this week in security — october 12 2025 edition
THIS WEEK, TL;DR
Clop stole data from 'dozens' of organizations who use Oracle E-Business apps
Bleeping Computer, Google: An extortion campaign that emerged last week and linked to the prolific Clop extortion gang now affects "dozens of organizations," according to Google. The hackers raided Oracle E-Business instances, which companies use to host their employee HR files and other sensitive business data, by exploiting security bugs that Oracle said were patched in July. Then, this week, Oracle quietly about-faced in a statement acknowledging that the bugs actually included a zero-day (patched October 4) that was being actively exploited. It seems that Oracle only found out about the zero-day because for some reason the ShinyHunters hackers (more on that in a second) leaked Clop's exploit as part of their own hacking escapades. Aside from that absurdity, this ultimately means Clop's hacking spree wasn't over when Oracle claimed last week that it was. The result is that the Clop hackers have stolen a "significant amount of data" from affected organizations. Oracle really messed up here, especially by gaslighting its own customers. And this is the tech giant now charged with securing Americans' user data as part of a deal keeping TikTok available in the United States. Expect a lot more to come from Clop and this campaign, since this isn't its first mass-hacking rodeo.
More: Oracle | Google Threat Intelligence | The Register | Charles Carmakal (LinkedIn) | watchTowr Labs | Reuters ($) | TechCrunch ($) | @christopherkunz
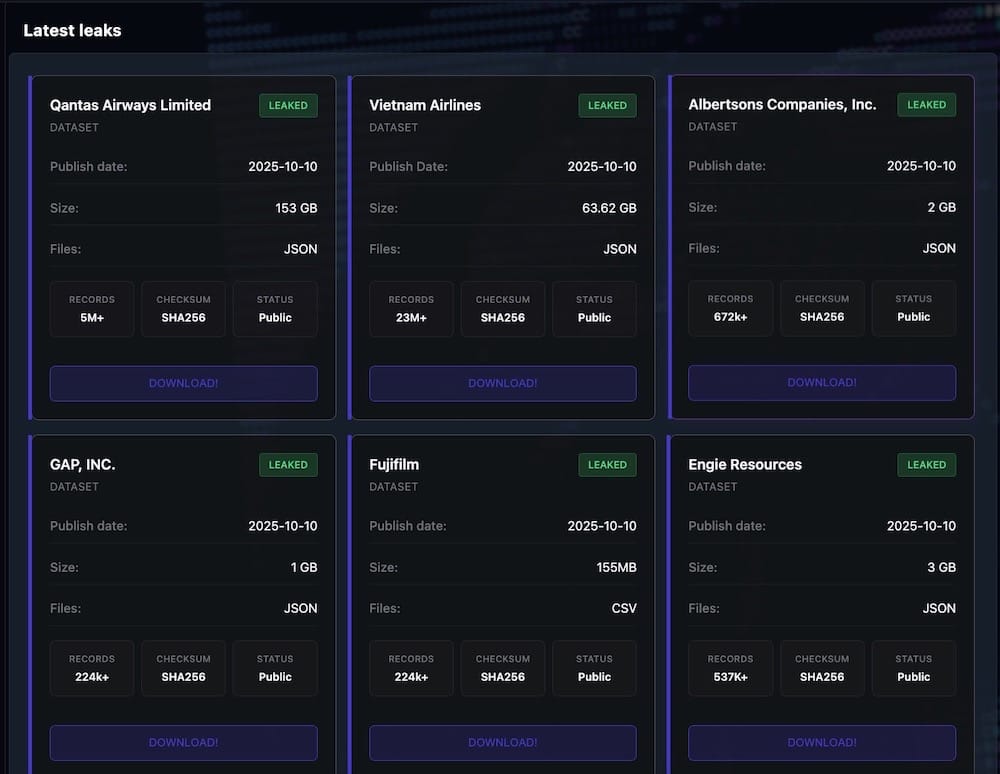
ShinyHunters start leaking data as hackers ramp up Salesforce extortion
KrebsOnSecurity: Moving onto part two of this week's Extortion Wars, and not to be outdone, the ShinyHunters coalition (aka "Scattered LAPSUS$ Hunters") have begun publishing leaked data that they stole during their mass-theft campaign targeting Salesforce databases and Salesloft Drift customers. The now-published data includes at least two airlines, notably Qantas, which obtained a court injunction preventing anyone connected to Australia from accessing or publishing the stolen data. That means folks like top Aussie bloke @troyhunt can't legally load the data into Have I Been Pwned, because Qantas is too busy putting its fingers in its ears and hoping for the best. Salesforce said it wouldn't pay the hackers' ransom, which… fair, but that's not to say other companies won't (or haven't so far). The feds seized the hackers' clear-web leak site this week, but its .onion site (viewable on Tor) remains unaffected. This is a very complicated and messy story in all because of its many moving parts, including other hacking groups joining the fray. But Krebs, as always, does an excellent job of running his readers through this one. Just as with Clop, expect this extortion campaign to stay in the headlines for some time.
More: The Guardian ($) | BankInfoSecurity | Bleeping Computer | Rapid7 | @vxdb
DHS reassigns CISA staff to assist deportations, as federal shutdown continues
Bloomberg ($), Nextgov: And onto your trifecta of bad news… (sorry)... Bloomberg ($) reported this week that the U.S. Dept. of Homeland Security has reassigned hundreds of CISA cybersecurity staffers to other agencies, such as ICE and CBP, to assist in the Trump administration's deportation crackdown. Staff who refuse the mandatory work reassignments can be fired, per Nextgov (which confirmed Bloomberg's reporting). The CISA staffers are said to have been working on international partnerships with other agencies and issuing guidance to protect against cyber threats. Not unimportant stuff! DHS spokesperson Tricia McLaughlin said it was "ludicrous" to suggest CISA was unable to handle threats because of the reassignments… but then just two days later, Trump's budget director Russell Vought fired over a hundred CISA staffers as part of the ongoing U.S. government shutdown. Anyway, if we get hacked again, again, or again this year, we definitely know who to blame.
More: Nextgov | @GossiTheDog | NBC News | @metacurity.com
~ ~
~this week in security~ is my free weekly cybersecurity newsletter supported by readers like you. Please consider signing-up for a premium subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
THE STUFF YOU MIGHT'VE MISSED
Microsoft says Medusa still exploiting Fortra GoAnywhere bug
Microsoft: The Medusa ransomware gang has been caught abusing a then-zero day bug in Fortra's GoAnywhere, a popular file transfer tool used by enterprises to share large files across the internet. The tool has been targeted before by hackers (by Clop, no less), given the sensitive data that these systems store. Fortra has details from September, but didn't explicitly say at the time that the bug was being actively exploited in the wild.
Payroll pirates are diverting university payments (y'arrr)
Microsoft (again): Double-dose Microsoft (credit where it's due), as the company disclosed another attack in the wild involving "payroll pirates." This is a technique where financially motivated hackers use phishing to trick victims into granting access to their cloud or Workday accounts so that they can modify banking details and divert payments into accounts used by the hackers (somewhat similar to business email compromise scams). Ars Technica has more.
Scoring free in-flight Wi-Fi: Air Canada edition
Ramsay Leung: Who needs to pay over $30 for in-flight Wi-Fi on Air Canada when you can just spend a third of the flight trying to get free access to the outside world? That's exactly what Ramsay Leung did and blogged their findings to show how it can be done.
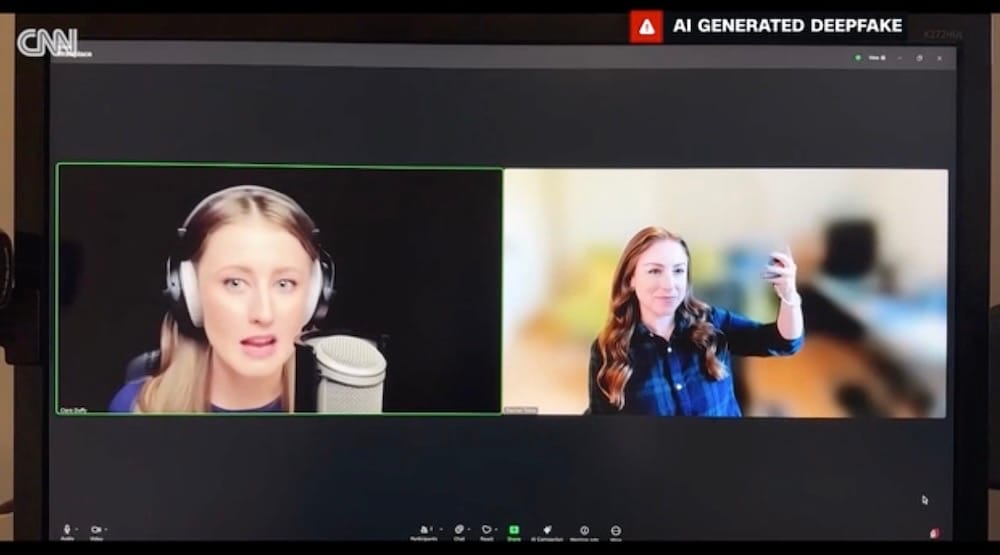
How deepfakes are conning companies out of millions of dollars
CNN: It's no secret that some hackers (including North Koreans!) are increasingly relying on deepfakes and AI-generated videos to trick their victims into thinking they're real people — and it's happening more and more. Here is the very excellent @racheltobac scaring the living daylights out of CNN by revealing just how easy it can be. Remember, if something seems weird, it probably is. Trust your gut!
Discord says 70,000 age check IDs stolen in data breach
404 Media ($): Discord said about 70,000 users had their government IDs (and other personal information) stolen from one of its third-party databases (Zendesk), which Discord uses for age verification checks. This is a clear-cut reason why age verification checks that rely on uploading copies of your passport and a selfie are a really, really bad idea.
SonicWall firewall backup breach affects… everyone
The Register: Remember when SonicWall said only 5% of its customer firewall backups were stolen as part of a breach of its cloud storage? Turns out it was every customer, actually, and SonicWall ate a boatload of humble pie as a result. These firewall files contain firewall configurations, policies, and settings, which can be quite helpful for hackers.
Security leaders share lessons learned from Salesloft Drift hacks
Cyberscoop: The Salesloft Drift attacks earlier this year affected some 700 companies, including Okta and Zscaler, which experienced very different outcomes. This Cyberscoop story was great because it dives into how the companies fared following the hack and why. Lots of lessons to learn here, and props to the companies for their transparency.
~ ~
OTHER NEWSY NUGGETS
ICE bought phone-snooping tech in vans: ICE now has access to vans equipped with cellphone-locating equipment, the latest in a raft of technologies in use by the U.S. deportation force. My TechCrunch colleague @lorenzofb found contracts revealing that ICE spent more than $1.6M over the past two years on these vans that house cell-site simulators (aka IMSI catchers or stingrays). Meanwhile: SAN reports that these fake cell phone towers may've snooped on anti-ICE protesters in Portland. (via TechCrunch ($))
North Koreans spoofing architects now?! A new report shows North Korean spies aren't just posing as regular IT workers to get jobs at big companies to earn billions for the North Korean regime while skirting international sanctions. Turns out these same spies are also trying to trick U.S. companies into hiring them to develop architectural designs. All of this to say, this North Korean hiring scheme is far, far wider than most people think. (via Wired ($), KELA)
Hey ChatGPT, build me a nuke: In a series of tests, NBC News found that several of OpenAI's ChatGPT models can be tricked into spitting out designs for nuclear weapons and instructions for making napalm, among others (and not for the first time!). (via NBC News, @kevincollier)
Not even cyber first choice: William Hartman, the acting NSA and Cybercom director who took over after Trump fired its then-director Timothy Haugh and other top brass at the request of a far-right activist, won't be nominated for the full NSA directorship after all. The U.S.' top spy agency has been essentially rudderless for months. (via The Record)
India might've spilled millions of tax records: India's income tax department exposed the highly sensitive personal and financial information of potentially everyone who used the online government portal to file their taxes, some 135 million registered users. At fault was a very simple-to-exploit bug. The Indian government fixed the bug after @journalistjagmeet verified the bug and alerted the agency. (via TechCrunch ($))
Security cams pulled from shelves: The FCC said Friday that several U.S. online retail websites will remove from sale security cameras made by Dahua and Hikvision (and others), whose technology is known to be used by the Chinese government to oppress its citizens and were subsequently banned for sale in the U.S. in 2022. (via Reuters ($))
Spyware maker NSO gets an American parent: NSO Group, the maker of the notorious Pegasus spyware, is now in U.S. ownership, an NSO company spokesperson confirmed, after a deal involving a group led by Hollywood producer Robert Simonds and "tens of millions of dollars" purchased the company. NSO will remain in Israel and be supervised by the Israeli government, the spokesperson said. (via TechCrunch ($), Calcalist)
~ ~
THE HAPPY CORNER
It's nothing but good news from here on out. Welcome to the happy corner.
In absolutely excellent news, Chat Control, the controversial European plan to scan the contents of everyone's end-to-end encrypted messages, has failed (at least for now). Germany eventually balked at the idea (after reportedly considering going along with it) after mounting pressure. Signal said it would leave Europe rather than face being forced to scan user messages, but said it was "relieved" to see Germany reaffirm its opposition to backdoored communications. Thanks also to one Dane who set up a website criticising Chat Control, European lawmakers were inundated with messages about their own ineptitude.
Speaking of encryption… thanks muchly to @riana for the reminder that there's an updating Google Doc of articles and papers about encryption and trust and safety to read.
Apple announced it has bumped its bug bounty payments up to $2 million for anyone who can hack iPhones capable of achieving "similar goals" to mercenary spyware, essentially a full compromise of a device (Wired ($) has a good story on this as well.) On top of that, buried in Apple's post was a note that it will provide "a thousand iPhone 17 devices to civil society organizations who can get them into the hands of at-risk users." (It's a drop in the ocean for a company worth $4 billion, but it's a start). But this is a really good thing since iPhone 17 devices come with memory safety features, making them far less susceptible to the class of bugs frequently abused by spyware. As such, these phones might be pretty darn helpful for those who face these attacks. (via @martijngrooten)
And finally, this week, since we're entering 👻 spooky 🎃 season:
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Ms. Charmaine, who can be seen here with the face of horror, utter horror(!) and judgement after learning that you haven't two-factored all of your online accounts. (Go and two-factor all of the things!) Thanks so much to Jillian J. for sending in!

🐈 Keep sending in your cyber cats (or friends!) 🐈⬛ This newsletter is powered by your cyber-cat submissions! Send in an email with a photo and name of your cyber-cat (or non-feline friend) and they will be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it for this week's edition of the newsletter! Join me next Sunday (or whenever you read!) for the next installment of whatever happens in the world of cyber. Thanks so much for reading. I hope you have a great rest of your week.
As always, please do get in touch with any comments, questions, feedback or submissions for the newsletter!
See you next,
@zackwhittaker