this week in security — october 26 2025 edition
THIS WEEK, TL;DR
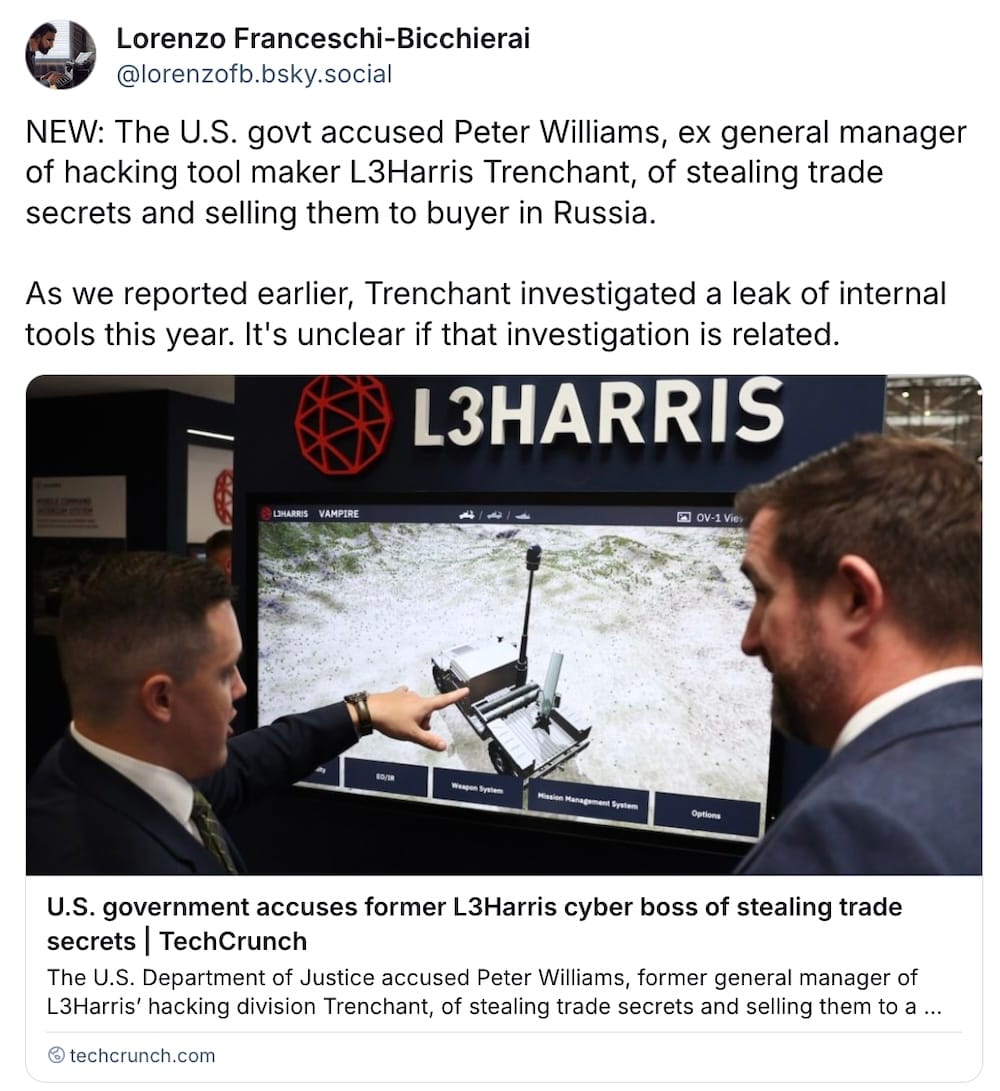
L3Harris hacking unit boss accused of selling secrets to Russian buyer
TechCrunch ($): Absolutely wild reporting here from @lorenzofb. The U.S. government has accused Peter Williams, the former general manager of Trenchant, the L3Harris unit that makes hacking tools and exploits for Western governments, of two felony counts of stealing trade secrets to the tune of $1.3 million for a buyer in Russia. We don't know what the trade secrets are or who the buyer is but… 👀 This comes in the same week that @lorenzofb first reported that Trenchant was investigating a leak of company-made exploits. A former Trenchant exploit developer was blamed for the leaks and fired, but he vehemently denied the allegations. The former developer came forward and told his story because weeks after getting fired, he got a threat alert from Apple saying his personal iPhone was targeted with mercenary spyware, thought to be the first publicly documented case of someone working in the spyware-making industry being targeted. Williams will be in court Wednesday for a plea hearing, where we may learn more.
More: TechCrunch ($) | DocumentCloud | Bloomberg ($) | Reuters ($) | Cyberscoop | @lorenzofb | @patrickhowelloneill
U.S. is 'slipping' on cybersecurity, says report, as federal shutdown continues
Cyberscoop: The successor organization to the bipartisan Cyberspace Solarium Commission has issued a dire warning on the state of the U.S.' cyber posture: "Our nation’s ability to protect itself and its allies from cyber threats is stalling and, in several areas, slipping,” said the report. It's no major surprise that months of Trump administration cuts and layoffs have hammered CISA, and the ongoing federal shutdown has resulted in even more layoffs. Axios ($) notes that much of CISA's information sharing efforts have gone dark, which isn't exactly great timing since many are still dealing with the aftermath of F5's breach by nation-state hackers. Meanwhile, CSO Online looks at the state of enterprise network security devices (hint: it's not great!) and why a never-ending stream of bugs in these devices allow hackers to walk right into a corporate victim's network.
More: CSC 2.0 | Cybersecurity Dive | Axios ($) | The New York Times ($) | Cyberscoop
Jaguar Land Rover said to be 'costliest' cyberattack in U.K. history
BBC News: Analysts say the hack targeting Jaguar Land Rover in late August is the most financially damaging cyber incident to have ever hit the U.K., reaching a cost of almost £2 billion ($2.6b), at a time when the U.K. economy remains slow. Experts monitoring the aftermath of the disruptive hack say around 5,000 companies in JLR's supply chain were affected by the outage, which stalled the car-making giant's production lines for weeks. A complete recovery still isn't anticipated until next year. But as the experts note, JLR still hasn't disclosed how much damage the hack did to its systems, as ransomware is more complex and costlier to recover from than a data theft attack. What's clear is that JLR is a huge company that is relied on by thousands of companies, and got caught out by a cyberattack, and clearly didn't have enough of a contingency plan in place.
More: Cyber Monitoring Center | The Guardian ($)
Windows Server Update Services bug under attack
Huntress: Security researchers at Huntress say they've seen evidence that a newly discovered bug in Windows Server Update Service (aka WSUS), tracked as CVE-2025-59287, is being maliciously exploited in the wild. WSUS allows network admins to patch their entire fleets of Windows devices with security updates. Huntress has seen four of its customers compromised, and has both guidance and indicators of compromise for network defenders and threat hunters. Per @GossiTheDog, the bug can be exploited to achieve code execution on an affected server over the internet to deliver malicious code to downstream Windows PCs. Patch today!
More: Bleeping Computer | Microsoft | Hawktrace | Eye Security
~ ~
THE STUFF YOU MIGHT'VE MISSED
OpenAI ordered to turn over ChatGPT prompts to feds
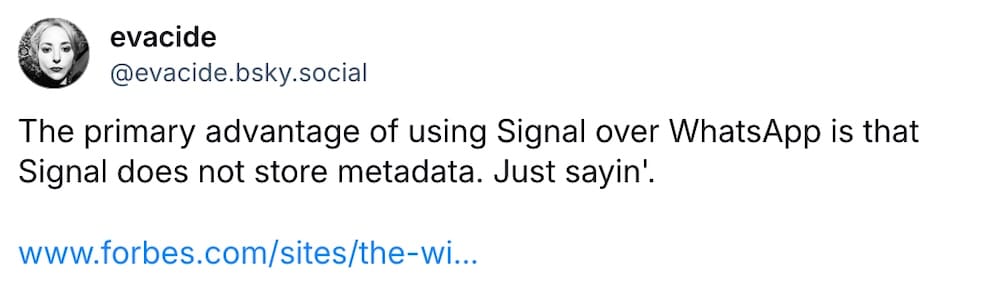
Forbes ($): Homeland Security investigators have demanded that OpenAI turn over prompts submitted by one ChatGPT user, who is accused of running a child exploitation site. The warrant — the first-known warrant targeting a ChatGPT user — proves that police can access the same prompts that users ask the chatbot, similar to a "reverse search" warrant. Cyber law expert @riana has several questions about the warrant worth considering. Meanwhile: @thomasbrewster also explores how ICE demands metadata from WhatsApp, which can include information about who you talk to on the app.
TikTok won't say if it's giving ICE your data
Forbes ($): Sticking with Forbes reporting on data demands… Earlier this year as part of a deal to keep TikTok active in the U.S. following a federal ban, TikTok effectively weakened its privacy policies to allow law enforcement officers to demand user data from the company without notifying affected users. Forbes repeatedly asked TikTok if it will give user data to the government, and its response was extremely weaksauce. More from The Verge ($) and Wired ($) this week on ICE's surveillance efforts.
Misbehaving AI Corner: Gaming Copilot and AI 'safety' systems
Microsoft has begun rolling out Gaming Copilot (to the surprise of gamers themselves), a "feature" (the heaviest of air quotes here) in Windows 11 that takes screenshots of the gamer's screen to give them help, hints, and tips for game-play. Some are likening the feature to Microsoft's problematic Recall product. Microsoft told Tom's Hardware that Gaming Copilot is "not used to train AI models," but it's still unclear why Gaming Copilot is sending data back to Microsoft's servers.
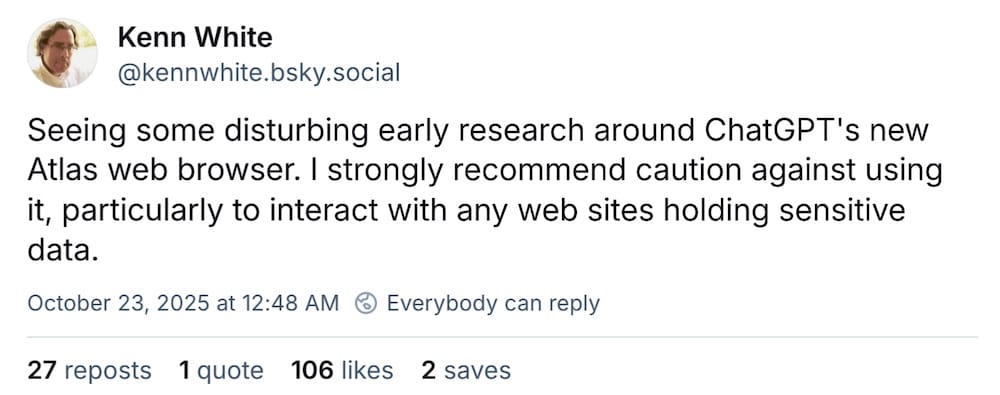
AI browsers are a hot mess of security risks
this week in security: Staying with AI for a minute… AI browsers are now a thing, from Perplexity's Comet to OpenAI's ChatGPT Atlas. But baking in AI to a web browser, something that is mission-critical to our everyday lives, comes with new security risks. This includes an entire class of "prompt injection" attacks that can steal data from your AI browser (such as credit card numbers to passwords) just by asking it — no zero-days needed. Both Comet and ChatGPT's Atlas are vulnerable to prompt injection attacks. All to say, use extreme caution! The browser you use is important, and some are better than others, as Wired ($) reported recently. More from Bleeping Computer and TechCrunch.
iOS 26 wipes evidence of spyware on reboot
iVerify: The folks at security firm iVerify say Apple's latest mobile software, iOS 26, wipes an important log file when a user restarts their iPhone or iPad. Researchers have historically used this shutdown log file to identify signs of spyware infection, like NSO Group's Pegasus and Intellexa's Predator.
~ ~
~this week in security~ is my free weekly cybersecurity newsletter supported by readers like you. Please consider signing-up for a premium subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
OTHER NEWSY NUGGETS
Dutch are sharing less with the U.S.: Dutch intelligence are sharing less intelligence with their American counterparts under Trump, according to the agencies' top directors, citing a "politicization of intelligence and to human rights violations." This was said during an on-the-record interview, so these were quite intentional remarks. (via Volkskrant ($), Dutch News)
Apple jettisons tea-spilling apps from App Store: Apple has pulled Tea and TeaOnHer from its app stores. The two apps allowed people to share information about who they've dated under the guise of personal safety. But the apps both had a rash of security flaws that exposed users' government-issued IDs and selfies, which the apps required users to upload before they could access the apps. Apple allowed the apps to stay on its app store after the breaches, but belatedly pulled the plug this week citing user privacy and complaints. (via 404 Media ($), TechCrunch ($))
It's always DNS, Amazon outage edition: Amazon started the week with a global snow day after an internal DNS failure took out a good chunk of the internet for much of Monday, from banks to internet-connected mattresses. The outage wasn't a cyberattack, according to a post-mortem, but shows how reliant we are on just three cloud providers. (via Amazon, Ars Technica, this week in security)
Xubuntu website serving malware: Eagle eye observers found Xubuntu's downloads page was serving malware. Early indications suggest the malware may try to steal data from a victim's clipboard memory. @bluesabre confirmed the incident in a Mastodon post. (via Reddit, HelpNetSecurity, The Register)
DOJ indicts alleged poker hackers: Prosecutors have charged 31 people, including an NBA coach and others with links to the mob, who are accused of scamming $7 million from rigged poker games that relied on using hacked card-shuffling machines. (Wasn't this a movie already?) (via Wired ($), NPR, Justice Department)
Collins Aerospace hack claimed by ransomware gang: Dublin Airport, one of the many European airports hit by a ransomware-related outage on airport check-in system maker Collins Aerospace, now says passenger data may have been stolen, including boarding passes. The Everest ransomware gang took credit for the breach. Since many airports were affected by the outage, we may expect even more passenger data to leak. (via The Journal)
~ ~
THE HAPPY CORNER
Ding, dong! That's the sound of the happy corner gong.
An early bonus cybercat this week with Tigger, who can be seen here preparing for the spooky season. (If you have any Halloween-related cybercats, please send in!)

Here's a fun story — well, it's fun now that it's been over a decade since it happened — about how an outage involving an internal password manager at Google resulted in an almost comical list of "how many ways can this go wrong." In the end, the password manager was liberated by a power drill. But there is a lesson here about contingency planning and also… well, testing it.
I very much enjoyed this "nope" sign at my local #NoKings rally last weekend.
And finally, some thoughts via Inspirational Skeletor. Whether it's politics, or cybersecurity, or something else entirely, sometimes it can feel hopeless in the world, especially when we're being sh*t on from a great height. But don't give up. We all have so much love to give, and there is a lot more work to do to make this world better for everyone. Things don't get better unless we make them happen. Today is a better day than ever to remember that, and a reminder to keep going. And yes, you can swear and cuss the whole time you're doing it.

Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Molly from back in her kitten days, thinking about all the amazing hacking escapades she'll get up to when she's all grown up. Thank you so much to her anonymous human for sending in!

🐈 Send in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a later newsletter!
~ ~
SUGGESTION BOX
And that's it for this edition — sent from California this week (hence why it's a little later than usual). Thanks for reading and making it through! Join me again next Sunday with your usual cyber roundup with everything you need to know.
If you want to get in touch (and please do!) or with something for the newsletter, drop me an email at any time! I love hearing from you (especially when there's a cyber cat or friend attached!).
Keep smiling.
@zackwhittaker