this week in security — october 19 2025 edition
THIS WEEK, TL;DR
Satellites are leaking the world's secrets, including private calls and military comms
Wired ($): We start this edition by looking up, literally. You might think that all of those satellites beaming our information to and from Earth are encrypted? Well, you'd be very, very wrong. University researchers spent three years pointing an off-the-shelf satellite dish at the sky to see what secrets satellites would spill, and it was surprisingly a lot — from the contents of T-Mobile consumer cell phone calls to military communications and internal corporate data. Satellites are used in a variety of circumstances but many aren't protecting the data from eavesdroppers, including the world's governments. Wired ($) had the scoop. The researchers spent the past year alerting various companies and organizations; some satellite links have been secured, but many (including critical infrastructure) remain open to snoops — and could be this way for some time. This was one hell of a way to start the week, and things only seemed to get worse from there.
More: SATCOM Security | @agreenberg | @matthew_d_green
Chinese hackers were inside F5 Networks since 2023
Bloomberg ($): Cyber giant F5 Networks disclosed Wednesday that it was hacked, and that the hackers had "long-term, persistent access" to its network. The hackers were caught in August, but the DOJ allowed F5 to delay public notification on national security grounds, given that the company provides cybersecurity defenses to most of the Fortune 500. Bloomberg reports that the hackers are Chinese state-backed and had access since 2023, which… oof, but especially oof for an ostensible cybersecurity company. F5 said the hackers also had access to its internal BIG-IP development environment as well as several undisclosed security flaws, prompting the firm to release a slew of product fixes to the public. Once again, we're faced with a U.S. cybersecurity giant at the root of yet another major security breach. U.S. cyber agency CISA ordered U.S. federal networks to take "immediate" action to patch their networks by… next week. Much urgency!
More: F5 Networks | Bloomberg ($) | Wired ($) | CISA | Bleeping Computer | TechCrunch | Ars Technica
China had access to U.K. classified networks for over a decade
Bloomberg ($): Staying with China… former political officials in the then-Conservative U.K. government revealed that China had access to the U.K.'s classified networks since at least 2013. The hacks involved access to the U.K.'s "official-sensitive" and "secret" levels of classified material, but senior cyber officials in charge at the time pushed back to stress that the government's most sensitive "top-secret" information was not affected. Instead, much of the mid-level classified stuff includes "formulation of government policy, private communications and some diplomatic cables," which… granted, not great. According to Bloomberg, the U.K. government was caught out in one breach after a London datacenter used to store sensitive government information was sold to a Chinese-aligned entity while the Conservatives were still in power. Ministers reportedly proposed a plan "to destroy the data center before it was made secure in a different way." Uhhh…. I'm sorry but what now?!
More: The Times ($) | Ciaran Martin (LinkedIn) | @kimzetter | @triclassified
Surveillance firm tracked world leaders and executives via SS7
Mother Jones, Lighthouse Reports: Incredible reporting here from Gabriel Geiger, who last year found a massive dataset of surveillance operations targeting thousands of people around the world, a finding so alarming that he felt "like shitting my pants." The cache belonged to First Wap, a surveillance company that exploits access to the global phone networks to snoop on the real-world locations of tech executives, a Vatican enemy, an actor, and many others. This story reveals how the long-running abuse of the SS7 protocol (which phone carriers around the world rely on to route calls and texts seamlessly across their networks) is used to gain access to pretty much anyone else's private information without their knowledge and without the need for spyware. To call SS7 the "asbestos of cellular networks" is an understatement, as we've seen SS7 exploits date back to at least the past decade.
More: Lighthouse Reports (methodology) | Gabriel Geiger (LinkedIn) | Amnesty
Windows 10 reaches end-of-life, will no longer get security updates
The Guardian ($): Here we go again, Windows 10 edition. The Microsoft operating system, with some estimated 40% of the PC market, has reached its end of life and will no longer receive software or security updates by default. Users can still get extended security updates for a year, but with some caveats. Windows 10 users have the option to upgrade to Windows 11, but a lot of people don't want any of the new AI nonsense, and there are estimated hundreds of millions of computers that simply don't have the hardware specifications to run the new software. This has prompted some folks to move to Linux so that they can save their hardware from the scrap heap (though there is an option to install Windows 11 if you don't have the right hardware). The alternative is a huge e-waste disaster waiting to happen, per 404 Media ($), with millions faced with throwing out their devices. Meanwhile: KrebsOnSecurity has your October Patch Tuesday update, including three zero-days, but also top advice and options for Windows 10 users.
More: Microsoft | EndOf10 | Associated Press | @wdormann
~ ~
THE STUFF YOU MIGHT'VE MISSED
Oracle patches new E-Business zero-days, as data breach victims come forward
Bleeping Computer: This Oracle E-Business fustercluck remains ongoing, as the tech giant fixes a fresh zero-day under active attack by hackers (though you wouldn't know it from Oracle's weak-ass disclosure). This time it's CVE-2025-61884, which patches another remotely exploitable bug in Oracle's E-Business software. Bleeping does a great job of explaining this very messy and sprawling hack. Also: Several breaches stemming from the E-Business raids were confirmed, including the American Airlines subsidiary Envoy and Harvard University. Expect many, many more breach notices to come.
Software vendor still exposing sealed court records, despite months of warnings
DataBreaches.net: The esteemed @PogoWasRight has spent months notifying a software vendor in Tupelo, Mississippi of a data lapse involving the exposure of sealed court records, the latest in a long line of govtech firms with shoddy security. And yet, the issue remains active because the company thinks ignoring this will make it go away.
Hackers can steal two-factor codes and private messages from Android apps
Ars Technica: "Pixnapping" is a theoretical new Android bug that can allow malicious apps with no system permissions to read the contents of a user's Android screen, such as two-factor codes and private messages from other apps. The bug was demonstrated on Google Pixel and Samsung Galaxy devices. Google "partially" fixed the bug last month and said it's seen no evidence of exploitation. But it's always good to limit the number of apps on your phone for privacy and security's sake.
Secret FBI group tasked with disrupting Russian ransomware gangs
Le Monde ($): French media reports that the FBI is running a clandestine unit called Group 78, whose job it is to "conduct operations in Russia," including manipulating Russian authorities, with the aim of targeting members of Black Basta, one of the most prolific Russian hacking crews. The goal is to make their lives more difficult so that they want to leave Russia and the Kremlin's protections. European officials were left shocked when the FBI told them, fearing that their own operations targeting the gang would be affected. (The story is in English, but there's a short thread en français).
Developer narrowly avoids getting hacked via fake job interview
David Dodda: Developers, beware. Dodda blogged (with screenshots!) about receiving an invitation to apply for a coding job, but quickly found that the "test project" used to try out his skills during the job interview contained cleverly disguised malware. This blog goes into detail about what you can look for and how to avoid these attempts. North Koreans are known to use these tactics as well.
~ ~
~this week in security~ is my free weekly cybersecurity newsletter supported by readers like you. Please consider signing-up for a premium subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
OTHER NEWSY NUGGETS
Capita accepts £14M fine for its cyber hot mess: U.K. data protection watchdog ICO fined govtech giant Capita £14m ($18.8m) for a slew of cybersecurity failings, including its sluggish incident response, following a 2023 ransomware attack and data breach that affected over 6.6 million people's data. The ICO was spicy in its written monetary penalty notice [PDF]. (via The Register, The Record, @lisaforte)
Did China just catch NSA hacking? In a rare-(ish) accusation involving Western hacking, China says the U.S. National Security Agency conducted cyberattacks against its national time-tracking center, which maintains and broadcasts China's high-precision standard time. It's not clear for what reason the systems were allegedly hacked, but time systems are pretty crucial for the running of critical systems. (via Bloomberg ($), Reuters ($))
ICE has nationwide camera access, for Flock's sake: 404 Media ($) reports that ICE, the Secret Service, and the Navy all had access to a nationwide network of 80,000 license plate-reading cameras provided by for-profit surveillance giant Flock. In the same week: 404 Media ($) confirmed that the ShinyHunters hackers also published the personal information of hundreds of ICE agents, DOJ, and FBI officials. (via DataBreaches.net)
Bolton indictment exposes extortion: Former U.S. national security adviser John Bolton was indicted on Thursday for allegedly mishandling classified information. Bolton is one of several Trump critics subject to criminal investigation of late. The indictment against Bolton, who pleaded not guilty, follows a hack of his AOL email account and an alleged subsequent extortion attempt by the Iranians. (via ABC News, Zero Day)
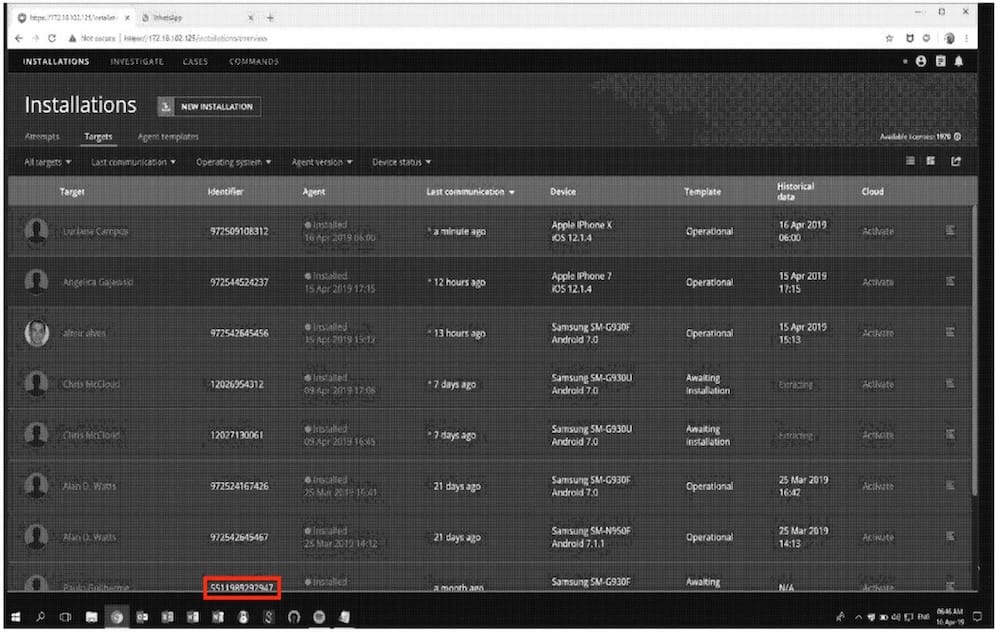
NSO banned from WhatsApp: A U.S. court has ordered Pegasus spyware maker NSO Group to stop targeting people via WhatsApp, a move that NSO says could put it out of business (even though it just got bought by an American-led investment group). From the lawsuit, we got a new (albeit grainy) photo of what Pegasus looks like to its government customers. (via Reuters ($), @jsrailton, @jurrevanbergen)
Prosper, Asahi report data breaches: Loan and financial giant Prosper revealed a data breach that affects over 17 million people, per Have I Been Pwned. You might not've seen the notice though, since Prosper is using noindex code to hide the page from search engines, which makes it more difficult to find. Also: Although Japanese beer maker Asahi is recovering from its ransomware attack that disrupted beer production and delivery, the company said company data may've been stolen. (via Bleeping Computer, The Register)
PowerSchool hacker gets four years: Matthew D. Lane, who was a teenager at the time he hacked edtech giant PowerSchool and stole over 60 million students' data, will spend four years in the slammer as a result. This was one of, if not the largest education-related data breach in U.S. history. (via Cyberscoop, The 74 Million)
Feds seize $15 billion (with a b!) in crypto: U.S. prosecutors have seized $15 billion in crypto from a prolific Cambodian forced labor scheme that operates a huge global "pig butchering" scam. These scams often appear as seemingly random text messages that appear out of nowhere, but hook people in with romance lures as a way to get access to their bank accounts. This works at a staggering rate. Wired ($) explains more in its news story, and backgrounder. (via Justice Department, USA Today)
~ ~
THE HAPPY CORNER
Listen carefully… Can you hear that? …nothing? Exactly. It's peace-and-quiet time in the happy corner, and you're invited!
Two, potentially cursed words: Encrypted mayonnaise.
Admittedly, I laughed at this one (and an obligatory explainer for the kids).
After some 35 years, the solution to the CIA's "Kryptos" sculpture located outside the spy agency's headquarters in Langley has been discovered. Turns out the decoded answer was known only to the sculpture's creator… but was also mistakenly included in folders that were locked in a vault at the Smithsonian. The New York Times ($) has the story.
And congrats to the BBC's cyber bod @joetidy ahead of the launch of his new podcast, which takes a deep dive into the Russian hacking group, Evil Corp, said to be responsible for major breaches and the theft of hundreds of millions of dollars. The seven-part series starts Monday, so check it out. The Beeb's media center has a few teaser words. I can't wait to listen!
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
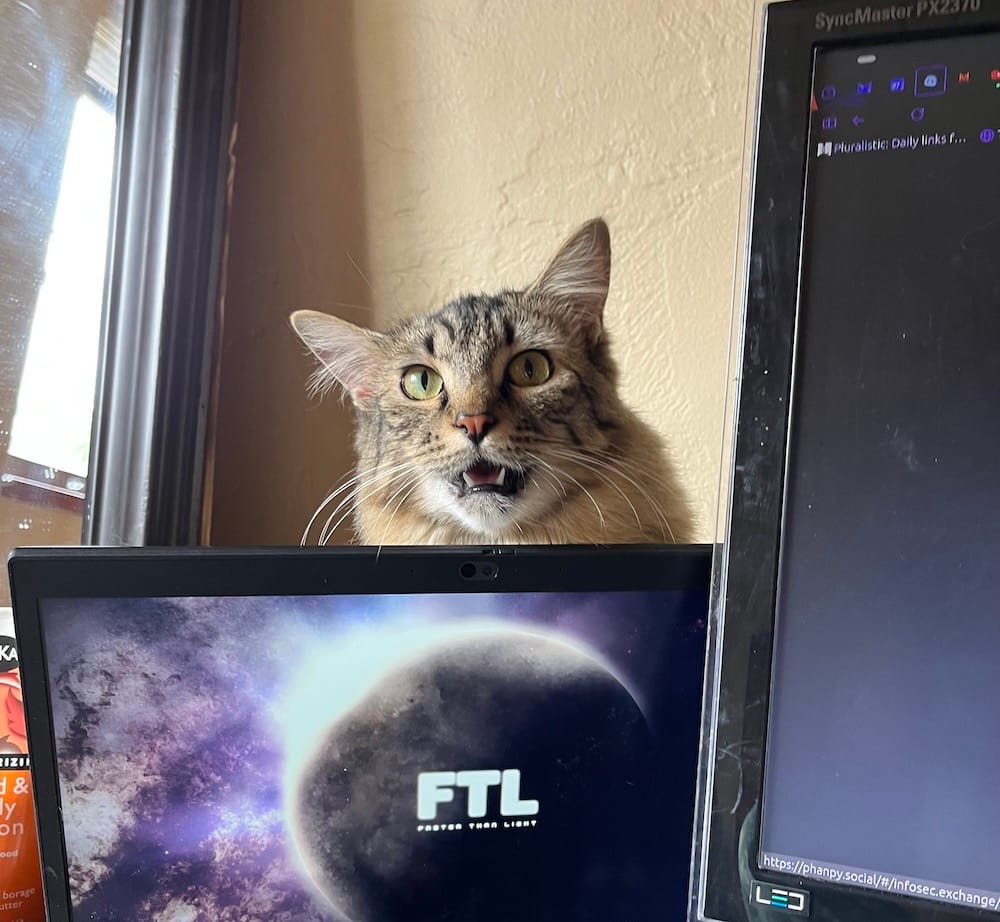
This week's cyber cat is Maharet, who can be seen here taking workplace surveillance to a whole new level. Thanks so much to Sampo for sending in!
🐈 Send in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Drop me an email with their photo and name and they will be featured in a later newsletter!
~ ~
SUGGESTION BOX
And that's it for this week's edition of ~this week in security~. Thanks so much for reading and subscribing! I'll let you get back to your weekend, and I'll catch you again next week!
If you have anything for the newsletter, please do get in touch, it's great to hear from you.
À bientôt,
@zackwhittaker