing ordinary people to record video and audio footage semi-covertly. The Verge asks: "How is any of this even legal — let alone ethical?" It's largely because laws can't keep up with the pace of snoop-tech. Citing experts, The Verge found that these days "social shaming" is the most powerful check and balance we have against non-consensual recording.
Flock cameras used to wrongly blame Colorado resident for theft, but the resident had their own evidence
Denverite: Speaking of surveillance tech… A Denver police sergeant called Jamie Millman accused a local resident of package theft by using Flock license plate cameras to basically guess that it was her (aka police laziness). But the woman strenuously denied it and hit back with mountains of her own evidence to show that it wasn't her, and took the dossier to the press to prove her innocence. Surveillance is easy; solving crimes is not. This story is enough to make your blood boil and lobby your municipality to enact stronger local laws.
Sending text messages to aircraft cockpits thanks to 'test:test'
Chaos Computer Club: The CCC said it was possible to view (and potentially send) text messages to cockpits of commercial planes by logging into ARINC OpCenter with the shockingly bad username and password combination of "test:test." The CCC reported the flaw to Collins Aerospace, the Raytheon-owned maker of aerospace tech (and airport check-in systems), but did not hear back. The test:test account was disabled soon after.
MIT pulls AI-related ransomware report after public debunk
Socket: Prestigious university MIT pulled the plug on a report claiming 80% of ransomware attacks were driven by AI, a claim that was widely panned as a load of tosh and bollocks. MIT retreated by taking the report down. The bigger issue here is that some CISOs will lap this up like it's fact.
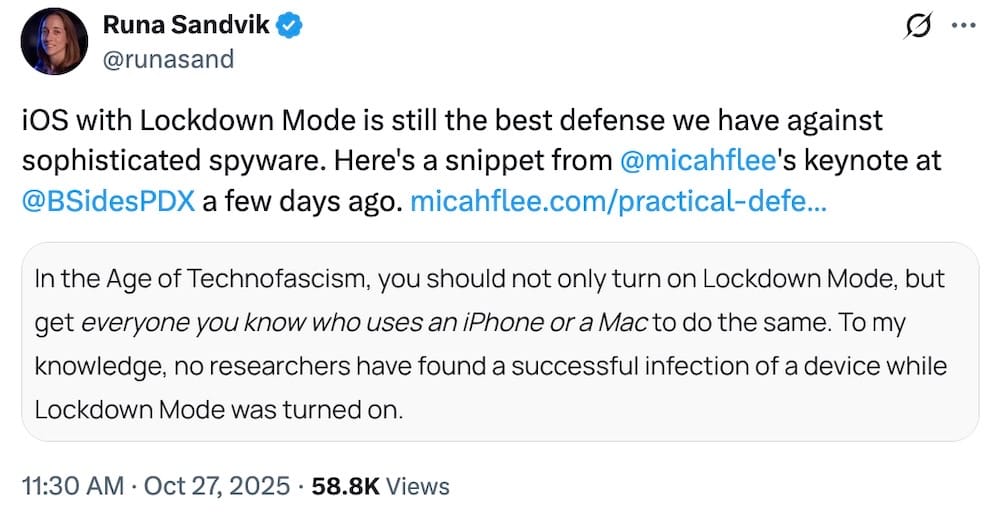
Journalist offers practical defenses against techno-fascism
Micah Lee: In October, Micah Lee gave a keynote address at BSidesPDX about practical steps that you can take against techno-fascism; that is, protecting yourself against surveillance and tracking while also helping your community. An absolutely vital read (and watch) for anyone and everyone who wants to take defensive measures. Per @runasand, who is another amazing digital rights defender, Lockdown Mode for Apple devices is one of your best digital defenses. (Google also has Android Advanced Protection, too!)
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing-up for a paying subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
OTHER NEWSY NUGGETS
Dems exposed top secret clearance holders: Democrats left an unsecured database exposed to the internet belonging to its DomeWatch program, used by prospective job applicants to upload their resumes. Some 450 people had top secret clearance, per the security researcher who found the database. See? You don't have to be inside the federal government to be terrible at security! (via Wired ($), Safety Detectives)
New spyware, who dis? The CEO of Milan-based surveillance vendor Memento Labs confirmed to TechCrunch that a newly identified Windows spyware called Dante, which was caught targeting victims in Russia and Belarus by security researchers at Kaspersky, does in fact belong to Memento. The CEO blamed one of Memento's government customers for getting caught using an outdated version of the spyware. It's not often that a spyware vendor actively confirms its tech was found used in active hacking campaigns. (via TechCrunch ($), Kaspersky)
Tata fixes flaw that exposed customer data: Tata Motors, one of the largest automobile giants in the world, confirmed it fixed a historical security lapse from 2023 that exposed internal and customer data. Eaton Zveare found Tata was using client-side decryption to hide its AWS keys, which allowed access to 70+ terabytes of internal and sensitive Tata data. Whooops. (via Eaton-Works, TechCrunch ($), @jagmeets13)
Tap, tap, (wire)tap, anyone still at NSA? Since the start of this year, the National Security Agency has lost more than 8% of its civilian staff as part of the Trump administration's ongoing efforts to cut the federal workforce, including NSA's top leadership, such as its director and top lawyer. The Record looks at some of the names floated to head the spy agency, which has gone more than a year without a permanent leader. (via @martinmatishak)
Cybercrime treaty? U.S. says nah: The U.S. has declined to sign a United Nations cybercrime treaty (with over 70 countries on board to date), which allows cross-border intelligence sharing, but critics say the treaty permits transnational repression and the erosion of human rights. The U.S. said it "continues to review" the treaty without giving a reason. (via The Record)
EY can't believe it wasn't secure: Security researchers found a four terabyte-sized publicly exposed SQL database belonging to consulting giant EY (formerly Ernst & Young). It's not clear for how long the database was exposed, but it's a reminder that it's not a question of if anyone found the database but how many found it. Neo had some nice things to say about EY's incident response, though. (via The Register, Neo Security)
~ ~
THE HAPPY CORNER
Pssst… can you hear that? Exactly. It's peace-and-quiet o'clock in the happy corner.
The good folks at 404 Media ($) tried out a pair of new Zenni lenses that make it more difficult for facial recognition systems to scan a wearer's face. By adding a pink sheen to the surface of the glasses, the lenses reflect infrared light, which can befuddle some face-scanning tech. While the glasses do technically work, they do have some functionality tradeoffs.

Data brokers might try to know everything about you, but it's not as "game over" as you might think. It's never, ever too late to start taking meaningful security and privacy steps to protect your identity and privacy online. The very excellent @yaelwrites joins the equally excellent @privacyguides to talk about what steps you can take to combat the data broker industry, such as using the Big Ass Data Broker Opt-Out List. An absolutely invaluable resource!
The new Tor Browser 15.0 has landed. The anonymity browser gets a few new features, plus a screen lock for Android users.
Thanks to @hacks4pancakes for pointing out this Reddit thread about cybersecurity conferences (aka cons) that are good for newcomers and junior staff. As a frequent con-goer, the smaller cons (in my view) can be more fun than the bigger annual shows, as there are few people and generally less nonsense or noise to fight through. Meeting people and learning new things is one of the best ways to break through in any field, and cyber is no different.
And finally, this week. @katmabu has a thread of pets in costumes, and the results are as delightful as you'd expect. My personal favorite:

Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Mighty, who can be seen here basking in the sun after a long day of hacking. I'm told Mighty recently passed over the rainbow bridge, but must've had a wonderful life to have had such a good human by their side. Thank you so much to Sam G. for the photo, and we're all sending you our collective love.

🐈 Send in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a later newsletter!
~ ~
SUGGESTION BOX
And that's it for this week's dispatch! Thanks so much for joining me and reading this wild week in cybersecurity. As always, if you have anything for the newsletter, please drop me an email.
It got really chilly on the east coast (now that I'm back) so I'm off to bundle up with scarves and layers to find a bagel from the outside world.
Out for now,
@zackwhittaker