this week in security — september 14 2025 edition
THIS WEEK, TL;DR
Investigation shows U.S. tech companies built and enabled much of China's surveillance state
Associated Press: We start this week with an(other) breathtakingly deep and detailed investigation by @yaelwrites and @dakekang on the Chinese surveillance state. This is one of the most detailed and thorough investigations, based largely on leaked documents but also extensive sourcing. The investigation digs into how some of the largest U.S. tech giants knowingly promoted and sold their technology to support the Chinese surveillance state. This incredible feature set of stories follows how the tech giants got there, and profited from enabling China's mass spying and detention programs, as well as developing technologies like predictive policing to monitor people deemed suspicious, which is staggeringly bad since this can accuse people of crimes they haven't committed. This tech has enabled crackdowns and allowed the controlling and persecution of countless citizens. If this tells us one thing: If you collect data, it can be used against you. This is pretty grim stuff, but important and necessary reading.
More: Associated Press | Tibetan Review | China Digital Times | @byrontau | @yaelwrites

Pakistan spying on millions through Chinese phone tapping and web spying tech
Amnesty International: Since we're talking about surveillance tech… Amnesty International's latest research uncovered a trove of documents revealing how Pakistan restricts citizens' access to phones and the internet under a Chinese-made surveillance and monitoring system akin to a commercialized version of China's "Great Firewall." The tech, developed by China-based Geedge Networks, allows Pakistan and several other countries to monitor, intercept and hack web traffic, as well as track the locations of phones, calls and text messages. Wired ($)'s reporters dive into the story with more color from the lens of how China's exported surveillance works and functions, both as a political ideology for China but also a major economic driver.
More: Bloomberg ($) | Reuters ($) | Great Firewall Report | Jurist News | @DrWhax | @hatr
Salesloft breach caused by March breach of GitHub account
DataBreaches.net: Following the breach at Salesloft a few weeks ago that ensnared some of its biggest customers, Mandiant was called in to investigate, and its findings reveal that hackers broke in as far back as March to Salesloft's GitHub account and pivoted from there. The breach wasn't detected for almost six months, and not until the hackers (said to be the ShinyHunters groups) stole gobs of data from customers' connected Salesforce instances. These hacks now include high-end fashion retailers, including Gucci and Alexander McQueen, among dozens of other tech companies. DataBreaches.net has consistently done some of the best reporting on this entire saga. Expect at some point for these hacks to reach a peak, potentially by way of publicly naming and extorting their victims. The FBI (finally) put out an alert this week [PDF] for companies to know what threat activity to look out for. Expect a lot of data breach notices to come down the line…
More: TechCrunch | SecurityWeek | ~this week in security~ ($)
Apple's new iPhones can block memory-based hacks, favored by spyware makers
TechCrunch ($): Some (early) good news this week — if you have a casual grand to spend, of course. Buried in a sea of product announcements revealed by Apple, the tech giant also published a blog that detailed a five-year effort called Memory Integrity Enforcement (sounds boring, but read on) to reduce the memory-unsafe footprint of its latest iPhone 17 and iPhone Air. By locking down the device's memory, Apple says it can reduce the majority of memory-related bugs (such as buffer overflows and memory corruption bugs) that spyware makers and exploit developers just love to use to hack iPhone users. This is a pretty smart move by Apple, one that aims to make it significantly more challenging for spyware makers to find these bugs. (Disclosure alert: I co-wrote this story!) It's already causing some exploit makers to rethink their approach. Meanwhile: The French government said Apple notified victims of a spyware attack as recently as September 3, showing the spyware threat is very present. (Disclosure: I wrote this too!)
More: Apple | Cyberscoop | Wired ($) | The Verge ($) | @pwnallthethings
Vietnam investigates breach of country's creditors data
Reuters ($): Another potentially big data breach may affect the entire population of Vietnam. Per DataBreaches.net, the ShinyHunters group claimed to have stolen some 160 million records from Vietnam's top state bank, including historical records (hence the number larger than the population) revealing huge amounts of credit information on the country's citizens. Resecurity has good analysis on the breach, including obtaining and analyzing samples of stolen data. Vietnam media confirmed the breach, with the country's computer emergency readiness team investigating. The bank issued a statement, but hasn't really said much about the breach yet. Relatedly: Panama's finance ministry was hacked by the INC ransomware gang, which took credit for stealing 1.5 terabytes of data.
More: Vietnam News | The Record | @pogowasright
THE STUFF YOU MIGHT'VE MISSED
Oura ring deal raises valid concerns about users' health data security
~this week in security~ ($): For the past couple of weeks, Oura customers have expressed fury over a deal between the wearable smart ring maker and the U.S. Dept. of Defense. Oura denied it was sharing users' data with the government, but the furor raised valid and justified concerns about where and how Oura stores customers' data, and who has access to it. Oura told me that some staff have access to customers' information, and that the company has received demands for customer data from the U.S. government.
How (and why) Mandiant's first 'APT1' report came to be
Zero Day: Here's @kimzetter with the inside story of how Mandiant, a little-known security firm at the time, published its first report into APT1 in 2013, which exposed a prolific Chinese military hacking unit said to be made up of thousands of hackers. The report paved the way for the first ever indictment of a nation-state hacker, and how security firms report threat activity in the future.
Here's the tech powering ICE's deportation crackdown
Forbes ($): Both Forbes ($) and TechCrunch ($) dig into the various tech, from spyware and facial recognition to the police forensic devices used for hacking into people's phones, that U.S. immigration authorities are using to target foreign nationals and surveil U.S. citizens. The U.S. government has spent millions on this tech over the past few years through successive administrations. Also: Texas Observer has a deeply reported story on a surveillance tower that looms over Mexico's Chihuahua state, which borders Texas.
Microsoft 'Kerberoasting' bug allegedly led to massive Ascension breach
CSO Online: Microsoft is in hot water again for its security practices after Sen. Ron Wyden blamed Microsoft for failings that allegedly led to a ransomware attack on Ascension Health, which saw data on at least 5.6 million people stolen. Wyden said the hackers exploited a technique known as "kerberoasting" (more here as well), which allows attackers to gather passwords by targeting the decades-old Kerberos protocol. Wyden said since Microsoft has a multi-billion dollar business selling cybersecurity, this was like "an arsonist selling firefighting services to their victims.” Woof, straight to the burns unit....
Hacking into a digital safe, with Andy Greenberg
Wired ($): During Def Con in August, security researchers revealed [PDF] how they found backdoors in a lineup of popular safes. Now there's a video of the shenanigans with Wired's @agreenberg that's well worth checking out.

Major npm supply chain attack hits millions but whimpers out
KrebsOnSecurity: Wild stuff here as at least 18 popular code packages hosted by npm were hacked by way of a phish targeting a key npm developer. The packages were modified to steal cryptocurrency from downstream projects. This supply chain attack almost turned into a five-alarm fire, had the malware component been anything other than focused on stealing crypto. There is a major cautionary tale here: be mindful of what third-party software you use, as it can be really difficult knowing if that code hasn't been manipulated in some way. In potentially related news: Canadian fintech firm WealthSimple said it was hit by a data breach because a "specific software package that was written by a trusted third party had been compromised." See? This does happen…
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. As a working journalist, I don't run ads or accept sponsors for this newsletter. Please sign-up for a premium subscription for exclusive articles, analysis, and more.
OTHER NEWSY NUGGETS
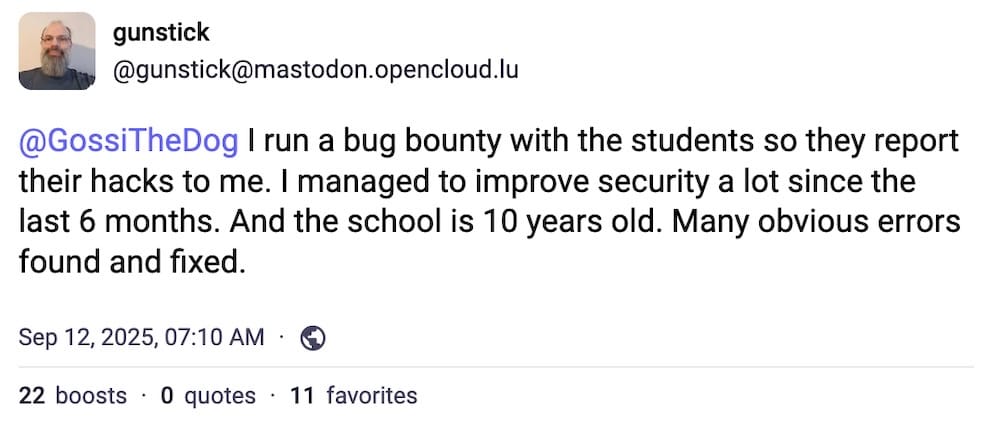
Kids caught hacking their own schools: The U.K.'s data protection watchdog says kids are increasingly hacking into their own schools, often for dares and giggles, but also warns of a rise of potentially malicious insider attacks. Given how "advanced persistent teenagers" like Scattered Spider and the like are as prolific as they are, hacker kids are not some low-level or nebulous threat. Also, U.K. schools are horrendously underfunded. (via BBC News, @gunstick)
WhatsApp security boss blows the whistle: The now-former head of security at WhatsApp filed a lawsuit claiming the encrypted messaging app's backend systems lacked user access controls, allowing employees access to some users' unencrypted data, like locations and profile pictures, and failed to enact basic cybersecurity measures, like auditing and logging. WhatsApp end-to-end encrypts your calls and messages, but still doesn't fully encrypt users' metadata. (via The New York Times ($), The Guardian)
Plex says reset passwords after breach: The streaming software giant urged users to reset their passwords after its user accounts database was popped, exposing users' email addresses and scrambled passwords. Plex said very little about the breach, nor how it encrypted user passwords, which matters since some hashing algorithms can be cracked. (Disclosure: I wrote this story!) (via TechCrunch ($), Plex)
Proton nukes journalist's accounts: Two journalists who go by the handles Saber and cyb0rg, who recently exposed a suspected North Korean government hacker in a report for the latest issue of the Phrack magazine, now say that the privacy-focused email provider Proton suspended their email accounts, which the journalists say were used for coordinating responsible disclosure. Not a good look here for Proton. Adjust your threat models accordingly! (via The Intercept ($), @phrack)
Jaguar Land Rover cyberattack drags on: The suspected ransomware attack on the U.K.-based carmaking giant Jaguar Land Rover may last until at least October, per reports, as the breach ground the company's production line to a halt. The company said some data was stolen from its systems, but didn't say what kinds or who it relates to. Some downstream companies that rely on JLR are already facing bankruptcy. (via The Guardian ($), BBC News)
EU at crossroads over encryption backdoors: I lose track of how many times a government, not least the collective nations of Europe, have tried to backdoor people's private communications under the guise of child safety, but here we are again… Brussels is looking at legislation aimed at backdooring encryption, despite hundreds of security experts [PDF] saying — once again — that this cannot be done securely without also putting everyone's data at risk. (via The Register, Patrick Breyer)
U.S. warn of hidden radios in highway tech: A four-page security note from the U.S. Federal Highway Administration, seen by Reuters, said undocumented cellular radios had been found “in certain foreign-manufactured power inverters and [battery management systems]," used in roadside U.S. transportation infrastructure. The note said roadside chargers, roadside weather stations, and traffic cameras should be scanned for suspected radios. (via Reuters ($), @janawinter)
THE HAPPY CORNER
Not a moment longer, welcome — at last — to the happy corner. And look, this might be a mood, but admittedly I did laugh at this:
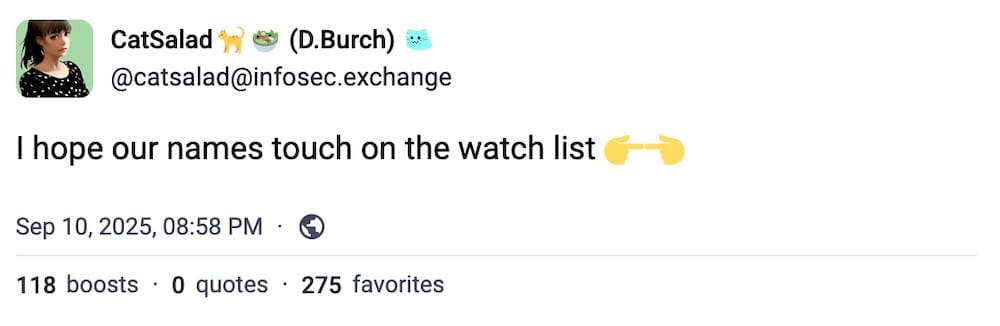
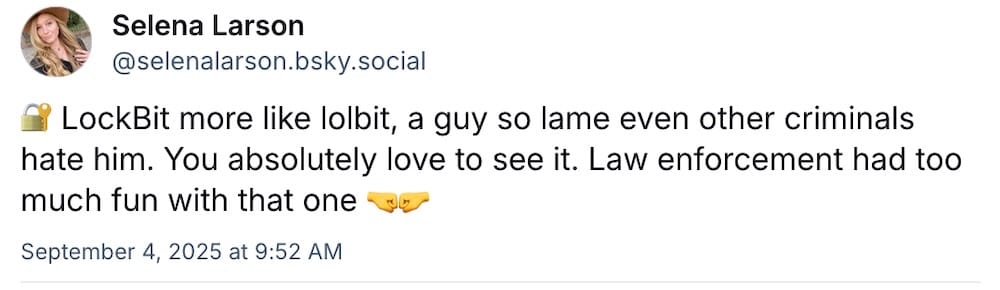
A huge congrats to @ransomwaresommelier for the successful launch and backing of The Green Archer, the latest in a series of comics. I absolutely cannot wait to get my hands on a copy, I'm a huge fan — and you can still lend your support. And, to sweeten the deal, the very excellent @selenalarson has gifted the world some of the most savage hacker roasts for your reading enjoyment. My personal favorite:
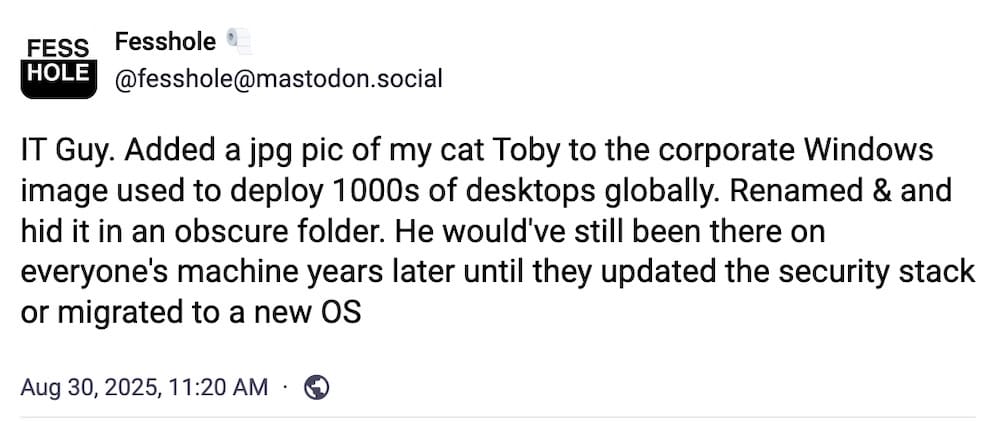
Now this is a good confession:
A little late to this, but Qantas executives got their bonuses cut after the airline's massive data breach earlier this year. The company's top leadership's bonuses will be cut by 15%, amounting to about $250,000 for the CEO. *spits out tea* …is this accountability?!
And lastly. Someone made an iPhone "dumbphone", and I'm absolutely here for it. This actually might be a good idea for kids and parents.
Share your good news at this@weekinsecurity.com.
CYBER CATS & FRIENDS
This week's cyber cat pupper is Toby, who can be seen here dressed to the max and ready to enjoy a night on the town, maybe check out a casino or two, maybe the slots. Don't worry about those blueprints... or the nightvision goggles... or that bag of exploits... woof woof... ("no heists here!") Thanks so much to Amanda H. for sending in!

Keep sending in your cyber cats! Got a cyber-cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a future newsletter!
SUGGESTION BOX
It's really nice to be back after a week away (and much needed)... even if the news this week was, let's be honest, overwhelmingly hot garbage. Thank you for sticking around and reading, it really means the world.
I'll be back next Sunday with the usual roundup from the week. And, as always, please do get in touch if you've got anything to share for the newsletter, a cyber-cat or friend, or just want to say hi.
Enjoy the rest of your weekend.
Ta ta, for now.
@zackwhittaker