this week in security — september 21 2025 edition
THIS WEEK, TL;DR
Jaguar Land Rover cyberattack harming U.K. supply chain, downstream businesses
Financial Times; Ars Technica: We start in the U.K. at Jaguar Land Rover, the automotive giant owned by Tata Motors, which remains offline after more than three weeks with no vehicle production following a cyberattack in late August. With billions in annual revenue, JLR will probably recover just fine, but the downstream effect on companies that provide parts and products to JLR are already going under, amid warnings of broader economic harm as a result of the hack. The U.K. government is waking up to the problem, but not fast enough. There's still no timeline for JLR's recovery, and every day is wiping millions of pounds from the British economy, with thousands of JLR employees told not to report to work. The U.K. is close to having its "Change Healthcare" moment; essentially a company that's too big to fail (but still wants to try anyway). You must read this yarn from @GossiTheDog, who lays out in a blog why outsourcing IT and security is much the reason for JLR's hot mess.
More: Gov.uk | The Record | Double Pulsar ($) | @GossiTheDog
U.S., U.K. charge key 'Scattered Spider' member with dozens of hacks
National Crime Agency: The plods in London nabbed one of the key figures in the Scattered Spider hacking group, arresting and charging Thalha Jubair, 19, in a London court alongside another teenager with the Transport for London hack last year. Jubair was also slapped at the same time with federal charges filed in New Jersey, accusing him of hacking into at least 120 companies, some 47 companies in the U.S., and making some $115 million in ransom payments. The indictment is just wild reading; Jubair is painted as one of the most prolific hackers of today (and may well be if found guilty). He's also accused of breaking into a critical infrastructure organization and the U.S. Courts system as part of an effort to access the sealed indictment of fellow accused Scattered Spider hacker, Noah Urban, who was separately profiled by Bloomberg ($) this week. Relatedly: A teenager who is suspected of involvement in two 2023 hacks targeting casinos on the Las Vegas strip (likely MGM and Caesars), which were largely attributed to Scattered Spider, turned himself into police this week, so that might be something to closely watch…
More: Justice Department | TechCrunch | BBC News | @metacurity

Self-replicating 'supply chain' worm affects over 180 software packages
KrebsOnSecurity: And now we're back in the weird and wonderful world of the software supply chain, as this week saw a new password-stealing self-replicating worm spread through the npm software repository. At least 180 code packages were compromised by the so-called "Shai-Hulud" malware, named after the Dune sandworms, including at least two-dozen maintained by CrowdStrike, as well as other packages like tinycolor that are downloaded millions of times each week. The worm works by infecting packages then stealing any npm tokens it finds, compromising those packages, and then continues spreading on and on. This is the latest in a series of attacks in recent months targeting the software supply chain of late. While the Shai-Hulud strain appears to have waned in recent days, this sounds yet another fire alarm through the development community.
More: Bleeping Computer | Socket.dev | StepSecurity | UpGuard | Synack
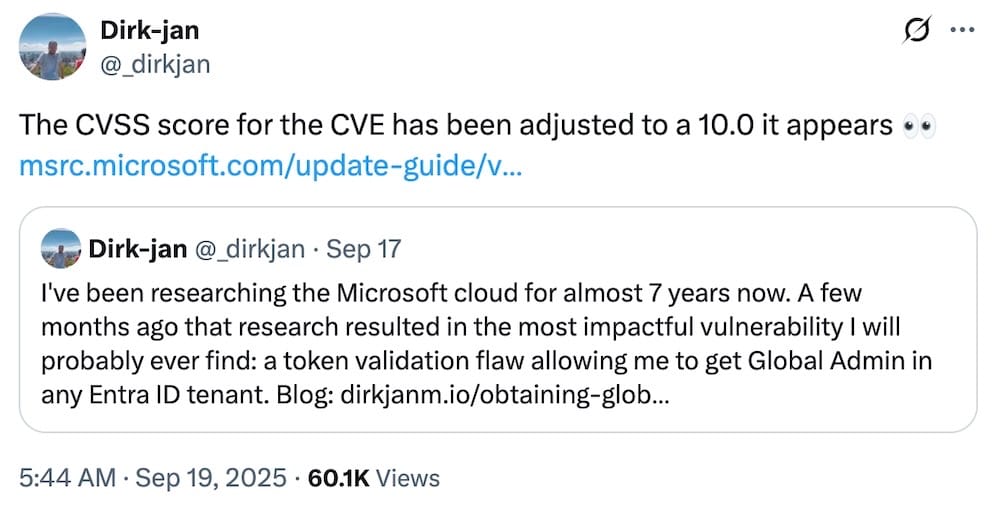
Entra bugs allowed access to 'virtually all Azure customer accounts'
Wired ($): Dirk-jan Mollema discovered a pair of severe security flaws in Entra ID, Microsoft's cloud-based identity and access tech, which allowed virtually unrestricted access to any Azure cloud customer account. Microsoft fixed the so-called bugs that allowed "god mode" access, which was eventually rated a maximum 10.0 in vulnerability severity. The bugs highlight once again the security of Microsoft's own security products, which it has faced a fair amount of scrutiny recently. The bugs are particularly concerning given that China, only a couple of years ago, hacked into Microsoft and had unfettered access to both consumer and enterprise customer emails thanks to the theft of a skeleton access key that should never have existed to begin with.
More: Microsoft | The Register | Dirk-jan Mollema | @_dirkjan
Cyberattack on airport check-in systems sparks delays across Europe
~this week in security~ ($): Several airports across Europe, including London's Heathrow, are facing continued delays and some flight cancellations after a cyberattack targeting aviation and defense contractor Collins Aerospace on Friday caused airline check-in systems to crash. Airline staff are manually checking-in travelers due to the outage, which is causing the bulk of the delays, as much of the automated systems are down. It's not yet clear if data was stolen in the "cyber-related disruption" as the company put it, but these systems do have access to quite a large amount of passengers' personal and travel records.
More: Reuters ($) | BBC News | The Journal | @HeathrowAirport
~ ~
THE STUFF YOU MIGHT'VE MISSED
Pilot aims to pair critical water facilities with cyber experts
NPR: NPR is on the ground at a water treatment facility in Vermont to look at the growing cyber threat facing the U.S. water supply system, much of it controlled by private industry. With hacks increasingly targeting water supply systems (also think Volt Typhoon), a new pilot called Project Franklin aims to help to link hackers and security researchers with critical infrastructure organizations to help support them with donated time and skills.
Learnings from hacking a cheap internet video camera
Joshua Kennedy: A security researcher wanted to remotely see what his dog was getting up at home while they were out of the house, so they bought a TP-Link internet video camera and "accidentally" (on purpose) found it contained a hardcoded default password, a big security no-no. Of course, what do you expect from a $20 camera on Amazon? Well that's the thing, we should expect better. The walk through is a fun read, and cute pup, too.

Flock cameras tracked driver hundreds of times over months
NBC News: Speaking of cameras… a local Norfolk, Virginia resident sued his city to find that the 176 license plate scanning cameras in his town supplied by surveillance giant Flock tracked him more than 500 times over a period of four months. That's roughly four license plate scans per day. The lawsuit puts scrutiny on the $2.2 million contract that the city of Norfolk signed with Flock (and any other city that Flock signs). As the EFF notes, it's "startling to see how many data points just driving your car through one city can add up to."
Courts' cyber clampdown is hampering public access
Court Watch: The excellent folks at Court Watch, who cover the world of legal news, blogged about their efforts to unseal a search warrant related to the murder of Charlie Kirk. They were successful in their efforts, though the unsealed case was entirely unrelated to Kirk's murder, such is the limited public nature of sealed documents. Per the writers: "And that’s the rub really, with the courts clamping down on providing access to sensitive cases after they got hacked, and a general vibe of courts of assuming that public records should not be read by the public itself, it’s a difficult time to try to find things that folks may or may not want to be found."
Google patches Chrome's sixth exploited zero-day of the year
Help Net Security: Google has patched its sixth exploited zero-day vulnerability this year, fixing a type confusion bug in the V8 JavaScript engine. The bug (CVE-2025-10585) was discovered by Google's Threat Analysis Group, which investigates government-backed threats (I'd bet $20 that this is somewhat spyware related). The Chrome bug also affects any other product that relies on the affected component, including Microsoft's Edge.
Artificial intelligence ushering in 'golden age' of hacking
Washington Post ($): The Post's @joemenn looks at how hackers are increasingly using AI to hack into their systems… but perhaps not in the way you're thinking. AI and "agentic" products that companies roll out internally and connect to their own systems, such as calendar assistants and other chatbots, can be tricked into granting malicious actors access to sensitive data. The Post's story is a good and fair overview of the general AI threat of today without overegging the pudding.
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. As a working journalist, I don't run ads or accept sponsors for this newsletter.
Please consider signing-up for a premium subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
OTHER NEWSY NUGGETS
Airlines feeding warrantless surveillance database: American Airlines, Delta, and United are among the many airlines collectively selling access to five billion plane tickets and flight itineraries to the U.S. government for surveillance, including ICE. The newly obtained documents reveal these records are updated daily and authorities can search the database by name, credit card, airline, and more. (via 404 Media ($))
U.S. has 70,000 cyber personnel: For the first time, the U.S. government confirms it has about 70,000 personnel (including contractors) across some 400 government organizations. This puts into perspective how big the U.S. cyber forces are; CYBERCOM makes up the majority of the government's cyber domain, and there's a fair amount of "unnecessary overlap" between the cyber orgs. (via GAO, Risky.biz)
American accused of Finnish therapy breach: One of the most damaging breaches in Finnish history was the theft of patient files from therapy service Vastaamo in 2020. The convicted hacker and smug jackass Aleksanteri Kivimäki was released earlier this month on appeal. But now, Finnish authorities say a second suspect, believed to be a U.S. national, was also involved in the breach. (via Finland National Prosecution Authority, The Record, @metacurity)
ShinyHunters nab 1.5B records in Drift heist: The hackers behind the recent mass data thefts targeting Salesforce databases of Salesloft Drift customers have taken more than 1.5 billion records from at least 760 companies. This makes the campaign one of, if not the biggest data breaches of the year. (via Bleeping Computer)
SonicWall breached, customers must reset creds: Some SonicWall customers are being told to reset their passwords after hackers broke into SonicWall's cloud backup service and stole customer firewall configuration files. Fewer than 5% of customers are affected (which still might amount to hundreds or thousands of customers). It's unclear how the crims got into SonicWall's systems to begin with. (via The Register, SonicWall)
~ ~
THE HAPPY CORNER
Let's switch gears and dial down the stress… we're entering the happy corner.
The age old movie classic Hackers came out this week 30 years ago. Unsurprisingly, we did get some nuggets of nostalgia. Some people ended up finding their careers, some found their significant others! And all that from a movie, who knew?
It's not every day that you see a cat with full bars of cell service.

For those who just love (to tease) their red teams, here's a phishy link generator for malicious-looking URLs that will almost guarantee to get their attention.
Excellent news on the release of Tails 7.0, one of the most private and secure operating systems going. To get started (and learn more) check out Privacy Guides, which — as an aside — is also a really top-notch website for advice and guidance on using privacy tech.
And finally, this week, some food for thought:
Good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Muffins, who can be seen here filtering all of the network traffic from their human's computer. A purrrr-fect cat-in-the-middle attack if I've ever seen one. Thanks so much to Tristan for sending in!

🐈 Send in your cyber cats! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a later newsletter!
~ ~
SUGGESTION BOX
And that's it for another week in cybersecurity! Thanks for joining me this in edition and your support. As always, it's hugely appreciated. I'll be back next week with your roundup from the past seven days and more.
Join me then! Until then, take it easy, enjoy the rest of your week.
See you next,
@zackwhittaker