this week in security — november 30 2025 edition
THIS WEEK, TL;DR
Gainsight downplays data breach as Salesforce urges customers to check logs
Cyberscoop: The Gainsight breach continues to unfold. Last week, Salesforce cut off Gainsight's customers after seeing "suspicious" activity. Google later said 200 Gainsight customers are affected by the breach, which DataBreaches.net linked to the ShinyHunters hacking group and its associates. Now, Gainsight's CEO confirmed that while some of its customers were breached and had data stolen, not all of them did, but neither Gainsight nor Salesforce have provided an accurate number of how many customers are known to be affected. Mandiant (aka the security adults in the room) is still investigating the scale of the incident. What's clear is that somewhere between some and many customers had data stolen during the hack. If you're a Gainsight customer, it may be best to assume the worst until you can prove otherwise. Salesforce has published known IOCs so that network admins can check for malicious activity.
More: Gainsight | Salesforce | HelpNetSecurity | Cybersecurity Dive
Meet 'Rey,' the Jordanian teenager and admin of Scattered Lapsus$ Hunters
KrebsOnSecurity: Brian Krebs flexed his investigative skills once again by tracking down a key administrator of Scattered Lapsus$ Hunters, a collective of various hacking groups (including ShinyHunters and Scattered Spider), who all have a knack for stealing gobs of corporate data through social engineering attacks. The gang of gangs is behind dozens of hacks and extortion attempts, including mass thefts from Salesforce databases and more. Krebs notes that after identifying the Jordanian teenage hacker, he attempted to contact his father to alert him that his son was involved in cybercrime. Instead, Rey agreed to speak to Krebs directly, confirmed that Krebs got his real-world identity correct, and said that he was trying to extricate himself from cybercrime by cooperating with the police. Relatedly: ReliaQuest said they have evidence that the hacking group is now targeting Zendesk instances in an effort to steal their stores of customer data.
More: The Register | KELA Cyber | ReliaQuest
PostHog says Shai-Hulud 2.0 worm is the firm's 'largest' security incident
The Register: Here we go again… For the second time this year, a self-propagating malware dubbed Shai-Hulud targeted developers en-masse, hitting some 25,000 devs in just a few days. For those who don't code, this is a messy one to understand but The Register does a decent job of explaining what was essentially a major five-alarm fire for the software development world. In short, Shai-Hulud was found ripping through npm open source projects, stealing and using credentials for other cloud services, like AWS, Google, and GitHub, among others, to spread even further. One affected project was PostHog, which said the worm modifying its packages used by its developer community was its "largest" security incident to date, given that so many people and downstream projects rely on PostHog's code.
More: Socket | Trend Micro | @jackhcable | @taggart-tech | @christopherkunz
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
THE STUFF YOU MIGHT'VE MISSED
U.K. lawmakers call for software devs to face cybersecurity liability
The Record: An interesting if not controversial proposal (though not new — thanks @brianhonan!) by U.K. lawmakers could mean software developers could face liability for the cybersecurity of their code. The lawmakers' report recommends making "Secure by Design" principles, which bake in cybersecurity at the start of the product development cycle, mandatory in the U.K., potentially opening the door for the government to hold shoddy software makers accountable if they don't adhere to the cybersecurity basics. Very early days here, and I think everyone might have an opinion on this…!
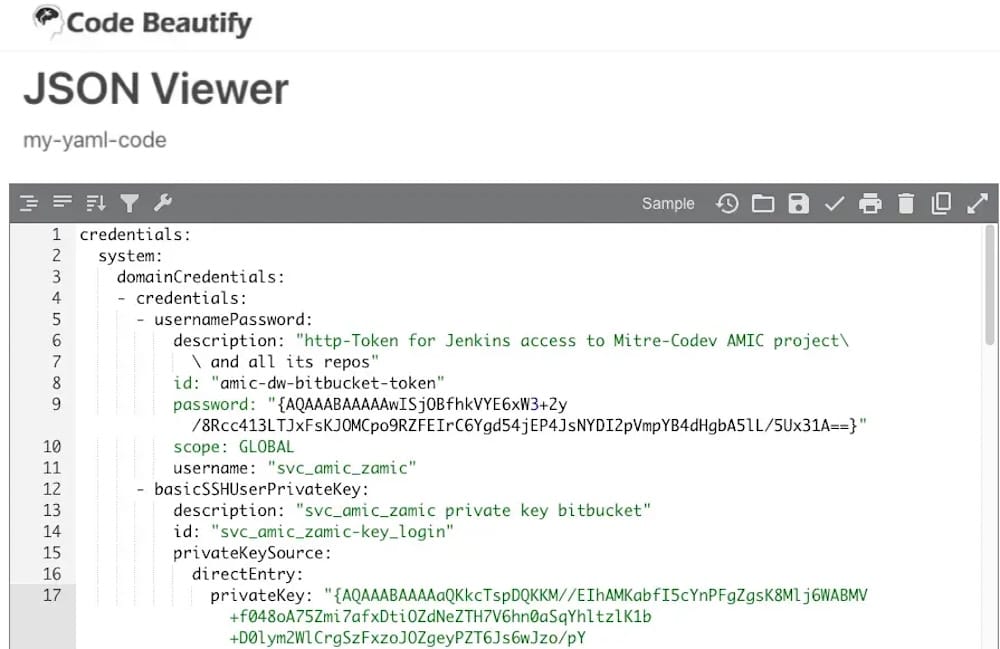
Pasting passwords and secrets into random websites are spilling online
watchTowr Labs: Apparently this needs saying… so… *pinches bridge of nose*... Please stop pasting your passwords, API keys, and other secrets to random websites! According to watchTowr Labs, plenty of folks use websites like JSONFormatter and CodeBeautify, which help to make large chunks of code more readable to humans. These websites let users save their pastes to share their results, not realizing they're public and also very, very easy to find.
Emergency alerts disrupted as OnSolve CodeRED hit by ransomware
Bleeping Computer: Crisis24 has confirmed its OnSolve CodeRED emergency notification system was hit by a cyberattack (allegedly ransomware), causing disruption to alerts across the United States. One university customer in Texas said data was stolen in the hack. Crisis24 is rebuilding its platform from a backup it had from late-March.
FCC says hackers are hijacking emergency systems to send fake alerts and broadcast obscenities
Reuters ($): Hackers are hijacking radio transmission equipment made by Swiss audio company Barix to broadcast fake emergency messages and obscene language. Radio World had this back in September, but now the FCC — more than two months later — urged broadcasters to secure their Barix systems [PDF]. Per Shodan, there are still hundreds of these devices exposed to the internet.
Bug in U.S. court systems exposed jurors' personal information
TechCrunch ($): Govtech provider Tyler Technologies is fixing a bug that allows anyone to brute-force access to the juror selection websites that the company develops for local governments across the U.S. and Canada. The bug allows anyone to rapidly cycle through the easy-to-guess information jurors have to provide the website when required to respond for jury service, thanks to a lack of server-side checks preventing mass login attempts (known as rate-limiting).
Holiday cyber scams are getting more inventive
NPR: NPR's @jennamclaughlin chats with Bob Rudis at Greynoise about some of the pressing cyber threats facing consumers today. This includes hacks that hijack home routers and use their bandwidth to launch DDoS attacks, and more. GreyNoise launched its own IP address checker for anyone who wants to see if their router has been ensnared by a botnet. Somewhat relatedly: I wrote a blog post this week looking at why the U.S. government may issue a nationwide sales ban on router maker TP-Link over its alleged links to China, and why any ban probably won't make the U.S. any more secure.
~ ~
OTHER NEWSY NUGGETS
London councils say data stolen after hack: At least three London boroughs have confirmed disruption following a cyberattack. Some of the councils share affected infrastructure, they said. One of the councils, Kensington and Chelsea, now says some data was copied and taken during the hack. (via BBC News ($), Sky News)
OpenAI drops Mixpanel after breach: Analytics giant Mixpanel, whose analytics code is used pretty much everywhere for tracking how people use various apps and websites, was breached, prompting at least one of its major customers, OpenAI, to drop Mixpanel altogether. The breached data was limited to profile information of API users, but given how ubiquitous Mixpanel is, this warrants a close and careful watch. Mixpanel's breach notification was also next-level crap, frankly, and says little about the incident itself, except that it was related to SMS phishing — but doesn't say how! (via SecurityWeek, OpenAI)
Budget leak blunder: The U.K.'s annual budget proposals leaked online ahead of the big reveal, because… journalists guessed the publication's URL. It turns out the file was published online with an easily guessable by file name at an easy-to-find web address. The U.K. government has called in former cyber boss @ciaranm to investigate. Not sure how much there is to investigate, as The Register noted citing one Reddit user:
North Korea blamed for UpBit crypto theft: South Korea believes the Lazarus Group, the North Korean hackers who specializes in the thefts of cryptocurrency, are behind a recent $30.4M heist targeting crypto exchange Upbit. North Korea has been behind at least $2 billion in stolen crypto this year alone. Why? Because those nukes don't pay for themselves. (via Reuters ($), Yonhap)
South Korea mopping up retail hack: South Korean retail giant Coupang was hacked to the tune of 33 million people's data, with data taken as far back as June. For context, South Korea's population is around 50 million. (via Bloomberg ($))
British broadband Brsk breached: U.K. broadband provider Brsk had a data breach, affecting the personal data of more than 200,000 customers, including names, email and residential address, phone numbers, location data, and records identifying whether a customer is considered vulnerable, such as those with medical needs.(via ISP Review, ThinkBroadband)
SitusAMC breach includes U.S. banking customers' sensitive data: Financial tech firm SitusAMC, which helps banks process loan applications, said hackers stole a range of data during its breach. The company said hackers stole its corporate files, which included accounting data, such as invoices and legal records, and client files, consisting of data related to our client’s business activities, which focus "largely on assignments and recording of mortgages." (via SitusAMC, Axios ($), SecurityWeek)
~ ~
THE HAPPY CORNER
A happy weekend to you all, and welcome back to the happy corner, where everything is chill and the vibes are peaceful.
Give the gift of good cybersecurity advice this holiday season by arming yourself with some hacklore knowledge, thanks to area cyber gent @boblord (who wrote a blog) and the dozens of awesome cybersecurity professionals who signed on to this fantastic cyber BS-busting cyber project. Hacklore.org debunks some of the common cyber myths out there — like claims that using public Wi-Fi and charging ports are dangerous — so that we can focus on giving out good and legitimately helpful cybersecurity advice. Check it out!
Here's a little nostalgia for everyone, looking at the user interface and design of Windows through the ages, dating all the way back to Windows 1.0 in 1985, blasting past the Windows "what were they thinking?" Vista years, all the way through to today's Windows 11 AI fustercluck. This blog post covers the good, bad and the very, very ugly (I'm looking at you, Windows 10!) I mean, if you don't see some of these screenshots and instantly remember the smell of static from a cathode ray tube monitor, you're… well, probably under the age of 30.
And finally, this week, something for the youths out there. Wired has published its ultimate guide to digital opsec for teens — and no paywall (thanks @lhn!). Opsec is the name of the collective skills you need to keep your information private for the long-term. This guide is excellent (so bookmark it!) as it helps you understand the risks of posting and publishing your information online today and how it can be used in the future against you. This guide uses real-world examples to show when opsec goes wrong, but how good opsec can really help you stay safe and private online. *cue the obligatory GIF*

Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet this week's incredibly cute cyber cat kitten, Robot T-Rex, who according to his human absolutely loves to create perfect circles for some reason. Thanks so much to Simon L. for sending in!

🐈 Send in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a later newsletter!
~ ~
SUGGESTION BOX
"It'll be a quieter week," I said last week. Well... yeah... even for a short week here in the U.S. with the Thanksgiving holiday, we still managed to get through a metric ton of cyber news, both here and around the world! Thanks so much for tuning in and reading. As always, please get in touch with me if you have anything you want to share for next week's newsletter.
If you want to go that little bit further, consider joining ~this week in security~ as a paying subscriber for access to my blogs, analysis, and deep-dives.
Until next Sunday, take it easy and enjoy your week!
Logging off for now,
@zackwhittaker