this week in security — september 28 2025 edition
THIS WEEK, TL;DR
U.S. sounds alarm over Cisco zero-days used to hack federal agencies
CISA, Cybersecurity Dive: U.S. cybersecurity agency CISA sounded the alarm this week about a new "widespread" cyber campaign targeting zero-day flaws found in Cisco routers used across enterprises and governments. At least 10 organizations have been breached so far, including several federal agencies have been hacked, per CISA, with evidence that intrusions could date back as early as May. If this all sounds somewhat familiar, it's because Cisco said the hacks are an extension of the ArcaneDoor attack first disclosed in 2024, and allow for the compromise and theft of data from affected devices (and allow access to the wider network that these devices are supposed to protect). CISA ordered civilian federal agencies to patch their networks within 24 hours, or by Friday. Some are already linking the attacks to China, but it still looks early on attribution.
More: Cisco | NCSC | CISA | Washington Post ($) | SecurityWeek | The Register | HelpNetSecurity
Secret Service's SIM bank discoveries were likely cybercrime-related
Wired ($), Tedium: Well, this was embarrassing. Just ahead of the opening of the United Nations General Assembly, the U.S. Secret Service announced it broke up an "imminent telecommunications threat" in the New York tri-state area involving nation-state actors. Federal agents raided several locations containing thousands of SIM card banks concentrated "within 35 miles" of the U.N. The Secret Service claimed that the threat could've disabled cell towers by pummeling them with tons of data. But, much of the story fell apart after the cyber nerds turned up, like @tprophet, Robert Graham, and Tedium, who helped to explain things. What is far more likely is that these SIM farms were used for regular profit-driven cybercrime, such as spam, fraud (like ticket scalping), and SMS blasting, and not some bizarre scheme targeting the U.N.
More: Secret Service | Associated Press | Bloomberg ($) | 404 Media ($) | @malwaretech

European airport delays subside as ransomware suspect arrested
TechCrunch ($): Last week's cyberattack on Collins Aerospace, a provider of airport check-in systems across Europe, was confirmed ransomware after a man in his 40s from West Sussex in the U.K. was arrested in connection with the incident. (No further details on the suspect, but worth noting Collins has a large office nearby!) Much of the airline delays have subsided, with airports reporting a mix of delays and cancellations but with an anticipated recovery of Monday, according to Brussels Airport, one of the airports affected by the check-in system outage. While much of the real-world knock-on effects have returned to some normality, all eyes on whether any data was stolen in the incident, such as passenger flight records.
More: National Crime Agency | Reuters ($) | BBC News
U.K. government planning to roll out mandatory digital IDs for citizens
The Guardian ($): The U.K. government has revived a long but slow-running effort to introduce mandatory identity cards across the population, which was met with almost immediate repulsion and extreme tutting. The U.K. has long resisted national identity cards (while much of Europe has them) fearing surveillance, unnecessary data collection and tracking (as someone who grew up in the U.K. at the height of this during the first major attempt). The problem is that we actually know very little about the scheme so far, except that the U.K. government seems hellbent on rolling it out as mandatory for citizens to gain employment under the thinking this will counter illegal immigration. To no surprise, Brits are making their voices heard (and loudly) with now over 2.2 million signatures as of the time of writing this newsletter. That's nearly more than any other petition in U.K. history.
More: U.K. Petitions | Associated Press | @alexlomas
~ ~
THE STUFF YOU MIGHT'VE MISSED
Deep-dive on how Scattered Spider hackers made millions in ransoms
KrebsOnSecurity: @briankrebs dives into the back story and history of Thalha Jubair, 19, an alleged hacker who is believed to be a core member of the Scattered Spider group and was charged in the U.K. and U.S. last week. This timeline looks at the hackers' early days from selling access to tech companies on cybercrime forums to major hacks targeting the tech, insurance, and retail industries. Relatedly: The teenager who turned himself in to Las Vegas police last week is now charged with hacks thought to be relating to the 2023 breaches of MGM and Caesars, per the Las Vegas Review-Journal ($). The teenager, who was allegedly 15 years old at the time of the hacks, was released with conditions. This'll certainly be a legal case to watch.
How to think about surveillance under authoritarianism
Bruce Schneier: A sobering but important look at the state of surveillance from the perspective of security veteran Bruce Schneier (also in Lawfare) across the U.S., and practically what we need to know and what we can do about it. Awareness of your own threat model is important at a time when surveillance and our data are being actively used to harass, threaten, and persecute. Meanwhile: The EFF's @mguariglia has a Bluesky thread about spending a week at a police convention and his biggest takeaway was how companies are collecting and consolidating as much data as possible.
Microsoft 'disables' surveillance tech used by Israeli military
The Guardian ($): Speaking of surveillance, Microsoft has pulled the plug on allowing the Israeli military to store vast amounts of surveilled Palestinians' communications data in its Azure cloud. The Guardian first revealed that Microsoft CEO Satya Nadella signed off on the Israeli surveillance program back in 2021, allowing the Israeli military to "collect, play back and analyse the content of cellular calls of an entire population." (Side note: reminds me a little of NSA's MYSTIC program targeting the Bahamas and other countries.) You can read Microsoft's explanation here.
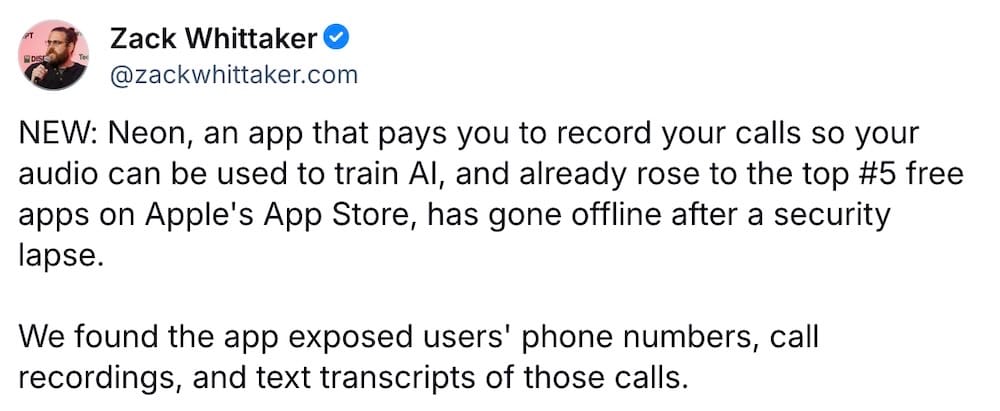
Viral call recording app Neon goes dark after exposing user data
TechCrunch ($): An app called Neon, which launched this week and shot to the top of the Apple App Store charts, offers to pay users to record their calls so their audio can be used to train AI models (don't even get me started, I can't). Just one major problem: the app was spilling thousands of the users' phone numbers, call recording audio, and text transcripts of those calls. I dug into the app and found the flaw, and wrote about it for TechCrunch with @sarahp. (Disclosure alert!)
Suspected Chinese hackers behind backdoor break-ins at legal firms
Google Threat Intelligence: In an entirely separate campaign thought to be linked to China, Google's security researchers say they've seen evidence of a Linux backdoor called BRICKSTORM being used to maintain persistent access to U.S. victim networks, many in the legal sector (think lawyers and incident responders) and IT outsourcers. The hackers are targeting these organizations because of the rich access they have to sensitive data and systems. Luckily, Google built a scanner for you to check your org. More from The Register.
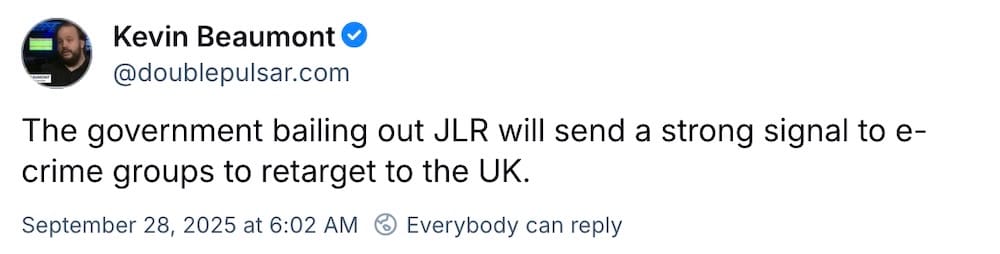
U.K. to bail out Jaguar Land Rover with loan after cyberattack
BBC News: The U.K. government will bail out automaking giant Jaguar Land Rover (owned by Tata, one of the richest companies in the world) after its cyberattack wiped out much of its network and stalled car production for weeks. The £1.6bn ($2bn) government loan will cover employee paychecks and affected downstream suppliers. JLR doesn't have cyber insurance, per Sky News. It makes sense to see the U.K. government step in here (even if it was necessary for the U.K.'s economic security), but this looks like Tata's security failings and profit-driving coming to light. Bailing out JLR on the short-term isn't going to fix the underlying and long-term cybercrime and ransomware problem.
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. As a working journalist, I don't run ads or accept sponsors for this newsletter.
Please consider signing-up for a premium subscription starting at $10/month for exclusive articles, analysis, and more.
~ ~
OTHER NEWSY NUGGETS
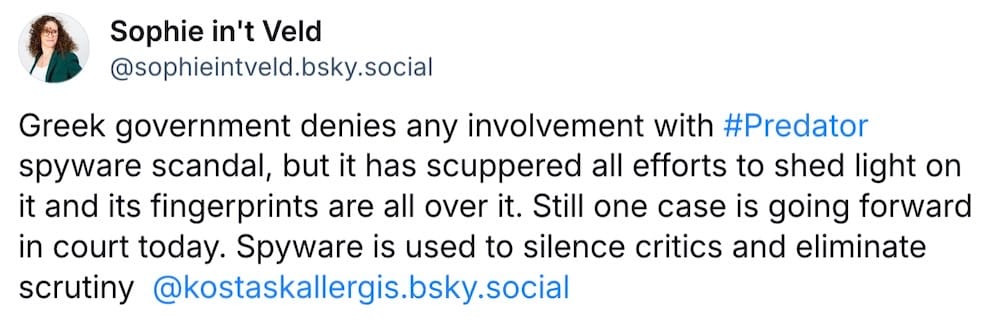
'Greek Watergate' legal case can proceed: A legal case in Greece involving the government's alleged use of spyware to Predator spyware to snoop on the phones of government ministers, military officials, and journalists can move ahead. Critics have accused the Greek government of trying to cover up the scandal, which saw at least 87 people's phones hacked. (via BBC News, @sophieintveld)
Federal agency popped with GeoServer bug: Not to be outdone by the Cisco zero-day, CISA said separately this week that a bug found in an unpatched GeoServer server, an open-source product used for sharing geospatial data, was exploited to hack into an unnamed federal agency's network. CISA does a grand job of laying out the lessons it learned after being called in to clean-up the hack. (via CISA, Bleeping Computer)
Stellantis breach affects millions of customers: Stellantis, the car making giant behind popular vehicle brands like Jeep and Fiat, had one of its Salesforce customer databases raided. The ShinyHunters hacking group claimed responsibility for the hack, per Bleeping Computer and DataBreaches.net. The hackers said they stole 18 million lines of customer records. (via Stellantis)
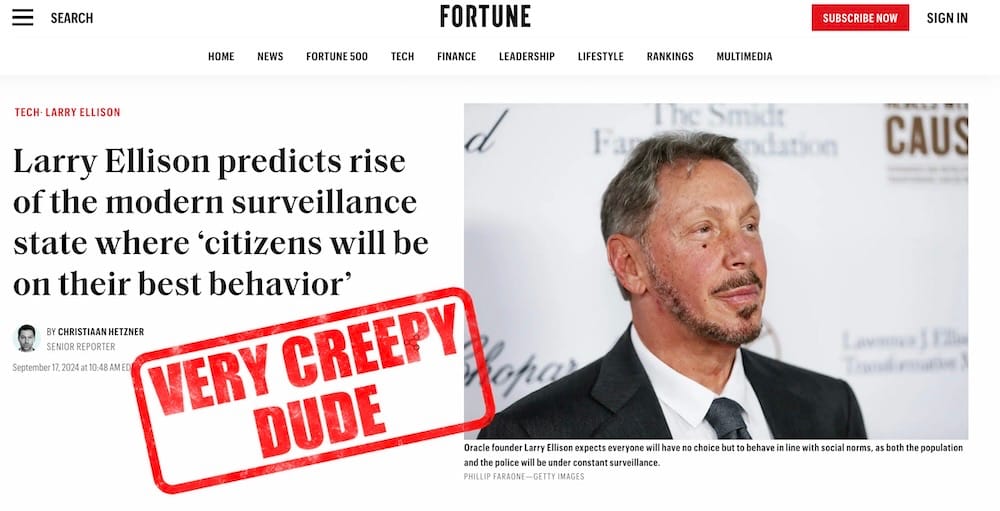
TikTok set for U.S. ownership: Remember how TikTok was to be banned over fears that China could use the algorithm to manipulate entire populations? The Trump administration says under a new shakedown deal to avoid a ban, U.S. cloud giant Oracle will get to store all U.S. user data on its servers and the TikTok algorithm will be retrained and operated from the U.S. But as the EFF points out: "People can now be concerned that TikTok could be a conduit for U.S. government propaganda." Well, yeah! Not sure how that's all going to square when we have headlines like this from none other than… Oracle's chairman Larry Ellison. This is such a creepy and weird thing to say! (via The Register, EFF)
Nation-state exploiting Libraesva zero-day: A zero-day flaw in Libraesva, an email security gateway product used by at least 200,000 enterprises around the world, has been exploited by "hostile" state-backed hackers, according to a Libraesva security bulletin. The email product is used to protect email users from phishing and other security threats. The bug can be triggered by sending an email with maliciously crafted attachments. (via Libraesva, SecurityWeek)
Gov't shutdown threatens cyber-sharing law: The 2015 law that allows government and private industry to share cyber threat intelligence with each other may end up expiring as a result of an anticipated U.S. government shutdown expected this week. Critics say the law expiring would drastically reduce the amount of information shared, almost to the point of eliminating it. (via The Register, Cyberscoop)
~ ~
THE HAPPY CORNER
OK, that's enough of this week's doom and gloom, smash the "keep it light" button!

Go grab some popcorn and an oversized soda, it's movie night in the happy corner.
*dims the lights* Thanks to @phranck this week, we've got a bunch of hacker and cyber-related documentaries to enjoy. And there's a bunch more hacker movies to check out, thanks to the good work of @realhackhistory:
Meanwhile, for those who just want a bit of peace and quiet for a good read, you'll be thrilled with this 1,600-word BBC feature piece on the origins of the @-sign.
For those who want to harden their iPhones from security and privacy threats, @sambowne re-upped this iOS Hardening Guide for locking down your privacy and security settings. (It's incredibly detailed, so those who are more at risk should take note.)
Thanks to @wendynather for the nostalgic blast from the past. I'm old enough that I can actually hear this picture. (If you know, you know. And if you're under the age of 35, you probably won't.)

And finally, this week, a moment of peace:

Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Cali (short for Calabaza, or "pumpkin" in Spanish, I am reliably told). Her human tells me that Cali is a Colombian street cat who they have since adopted. With enchanting eyes like those, who needs zero-days or hacking tools when you would just willingly give over your passwords... Thanks so much to Blazej for sending in!

🐈 Send in your cyber cats (or friends!) 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name, and they will be featured in a future newsletter! (Sent in before? Drop in an update!)
~ ~
SUGGESTION BOX
OK, that was admittedly quite a lot this week and pretty heavy stuff, so thanks for bearing with me and the ongoing fustercluck of news.
I'll be back next Sunday with your usual round-up of the week in cyber, privacy, breaches, leaks, spills, 'sploits, and more. Thanks so much for reading this newsletter and being on this ongoing cyber journey with me.
Onwards to a better week!
Your cyber friend,
@zackwhittaker