this week in security — november 23 2025 edition
THIS WEEK, TL;DR
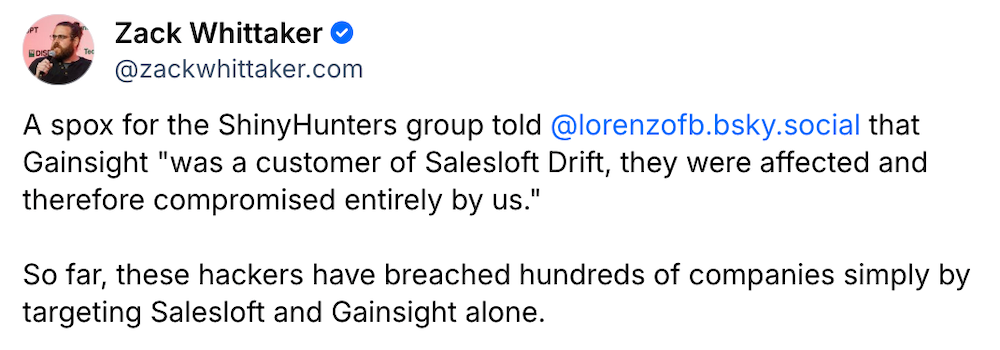
ShinyHunters hackers stole data from 200 companies by hacking Gainsight
DataBreaches.net: A hack at Gainsight, a company that helps customers manage their Salesforce databases, was hacked and some 200 corporate customers had data stolen as a result, according to Google. Salesforce said it cut off Gainsight applications after seeing a raft of suspicious activity, which seemed to catch Gainsight off-guard and scrambling to figure out what was going on. Since this looked like a repeat situation of the Salesloft hack a few months ago, @PogoWasRight asked the ShinyHunters gang if they were involved, and they confirmed that they were and to expect another public extortion effort like last time. The hackers told @lorenzofb that they broke into Gainsight by way of Salesloft's hack months earlier, suggesting the hackers had access for months. Google has some guidance on how to secure your company's Salesforce data, and Salesforce said it has notified affected companies whose data was stolen. Relatedly: CrowdStrike said it fired a "suspicious insider" after they fed screenshots of its internal network to the hackers, which were posted online. (Disclosure: I co-wrote this one!). Unit 42 also warned this week that the ShinyHunters hackers are working on their own ransomware encryptor, suggesting the gang isn't focused on just extortion but also destruction, too.
More: Salesforce | Bleeping Computer | TechCrunch ($) | GitHub | BankInfoSecurity | Dark Reading | Unit 42
Europe wants to scale back GDPR to help Big Tech and AI companies
The Verge: As expected, the European Union announced it was looking to scale back its landmark GDPR data protection legislation as the bloc faces intense pressure from the U.S. government and AI companies to compete. The EU wants to allow AI companies to use personal data to train their models so long as identifiable information is first removed, as well as other changes, such as ridding the need for some cookie consent popups, which, granted, are annoying. The hope is that by cutting red tape, AI companies can help revive the bloc's sluggish economy — assuming the entire AI industry isn't going to collapse in on itself. Reuters ($) has a good explainer on the anticipated GDPR changes. Next stop: a metric ton of scrutiny from lawmakers in the European Parliament.
More: European Commission | The Guardian ($) | IAPP | Deutsche Welle
WhatsApp bug let researchers scrape public data from billions of accounts
Wired ($): University researchers found they could enumerate every phone number in the world — some 3.5 billion numbers — against WhatsApp's servers to check if that number is associated with an existing user, as well as scraping their public profile photo, name, and any other available public information. The researchers said they weren't rate-limited by WhatsApp's servers, so they could check in the region of 100 million phone numbers every hour. If this sounds somewhat familiar, it's because WhatsApp parent company Facebook (aka Meta) had a similar phone number enumeration problem back in 2019.
More: SecurityWeek | GitHub | University of Vienna
Airlines to shutter program that sold flight records to U.S. government
404 Media ($): In some early good news from the week, a data broker called the Airlines Reporting Corporation (ARC) that was set up by airlines to sell customers' data to the U.S. government without a warrant has said it will stop the practice after facing pressure from lawmakers in recent months. This is largely thanks to 404 Media's dogged reporting on the program, showing that it sold hundreds of millions of customer flight records every year to aid government surveillance. ARC has sold to ATF, ICE, the FBI, and the State Dept. and others. This is more impact journalism from 404 to add to the growing pile.
More: Migrant Insider | The Record | @josephcox | @RepEspaillat
Border Patrol's hidden cameras used in sprawling in-land surveillance program
Associated Press: Incredible reporting here uncovering and documenting a massive U.S.-wide covert license plate tracking surveillance program set up by U.S. Border Patrol to monitor for entirely subjective "suspicious" travel patterns. The program operates largely in secret, so much so that Border Patrol embedded cameras disguised as roadside traffic drums and electrical equipment. Using public records requests, the AP identified the locations of these cameras in the wild and photographed them. This is really worth the read.
More: Associated Press | @byrontau | @garanceburke

~ ~
THE STUFF YOU MIGHT'VE MISSED
Critics say banning ransom payments ban won't stop major hacks
Financial Times ($): The U.K. government is planning to ban many companies operating in Britain from paying hackers following a cyberattack, a move aimed at preventing hackers from profiting from cybercrime. Critics argue the ban won't stop hacks but will make it much harder to negotiate with hackers. That said, the pro-ban crowd have long said cutting off hackers from their profits will help in the long-run, but that this also requires some actual investments in defensive cybersecurity practices.
Trump's FCC votes to scrap cyber requirements for telecom firms
Cybersecurity Dive: Two Trump-appointed FCC commissioners, including its chairman Brendan Carr, have voted to scrap minimum cybersecurity requirements for large phone and internet companies. This comes just months after some of the U.S.' largest telecom companies, including AT&T, Verizon, and others, reported intrusions attributed to the China-backed Salt Typhoon hacking crew with the aim of stealing valuable call and text message records on senior American officials. The FCC's sole Democratic commissioner dissented in the vote. More via @ericjgeller.
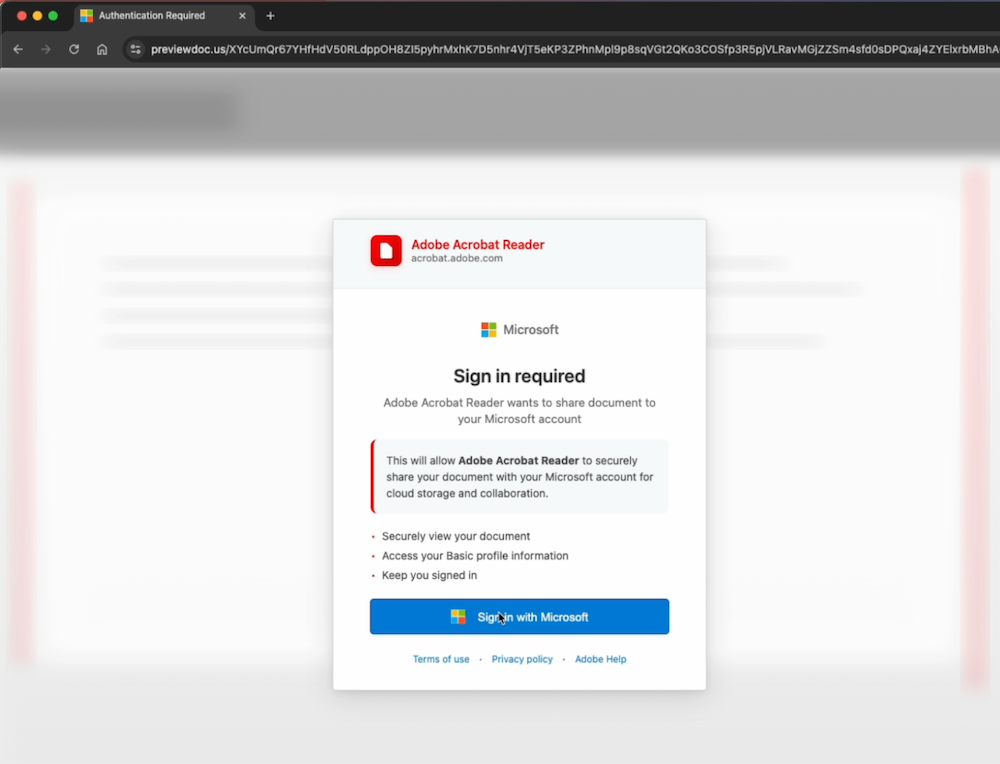
New sneaky phishing attack uses browser-in-the-browser trick
Push Security: An increasingly popular attack that makes it look like a legitimate browser popup is asking for your credentials has been spotted in criminal phishing attacks with the aim of stealing credentials and two-factor codes. Instead of loading an actual popup, the malware campaign simulates a login form within the browser window that aims to trick unsuspecting victims into handing over their credentials. Bleeping Computer covers some of the history of browser-in-the-browser attacks.
U.S. hacker conference HOPE loses venue after complaint
2600: Popular U.S.-based hacking conference Hackers on Planet Earth (aka HOPE) was banned by its event host, St. John's University in New York City, because — as the conference hosts were told — "a single person thought we were promoting an anti-police agenda." HOPE has been operating since the mid-1990s, and one of my own personal favorite cons in recent years to attend. "We don't know exactly how we'll get through this latest challenge. But we know we will," said HOPE, clearly in both name and spirit.
PowerSchool breach blame shared by school districts
The Register: A new report by Canadian data protection officials this week found that schools who relied on ed-tech giant PowerSchool to store their students' private information were also in part to blame for their part in the company's massive data breach. While PowerSchool took most of the blame for using poor passwords and a lack of multi-factor authentication that could've prevented the massive theft of 60+ million records, "widespread failings across the education sector" meant that schools weren't checking to ensure that PowerSchool had the basic security mechanisms in place when signing their contracts.
What organizations can learn from Capita's record-breaking ransomware fine
Double Pulsar ($): U.K. authorities slapped gov-tech giant Capita with a record breaking fine following its 2023 ransomware attack that saw 6.6 million people have data stolen. Area cyber-porg @GossiTheDog takes this excellent post-mortem read to a next level by diving into the Capita hack, why the company's response was largely a complete shitshow, and what other companies can learn from Capita's mistakes. (Also see BushidoToken for an October blog with additional lessons learned, too.)
Harvard hacked (again) to steal donor records and personal data
The Harvard Crimson: Props to The Harvard Crimson, the student-run newspaper at Harvard, for breaking news that their university was hacked — for the second time this year — to steal data from its internal systems. The journalists report that a "phone-based phishing attack" was used to compromise data from Harvard's alumni office, including donor data. Columbia and UPenn were also hacked earlier this year. Bloomberg ($) also has some yarn on the latest Harvard hack.
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
OTHER NEWSY NUGGETS
Buh-bye bulletproof host: U.S., U.K., and Australian authorities have sanctioned Media Land, a so-called "bulletproof" web host that aims to shield its customers from takedowns and law enforcement actions. The trio of governments say the web host was used by LockBit, BlackSuit, and Play ransomware gangs to launch some of their attacks. (via TechCrunch ($), Cyberscoop)
Chrome's seventh zero-day: Google has patched its seventh zero-day in its Chrome browser this year. Google said the bug, tracked as CVE-2025-13223, has been exploited "in the wild," meaning it's being used in active hacking campaigns. Update (or restart your browser) today to patch. (via HelpNetSecurity)
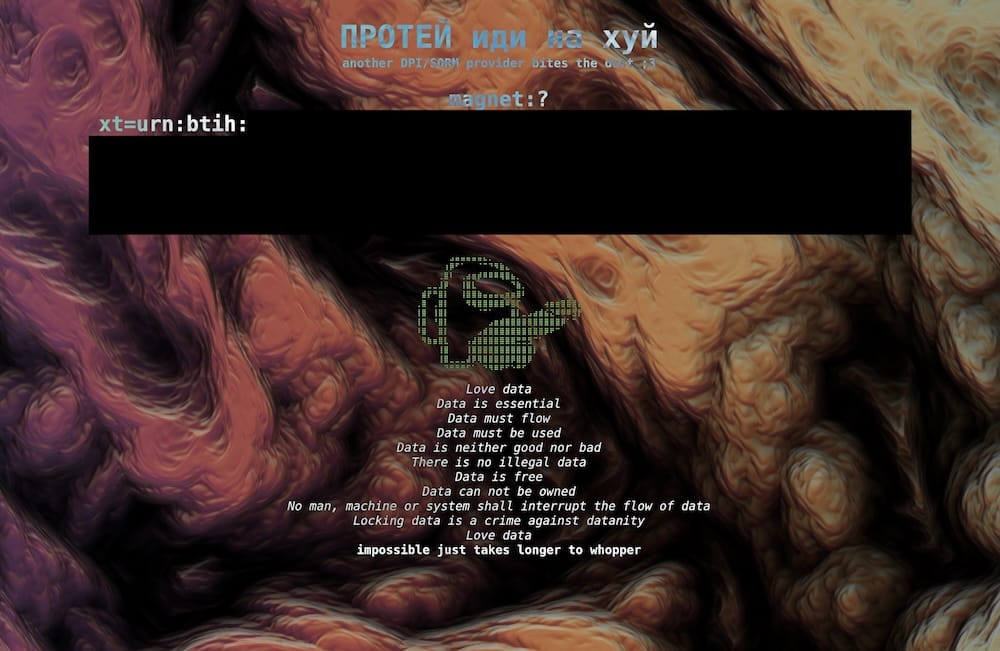
Surveillance vendor hacked and defaced: Protei, a provider of web-filtering products and deep packet inspection (DPI) systems to internet providers, was hacked, its servers raided, and its website defaced. (Disclosure: I wrote this story!) The hacker's defacement said, "another DPI/SORM provider bites the dust," referring to SORM, Russia's system for lawful intercepts. (via TechCrunch ($), DDoSecrets)
Trusted SMS shortcode used to phish: Hackers sent hundreds of thousands of scam text messages to users from trusted SMS shortcode numbers in an effort to trick recipients into calling a scam phone number. Texts from unknown numbers are common, but five-digit trusted shortcodes — such as those used by banks, non-profits and organizing groups — are rare, due to their tight regulation. (via NBC News, @kevincollier)
Banking data stolen in SitusAMC breach: The FBI is investigating after a swath of banking data was stolen from SitusAMC, a real-estate and banking advisory firm, used at hundreds of banks, including JPMorgan Chase, Morgan Stanley, and Citi. The company confirmed it was hacked on November 12 and said that some customer data was stolen. (via The New York Times ($), Reuters ($))
SEC drops SolarWinds' CISO case: SolarWinds' CISO is off the hook after the U.S. securities regulator, the SEC, dropped a civil fraud case it brought following the company's hack in 2019. The SEC argued that SolarWinds failed to disclose certain risk factors prior to the hack, which allowed Russian government hackers to break into dozens of federal agencies using SolarWinds' hacked software. Legal watchers saw the case as a potential precedent-setter for the wider cybersecurity industry. (via Cyberscoop, Cybersecurity Dive)
DoorDash breached (again): Delivery giant DoorDash has confirmed that personal information belonging to customers, delivery drivers, and merchants was taken in a recent data breach. DoorDash said an employee fell for a social engineering attack (counterpoint: DoorDash didn't do enough to properly protect itself from a social engineering attack.) DoorDash said names, email and physical addresses, and phone numbers were stolen. (via SecurityWeek, TechCrunch ($))
CISA orders Fortinet bug patch: Civilian federal agencies have only a few more days to patch affected Fortinet WAF* products (*corrected!) from a zero-day vulnerability used in active hacking campaigns. CISA ordered agencies to fix their systems, saying the bug presents "significant risks to the federal enterprise." (via Bleeping Computer, Fortinet)
~ ~
THE HAPPY CORNER
We start the Happy Corner™ this week with some excellent news out of Oakland: the California city has rejected a $2 million contract with surveillance maker Flock — which provides the city's existing license plate scanners — over fears that federal immigration authorities like ICE can tap into the data. Hundreds of local residents rallied against Flock at the council meeting. It's not exactly clear what happens to the city's existing array of cameras, but it goes to show that people power at the local level really does work.
Speaking of people power… turns out that electronic voting is really difficult, even for the experts. A cryptology group recently held an election for various leadership posts by using a highly secured voting tally system. But one of the three people with private keys needed to unlock the results lost their key, sending the tally results into a cryptological black hole and unable to be recovered. More from The New York Times ($) and Ars Technica.
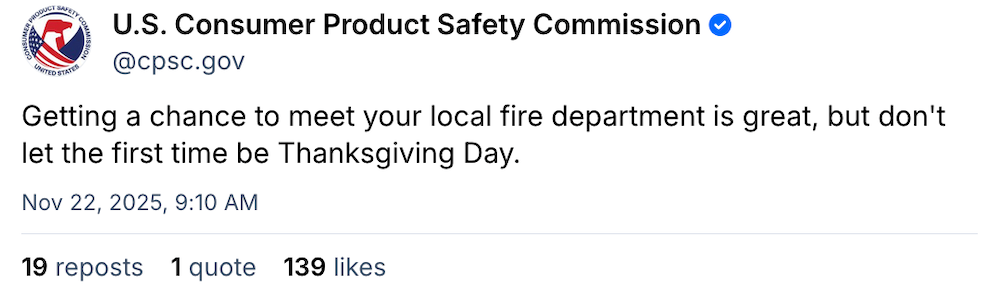
And in the spirit of the upcoming Thanksgiving holiday this week, here's a little dose of levity from what might be the only U.S. government department still capable of being helpful while also having a little fun.
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Millie, who can be seen here trying her very best to hack into the garden from inside the house, but clearly not having much luck. Millie's human tells me that one day she'll get a job as a pentester, but she's got a long road of training first. Many thanks to Michael W. for sending in!

🐈 Send in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a later newsletter!
~ ~
SUGGESTION BOX
And not wanting to keep you for a moment longer... that's it for this week! Catch me again next Sunday with your usual round-up and drive-by analysis from the weird and wonderful (but often woeful) world of cybersecurity.
If you have anything you want to share for the newsletter (or feedback, newsletter suggestions, a cyber-cat or friend, or just to say hello), please drop me an email. Since this week is the Thanksgiving holiday, it may be a lighter edition next week — or not, let's face it, cyber doesn't sleep for anyone or anything. But we'll see what happens!
Stay safe on the cyber webs,
@zackwhittaker