this week in security — october 5 2025 edition
THIS WEEK, TL;DR
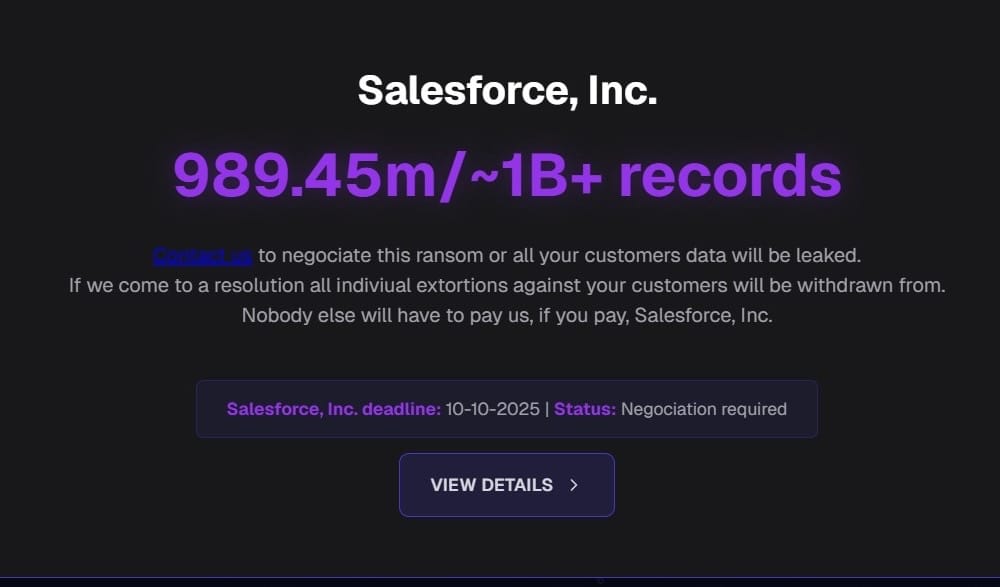
ShinyHunters claim 1 billion records stolen from Salesforce customers
TechCrunch ($): And there it is, after months of stealing huge amounts of customer data from Salesforce-hosted instances, the prolific hacking collective Scattered LAPSUS$ Hunters (thought to be a mix of several known hacking groups) has shown its hand, claiming to have stolen a billion records as part of its mass-hacking campaign. After targeting big name brands who store data in Salesforce, the hackers published a data leak site threatening to publish the stolen data if the victim companies don't pay their extortion demand. There are dozens of companies listed, like Toyota, FedEx, and Disney/Hulu (which didn't respond to our requests for comment) and some known victims that aren't listed, like TransUnion and Workday. (Shiny wouldn't say why when I asked, but it's probably because they're still negotiating a ransom.) The hackers' demands expire on October 10, so we may see more from the hacking group of groups. It's not too late to harden your Salesforce data. (Disclosure: I co-wrote this story with @lorenzofb!)
More: DataBreaches.net | Reuters ($) | BankInfoSecurity | CSO Online | Bleeping Computer | Google Cloud
Executives extorted with claims of stolen data from Oracle apps
Bloomberg ($): Not to be outdone, hackers thought to be associated with the Clop ransomware gang have been observed sending hundreds of extortion emails threatening corporate and tech executives with demands to pay up or have their personal information published. Google and Halcyon researchers said this week that the hackers appear to have hacked customers' Oracle E-Business Suite servers, which corporate customers use to host tons of internal operational and HR data. One executive got a ransom demand for $50 million, per Bloomberg. Cyberscoop has a copy of the extortion letter. Oracle said it was "aware" some of its customers received extortion demands and said it found the "potential use of previously identified vulnerabilities" patched in July, suggesting that the flaws used to steal data were not zero-days.
More: Oracle | Cyberscoop | The Record
U.S. government shuts down and takes cyber-sharing law down with it
CSO Online: Cybersecurity Awareness Month started a little differently this year, with U.S. cybersecurity agency CISA announcing the month's "official beginning" on… September 29… for reasons that only seem to make sense if the U.S. government was about to summarily shut down days later on October 1… which it did. Due to a weird quirk of constitutionality seemingly unique to the United States, hundreds of thousands of federal workers now won't get paid and the programs and services they support won't get funding until Congress agrees on a deal to fund the federal government. U.S. cyber intelligence sharing law, dubbed CISA 2015 (confusingly unrelated to the federal agency), has now lapsed, as the law wasn't extended amid the political deadlock, meaning that the U.S. government loses a ton of cyber threat visibility into the private sector and the private sector loses liability protections for sharing information that can help to defend against cyberattacks. tl;dr: Everyone is losing here.
More: Washington Post ($) | Cybersecurity Dive | @doublepulsar
Data breach roundup: WestJet, Asahi, FEMA, Renault U.K., Discord
OK, we have a fair number of these to blast through so… we start with… *breathes in heavily* WestJet confirms its June data breach affects 1.2 million people… South Korea's had pretty much a hack every month since the start of the year… FEMA and CBP's breach that got dozens fired was way worse than first claimed… Asahi beer is running dry(!) after a ransomware attack, per Reuters ($)… Allianz Life's hack reaches 1.5 million people… Jaguar Land Rover might be back online as soon as this week, but missed major cyber blind-spots prior to its hack, Bloomberg ($) reports. Speaking of carmakers, Renault U.K. had a "third-party" database popped… and… Discord said users' IDs used for age verification checks were stolen — yeah, I had a little rant about that one…
More: Nextgov | Bloomberg ($) | TechCrunch | ~this week in security~ ($) | @troyhunt
~ ~
THE STUFF YOU MIGHT'VE MISSED
U.K. government tries to backdoor Apple iCloud, take two
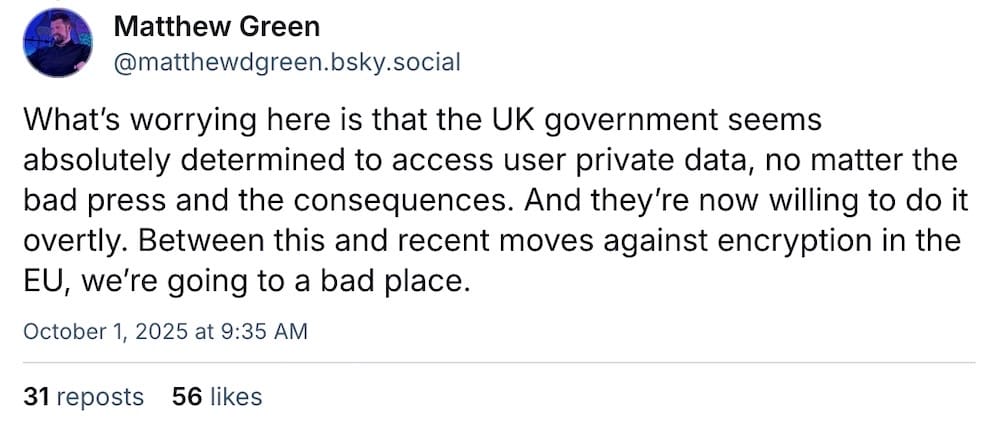
Financial Times ($): The U.K. government is back, again, with another attempt to legally force Apple to backdoor its iCloud. This time, though, the U.K. wants to narrow the demand so it can access any encrypted British user's data stored worldwide, rather than any user's data anywhere in the world. Narrowing the backdoor is still a backdoor. Good thread by @matthewdgreen.
Amazon Ring cameras to get facial recognition
Washington Post ($): A new surveillance hellscape just dropped… The Amazon-owned video doorbell maker and surveillance giant Ring is rolling out facial recognition to its customers' cameras, allowing Amazon to collect biometric information on people who are simply… walking past. Friends don't let friends use Ring cameras, let alone with facial recognition, so please don't mind if I don't want to come over for dinner.
Privacy for me but not for thee: Ted Cruz edition
TechCrunch ($): Cancun enthusiast Ted Cruz voted down a bill that would have banned invasive data brokers from selling their personal information on anyone in the United States, rather than just lawmakers and government officials. Ron Wyden, who proposed the bill, said, “Members of Congress should not receive special treatment." But Cruz said, wrongly, that extending those protections to everyone would make it more difficult for police to know where sex offenders are. (Disclosure: I wrote this story!)
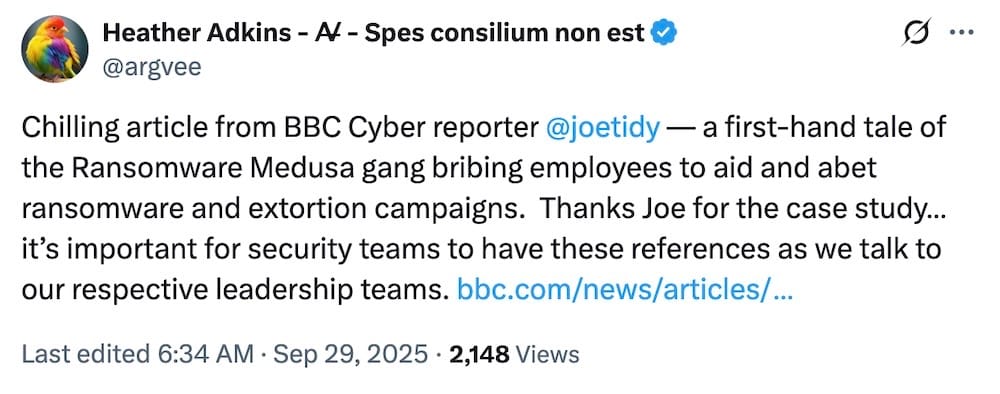
Criminal hackers offer reporter money to hack BBC
BBC News: BBC's cyber reporter @joetidy did a stellar job in this story describing what it was like to be offered money to hack his employer, the BBC, so that the hackers could deploy ransomware. Chilling stuff to read, and excellently told from Tidy's first-hand perspective. Tidy experienced what a lot of victims face when being hit by floods of password resets and "MFA-bombing" attempts. One wrong move and the hackers can walk in. Risky.biz has a cracking podcast on the story, too.
Why burnout is a growing problem in cybersecurity
BBC News: Another good story here from the Beeb this week, looking at the state of burnout across the cybersecurity industry. Particularly in cyber, people are your best asset, but companies (and governments) are not spending enough on cybersecurity at large, or the people who are on the digital front lines.
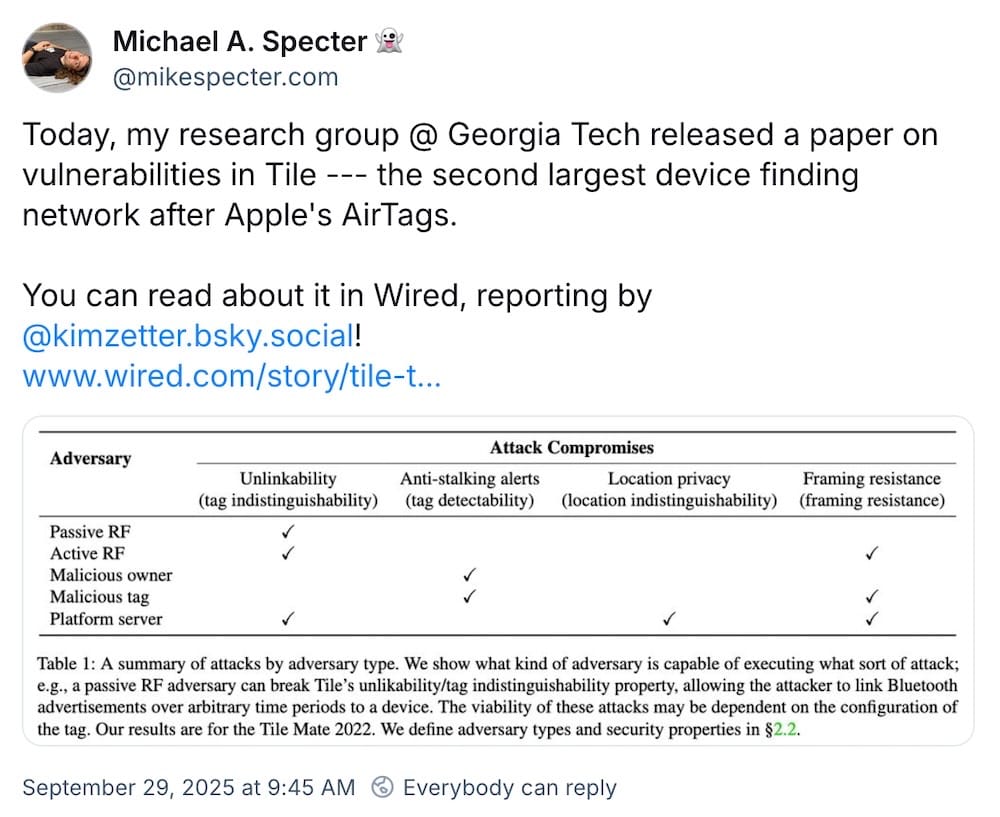
How Tile tracking tags can be exploited by stalkers
Wired ($): Academics discovered that reveal Tile location tracking tags are not encrypting their location data or their unique identifiers, which can be "picked up by other Bluetooth devices or radio-frequency antennas in a tag’s vicinity to track the movements of the tag and its owner" and enable surveillance. More from The Register, The Verge ($), as well as @mikespecter, whose team found the flaws.
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. As a working journalist, I don't run ads or accept sponsors for this newsletter.
Please consider signing-up for a premium subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
OTHER NEWSY NUGGETS
Columbus class action craps out: A judge was forced to dismiss a class action lawsuit against the City of Columbus in Ohio following a ransomware attack in 2024, which affected over 500,000 people in the city, because of immunity under state law. Yes, this is the same city that sued a security researcher for accurately describing the true nature of the breach, which the city tried to cover up, but whose residents get nothing to protect themselves. (via @PogoWasRight, FOX28)
Hackers steal Red Hat customer files: Hackers calling themselves The Crimson Collective say they've stolen hundreds of customer engagement files from Red Hat's consultancy business. These files can contain network architecture diagrams, configs, authentication tokens, and more — or, as The Register notes, "effectively a blueprint of a customer's IT environment." Red Hat confirmed the breach. (via 404 Media ($), Bleeping Computer)
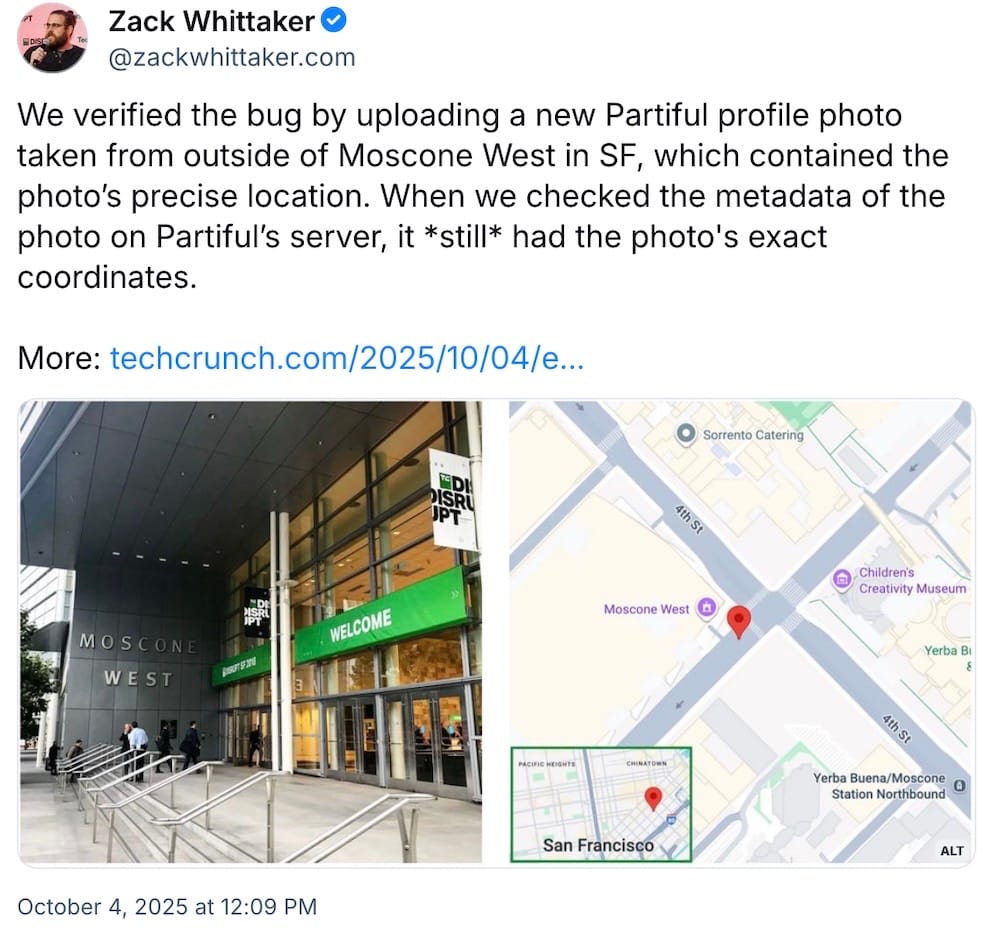
Partiful forgot to strip GPS data: Captain Buzzkill here with another vibe-killing bug. (Disclosure alert!) My colleague @amanda.omg.lol and I found that event planning startup Partiful wasn't stripping GPS location data from user-uploaded photos, allowing anyone to see where users' profile photos were taken. The bug is now fixed and metadata removed from Partiful's servers after we alerted the startup. (via TechCrunch, @zackwhittaker)
Bullet crashes internet in Texas: Internet suddenly crashed? It's almost always DNS… except when it's actually BGP… or squirrels chewing through a fiber cable. This time, though, it was a stray bullet causing a mass internet outage to 25,000 people across Texas. (via 404 Media ($), WFAA)
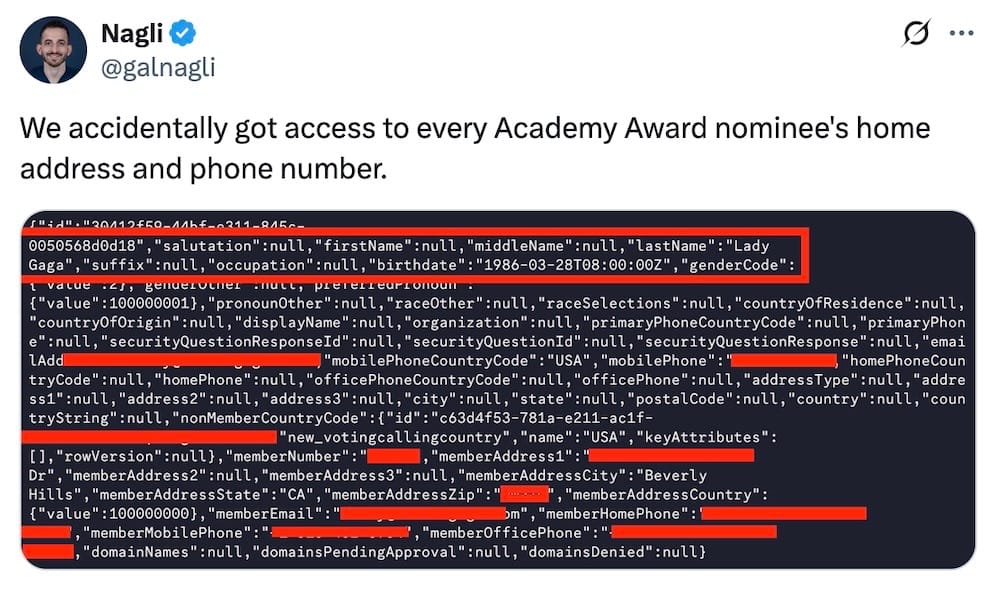
Academy Awards all-access API: Wiz security researcher @galnagli posted on X about a now-fided publicly exposed API belonging to the Academy Awards (aka the Oscars), which was leaking the personal information of every nominee, including their phone numbers and home addresses.
Misbehaving AI Corner: I don't know who needs to hear this (anyone? everyone?) but it's really not a good idea to allow an autonomous AI agent to act on your behalf at the best of times, let alone when given your credit card and the ability to buy stuff online. But that's where we are. (via @RachelTobac) Meanwhile: LayerX Security found a bug that showed it was easy to trick Perplexity's Comet browser (which has AI baked in) into stealing a user's data.
Signal: Et tu, Germany? Signal accused Germany of being on the "verge of a catastrophic about-face" by reportedly reversing its opposition to Chat Control, a EU effort to mass-scan the private messages of millions of people. Signal said Germany "must hold the line" in opposing Chat Control, and warned Signal would "leave the market" rather than comply with surveilling its users. (via @signalapp [PDF], EFF, Mozilla Foundation)
~ ~
THE HAPPY CORNER
At last. It's the happy corner, the much-needed salve for that hellish week.
Just checking in on one of my favorite hacker friends @akacki.net for some wholesome good advice. Drop the doomscrolling and hack the planet!

My personal pick of this week's favorite memes goes to this gem. Also, it's generally just good advice!
Speaking of good advice, Consumer Reports (via @yaelwrites) has published its latest annual consumer cyber readiness report, taking a deep look at the attitudes towards digital privacy and security across America and what folks are doing to protect themselves. Talk about news you can use and guidance you can take, this report has you covered. (via Consumer Reports)
And, bonus cybercat, from my own personal collection.
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cyber-cat special features Skye and Ginger, who can be seen here guarding the security perimeter from inbound threats. Thanks so much to Cathy S. for sending in!

🐈 Send in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a later newsletter!
~ ~
SUGGESTION BOX
And that's all there is for this... very busy, mixed bag of news this week. Join me next week for the usual roundup from the past seven days and more.
If you have anything to share for the newsletter, from good news and cybercats to feedback and suggestions, I love to hear from you so please get in touch.
Enjoy the rest of your Sunday, and hope you have a great rest of your week. I'm off to hack the planet, too. :)
Until next time,
@zackwhittaker